
A few days ago we published an article on the new cybergang 8Base. 8base define themselves as “honest and simple pentesters. We offer companies the most loyal conditions for returning their data”. As RHC, we contacted them, and their approach immediately appeared different to other gangs.
At our first contact to request an interview, the first thing that they replied with was “Dear friends, fortunately we are not rock stars, and do not give interviews, for the simple reason that we have nothing to be particularly proud of”. This response is completely divergent in respect to other interviews that we have conducted where self-celebration is often a must.
They went on to report “we see security flaws in corporate networks and we use them. You can send your questions for review, but not count on the fact that you will receive responses, because as we have said, we are not rock stars.”. We accepted the challenge and in the end we managed to succeed.
We present to you the full interview held with an group that is developing their business in a different way compared to other cybercrime gangs. Their business is oriented more towards an “unrequested security audit” against companies that, most likely, are not even aware of what a security audit entails.
RHC: Hi guys, thank you for giving us this interview. Our first question is purely out of curiosity – is 8Base a name without specific meaning, or is there some significance behind it?
8Base: Hello, absolutely no difference
RHC: After our first message to request an interview, you said to us that you are not rock stars and that there is nothing to be particularly proud of regarding what you do. Could you expand more on what you meant with that statement?
8Base: We are simple honest pentesters, that’s all the explanation
RHC: We know that you are a pentesting group and that you can do it differently to others. Likely, aside from the financial motivation, there also seems to be an interest in improving the security of corporate IT infrastructure. Additionally, as we understand from your words, if you earn something at “honest” prices it is better for all. What could be a strategy to adopt to make these companies understand that the life of their own business is at risk, without going beyond into cybercrime?
8Base: Perhaps they should consider recruiting more qualified personnel for the post of system administrators.
RHC: We also conduct penetration testing and very often we find completely disastrous situations. Systems at end-of-support, predictable/trivial passwords, or even worse default passwords, critical patches never installed and hardening measures never executed. However, in your opinion, how are small and medium companies placed in terms of cyber security?
8Base: All companies have the same mistakes. The problem is in the education of system administrators and not in companies.
RHC: The great Bruce Schneier once said “I am regularly asked what the average Internet user can do to ensure his security. My first answer is usually ‘Nothing; you’re screwed’.” In your opinion has it truly come to this, or can there be some unconventional ways, still only lightly explored, to increase people’s knowledge of cyber risk?
8Base: We don’t know, you just need to be attentive to details.
RHC: We in Italy are not well positioned in terms of cyber security, and we have seen that you have hit some Italian organisations. In respect to other organisations in different parts of the world, how did you find the IT infrastructure of the Italian organisations? Better, worse, or in-line?
8Base: All companies have the same mistakes. The problem is in the education of system administrators and not in companies.
RHC: An analysis by VMware researchers has reported that your group may have been born from an offshoot of RansomHouse. In fact, the ransom notes are very similar and even some other small details. If you are able to comment, what do you think of this statement?
8Base: This is their job – let them compare.
RHC: The following, within your Terms of Service, is very interesting: “A list of information security recommendations will be provided to the head of the company”. What does this report consist of? Is this a penetration test report where in addition to the vulnerabilities, the attack vectors used are also highlighted? Do they ever ask you for more details or do the companies accept everything that you write?
8Base: When it comes down to it, there are companies that are interested, and there are those who just need us to delete their data from our servers and decrypt the files.
RHC: Another interesting thing is the next point: “Current vulnerabilities will never be used by the team for further attacks. In case new vulnerabilities will be discovered, the company will be notified”. In this case, if the company has paid the ransom do you follow up the specifics in their infrastructure? How does this particular model work?
8Base: It all depends on the holes left in these companies, if they cover them, then we leave the company without attention.
RHC: Considering your organisation with “educational” purposes, after each hit do you intend to demonstrate and/or state the timeline of an attack? In terms of awareness and with the view of “Lessons Learned”, reporting how companies are being breached allows others to increase their own defences. As such, do you have intentions to demonstrate the weak points of each company that is hit and to show the kill chain that was used, perhaps after a ransom is not paid?
8Base: No, if the company paid for our services, then no information from our correspondence with it will leak anywhere.
RHC: In an old interview with the Everest group, we were told that the group themselves sometimes thought about returning to being White Hat hackers. Have you ever thought about this or is it something that does not inspire you at this point? In terms of cybercrime, why is it better than ethical hacking today? Many bug hunters these days make a lot of money on some well-known bug hunting platforms.
8Base: The problem is that it is easier for a company to pay after problems have been caused. Because if we examine the company for errors in the settings and let them know about it, they will just send us. These are the realities.
RHC: So far we have seen that your group has launched attacks using documented security flaws. Do you have internal bug hunting programs planned to discover zero-day vulnerabilities to then use, such as for example how CL0P or REvil did with the Kaseya ransomware attack?
8Base: Follow the site, perhaps there will be an answer to your question.
RHC: Some reports released early this year reported a drastic drop in ransom payments in ransomware operations. Your group was formed in this period. The victims published on your data leak site (DLS) are those that do not pay the ransom. What is the actual percentage today of organisations that do pay the ransoms in your experience?
8Base: A difficult question, it all depends on the quality of the work done.
RHC: You are a Ransomware-as-a-Service (RaaS) program. How many affiliated groups do you manage currently? Do you plan to become as big as LockBit or Conti?
8Base: We do not have and will not have child groups, we work independently. Less people means less problems.
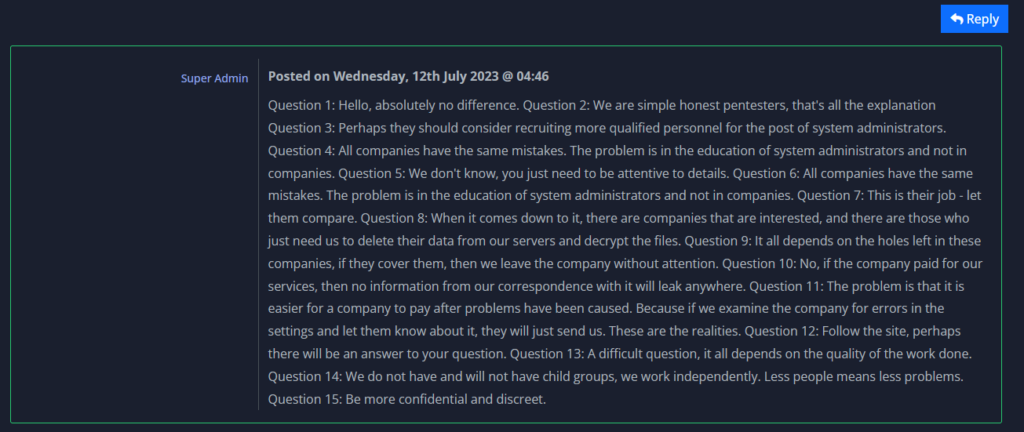
RHC: Thank you for having responded to us, and we would like to ask if there is anything that you want to report to our readers.
8Base: Be more confidential and discreet.
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
