
Capire davvero cos’è il ransomware non è semplice: tra notizie frammentate e articoli tecnici, chi cerca risposte rischia di perdersi in un mare di informazioni confuse. Questo articolo nasce per fare chiarezza, offrendo una spiegazione completa e accessibile di come funziona il ransomware e del mondo criminale che lo alimenta.
Negli ultimi anni le cronache sono piene di notizie su grandi violazioni informatiche, riscatti milionari, gang cybercriminali, servizi di RaaS (Ransomware-as-a-Service) e perfino presunti conflitti cibernetici tra bande criminali. Per chi non lavora nel settore della sicurezza, termini come questi possono risultare oscuri e generare confusione. In questo articolo spiegheremo che cos’è il ransomware e come funziona il business — altamente redditizio — del crimine informatico organizzato. Offriremo un’analisi completa: partiremo dal modello di “affiliazione” e proseguiremo descrivendo tecniche, tattiche di attacco e metodi di estorsione usati dagli operatori del fenomeno.
Nell’immaginario popolare, si pensa che la criminalità informatica sia legata a singoli individui con abilità informatiche eccezionali. Ma se vuoi estorcere milioni di dollari a una grande azienda, non puoi fare tutto da solo, hai bisogno di una “squadra”, ovvero: Un gruppo di hacker criminali con competenze informatiche diversificate, avanzate e verticali, che frequentano il Dark Web e che con molta probabilità vivono in Russia.
Infatti, la stragrande maggioranza dei criminali informatici non dispone di tutte le capacità tecniche necessarie per fare da soli e quindi creare malware, estorcere denaro, penetrare le aziende. Ecco appunto che nasce la RaaS, la Ransowmare as a Service, dei criminali informatici che collaborano in modo “organizzato”, per un unico scopo: estorcere tanto più denaro possibile ad una ipotetica organizzazione.
La criminalità informatica è esplosa negli ultimi anni perché i criminali si sono “specializzati” e “sotto-specializzati” in modo che ognuno potesse concentrarsi su un determinato obiettivo, su una singola fase del processo di violazione ed estorsione e tutto questo funziona terribilmente (purtroppo) bene.
Per RaaS, come abbiamo detto, si intende “Ransomware as a Service”, quindi Ransomware come “servizio”, un modello di business criminale dove la violazione viene condotta da un gruppo di criminali informatici militarmente organizzati. Ora analizzeremo questa piramide a tre livelli, per comprendere al meglio il suo funzionamento e la divisione dei compiti tra i criminali informatici.
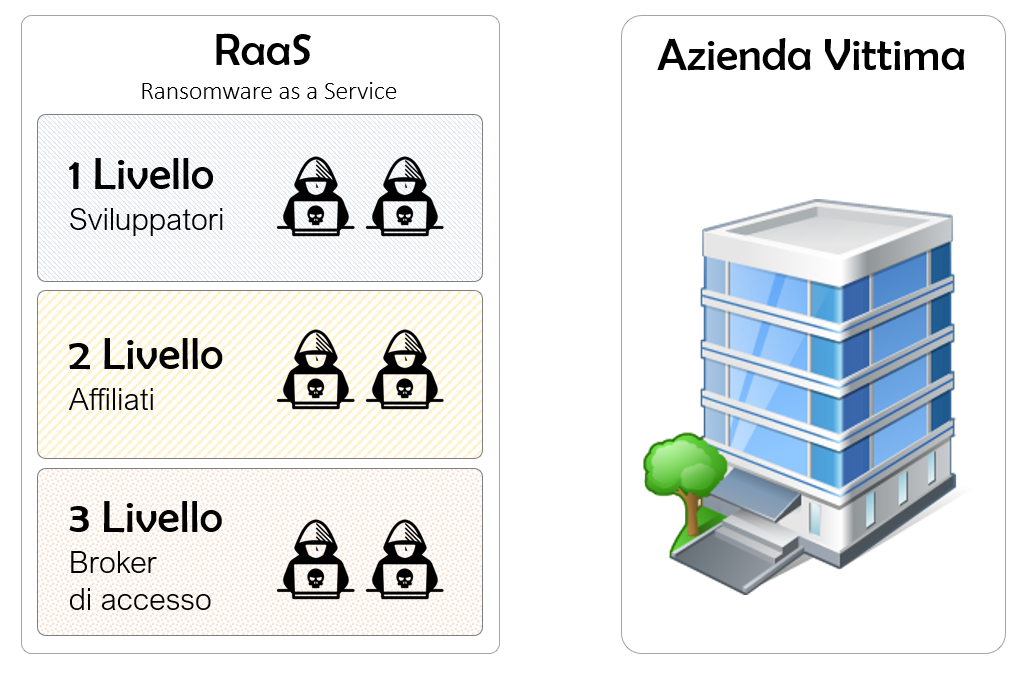
Al primo livello troviamo gli “Sviluppatori“. Si tratta di esperti nella scrittura dei malware, di crittografia, che li realizzano, li aggiornano continuamente, creano strumenti per poter fornire sviluppate dashboard e sistemi di comando e controllo agli “affiliati“, capaci di gestire tutta la fase di infezione, che come vedremo è la fase ultima “attiva” di un attacco ransomware, prima di passare all’estorsione. Gli sviluppatori mettono a disposizione anche degli strumenti di supporto tecnico per gli affiliati, in modo che questi possano avere delle risposte immediate dagli sviluppatori su problematiche tecniche.
Al secondo livello abbiamo gli “Affiliati”. Si tratta di altri criminali informatici che affittano il ransomware dagli sviluppatori e conducono la reale attività di attacco e di estorsione, accedendo alle reti della vittima e rimangono al suo interno per molto tempo, esfiltrando quanti più dati sensibili che gli consentiranno un ulteriore livello di persuasione nel caso in cui l’azienda non vorrà pagare la richiesta di riscatto, che vedremo nel secondo articolo.
Gli affiliati, quindi, affittano il ransomware dagli sviluppatori, accettando o concordando le provvigioni all’interno di forum underground chiusi (come i forum nelle darknet su presentazione), ma anche su forum accessibili presenti nel clearweb, come ad esempio il noto XSS.is.
Gli affiliati, in molti casi, per poter accedere ad una rete di una grande azienda, possono acquistare l’accesso dalla terza e ultima entità nella piramide RaaS, ovvero i broker di accesso.
Questi ultimi, sono di fatto dei gruppi di criminali informatici che violano le reti delle azienda per acquisirne persistenza. Sono molto esperti di tecniche di penetration test e, una volta acquisito l’accesso alla rete di una grande organizzazione, la mettono in vendita nei forum underground per poche migliaia di dollari. Gli affiliati, spesso sono clienti dei broker di accesso, in quanto consentono di velocizzare il loro flusso di lavoro, mettendo loro a disposizione accessi illeciti già verificati e disponibili e a basso costo.
Ovviamente la RaaS esiste quando c’è una organizzazione da violare. Questa organizzazione normalmente ha endpoint esposti su internet non correttamente configurati o aggiornati, che permettono ai broker di accesso di accedere all’interno delle loro reti.
Queste aziende spesso vengono identificate attraverso motori di ricerca quali Shodan, Zoomeye, Censys, IVRE che permettono di individuare con facilità le risorse esposte su internet di una organizzazione e le relative vulnerabilità esposte. Come spesso abbiamo detto, la RaaS non ha come obiettivo una specifica azienda, spesso colpisce una grande azienda, solo perché lascia una firma “indelebile” sul web delle sue intrinseche vulnerabilità dovute ad una errata postura cyber al suo interno.
Ora che abbiamo scoperto tutti gli attori nel grande gioco del RaaS, ci addentreremo sul modello di attacco e quindi scopriremo le modalità di iterazione tra i tre livelli del RaaS. Ma per prima cosa iniziamo a mostrarvi la grafica numerata del percorso di attacco per semplificarci la lettura.
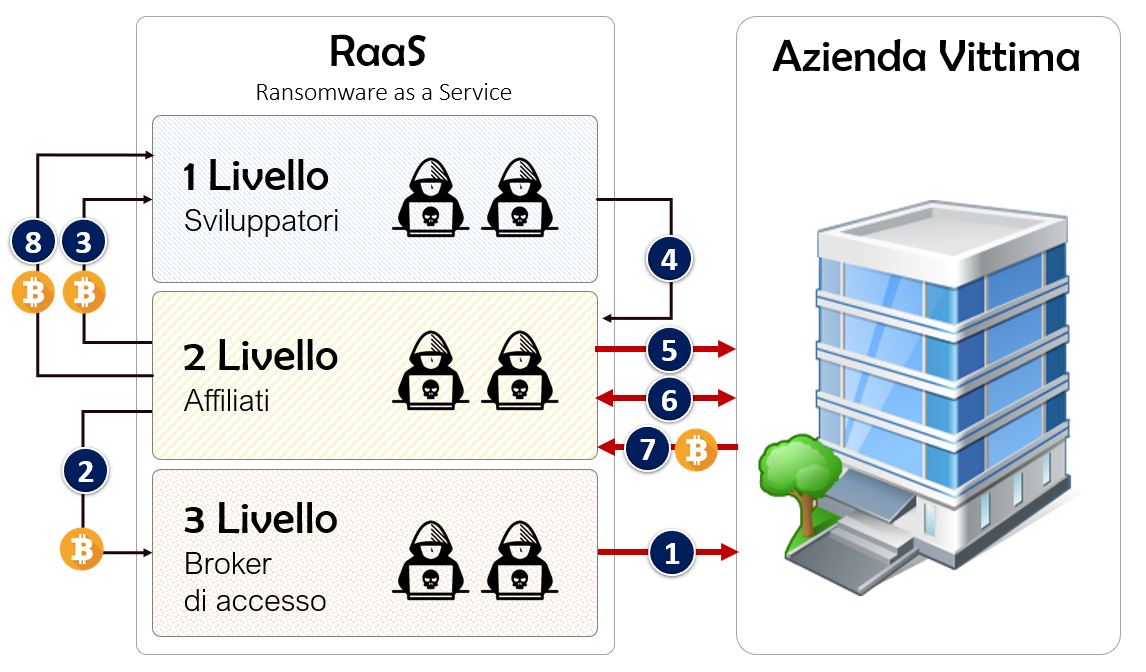
Ora comprenderemo con precisione tutti i passi che vengono effettuati in questa perfetta e militare organizzazione criminale che consentirà, qualora il tutto funzioni a dovere di estorcere grandissime quantità di denaro.
Qualsiasi pagamento di riscatto effettuato da una vittima viene suddiviso tra l’affiliato e lo sviluppatore del ransomware. Nel caso di DarkSide (il ransomware che ha bloccato Colonial Pipeline), lo sviluppatore del malware prendeva il 25% per riscatti inferiori a 500.000 dollari, ma tali provvigioni scendevano al 10% per riscatti superiori a 5 milioni di dollari.
Tutto questo viene definito con delle politiche descritte nei blog degli “sviluppatori” o nei forum underground come ad esempio XSS del quale abbiamo parlato molto di recente. Questa divisione dei pagamenti dei riscatti risulta molto chiara da vedere sulle blockchain, con le diverse azioni che separano i portafogli Bitcoin controllati dagli affiliati e dallo sviluppatore.
Se parliamo di DarkSide, lo sviluppatore ha ricevuto bitcoin per un valore di 15,5 milioni di dollari (17%), con i restanti 74,7 milioni di dollari (83%) destinati ai vari affiliati.
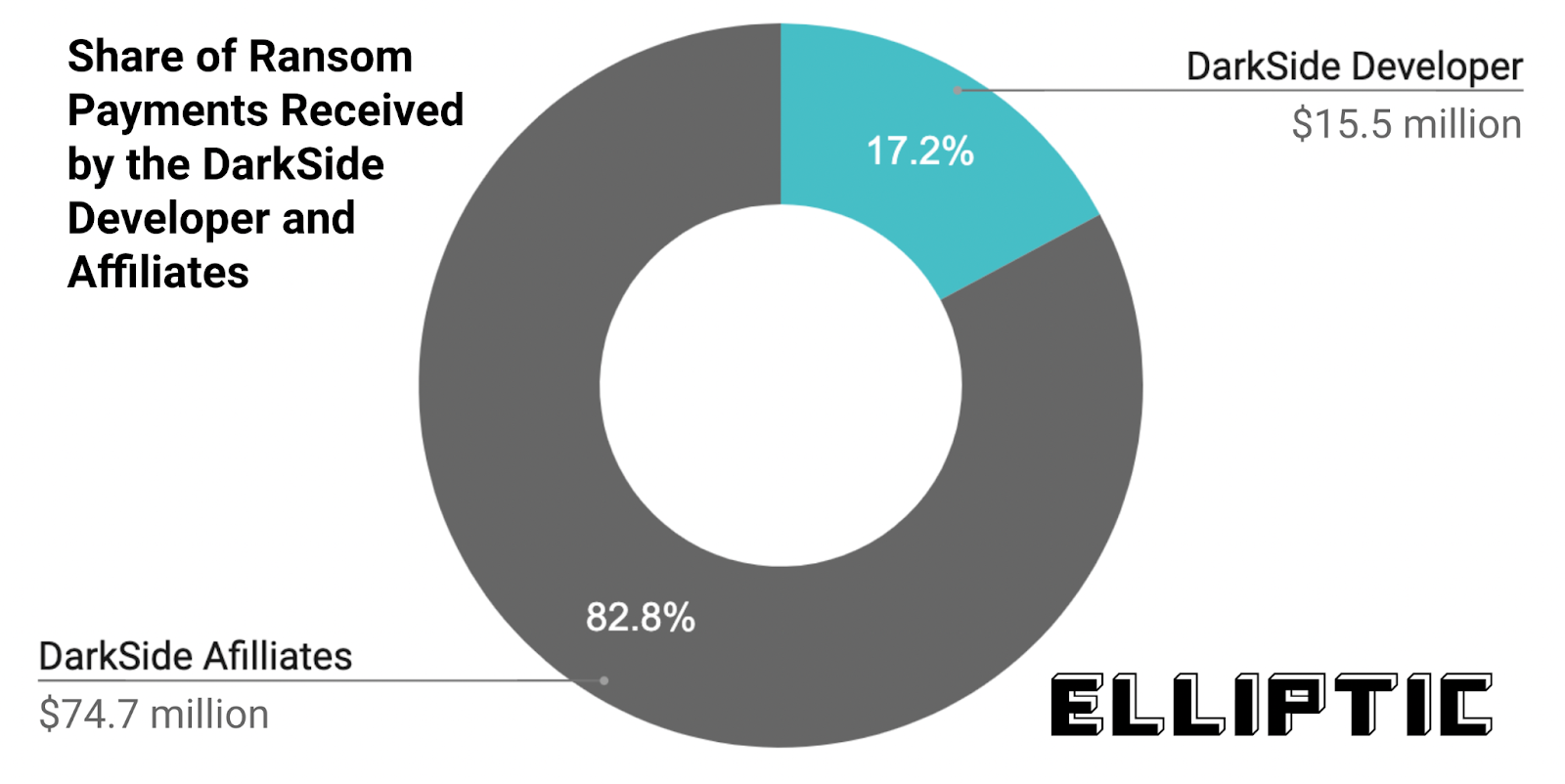
In totale, a DarkSide sono stati effettuati poco più di 90 milioni di dollari in pagamenti di riscatto in bitcoin, provenienti da 47 portafogli distinti.
Questo fa comprendere con relativa precisione il numero di vittime violate che hanno pagato un riscatto. Ad esempio, secondo DarkTracer, 99 organizzazioni sono state infettate dal malware DarkSide, suggerendo che circa il 47% delle vittime ha pagato un riscatto e che il pagamento medio era pari a 1,9 milioni di dollari.
Come abbiamo visto, la RaaS ruota principalmente attorno a “sviluppatori” ed “affiliati”, ma esistono anche altre figure che mano a mano stanno prendendo forma facendo divenire la RaaS una vera e propria organizzazione aziendale, con ruoli diversificati e molteplici attività di outsourcing.
I criminali informatici che sviluppano infrastrutture che vengono rivendute agli sviluppatori di Ransomware per velocizzare il loro ciclo di sviluppo del software, come ad esempio i sistemi di pagamento in criptovaluta, i blog, e così via.
Si tratta a tutti gli effetti di componenti software criminali, che vengono acquistate dagli sviluppatori di ransomware che utilizzano all’interno delle loro soluzioni, esattamente come si stesse progettando un software lecito, utilizzano software di terze parti.
Per poter massimizzare il profitto in situazioni nelle quali le aziende sono reticenti a pagare il riscatto e per massimizzare gli sforzi messi in atto per violare e crittografare una determinata azienda, la RaaS può avvalersi su persone specializzate nella gestione dei “negoziati” tra l’azienda violata e il gruppo RaaS.
Infatti, diversi attori si stanno avvalendo di figure che gestiscono l’aspetto della negoziazione, oltre ad accumulare pressione verso l’azienda, ad esempio tramite chiamate, attacchi DDoS (Distributed Denial-of-Service) e minacce tra cui la perdita di informazioni rubate durante un l’attacco ransomware, insomma delle persone specializzate in pura “estorsione”, che possano facilitare l’attività di pagamento da parte dell’azienda.
Il ransomware non è rimasto immutato dalla sua comparsa. Si può tracciare una linea che parte dal primo caso noto — il Trojan AIDS di Joseph Popp — e arriva ai casi più recenti e sofisticati come WannaCry, Maze, REvil e DarkSide. Nel tempo sono cambiate le capacità tecniche dei malware, ma soprattutto si sono evolute le strategie di ricatto: i gruppi criminali hanno trasformato l’attacco informatico in un modello economico sempre più articolato e remunerativo.
Per comprendere l’attuale panorama, è utile distinguere tre principali tattiche di estorsione che si sono affermate progressivamente.
L’aggiunta di più livelli estorsivi ha trasformato il ransomware da semplice strumento tecnico a leva strategica multifattoriale: la vittima affronta non solo il blocco operativo, ma anche possibili danni legali, perdite di clienti e un danno d’immagine difficile da quantificare. Per questo motivo molte imprese oggi non considerano più i backup come unica difesa, ma integrano misure di risposta che contemplano anche la gestione della comunicazione, la negoziazione e il coinvolgimento di consulenti legali e specialisti in incident response.
Come abbiamo visto, i “broker di accesso”, hanno grandi capacità tecniche offensive, capaci di violare una organizzazione, pertanto a loro spetta il compito di penetrare il sistema dell’azienda e rivendere i punti di accesso agli “Affiliati”, che rimarranno all’interno delle reti fino a quando non avranno trovato dei dati tendenzialmente sensibili, capaci di ricattare la vittima attraverso la doppia estorsione, modalità introdotta da Maze (una cyber-gang ad oggi non più attiva) a fine del 2019.
Tutti sembrano concordare sul fatto che le tattiche, le tecniche e le procedure utilizzate dagli “affiliati” e dai “broker di accesso”, riflettono un modo di azione comune che incorpora un mix di funzionalità native di Windows , malware commodity e strumenti di red team pronti all’uso come Cobalt Strike, Mimikatz, powershell e backdoor .NET.
I “broker di accesso” infatti, hanno buone competenze nelle attività di penetration-test mentre gli “affiliati”, si muovono lateralmente per accedere alle infrastrutture che contengono i dati più preziosi, come ad esempi i reparti di ricerca e sviluppo, il reparto di finanza e controllo oppure l’ufficio Human Resource, con l’intento di prelevare quante più informazioni “sensibili” dall’organizzazione.
Una volta stabilita la persistenza, la banda criminale può rimanere all’interno di una organizzazione anche per 45 giorni, ma è noto che il numero dei giorni può arrivare fino a 90 (quindi 3 mesi, che di fatto possiamo paragonarlo ad un attacco APT, un Advanced persistent threat), e solo dopo aver prelevato quante più informazioni possibili utili alla seconda estorsione, avviano il payload del ransomware.
Dobbiamo quindi comprendere che il momento in cui viene percepito l’attacco informatico da parte degli utenti (qualora non sia stato rilevato un accesso in precedenza), è la fine del lavoro “tecnico”, svolto dai criminali informatici.
Il ransomware, a questo punto effettua il suo lavoro, cifra i dati presenti all’interno dei server e mostra a video un programma che riporta che il computer è stato infettato, il prezzo per decifrare i dati e il tempo entro quando occorrerà pagare il riscatto. Nel caso di Ransomware come REvil (Sodinokibi), passato quel periodo, la cyber-gang raddoppia il costo del riscatto.
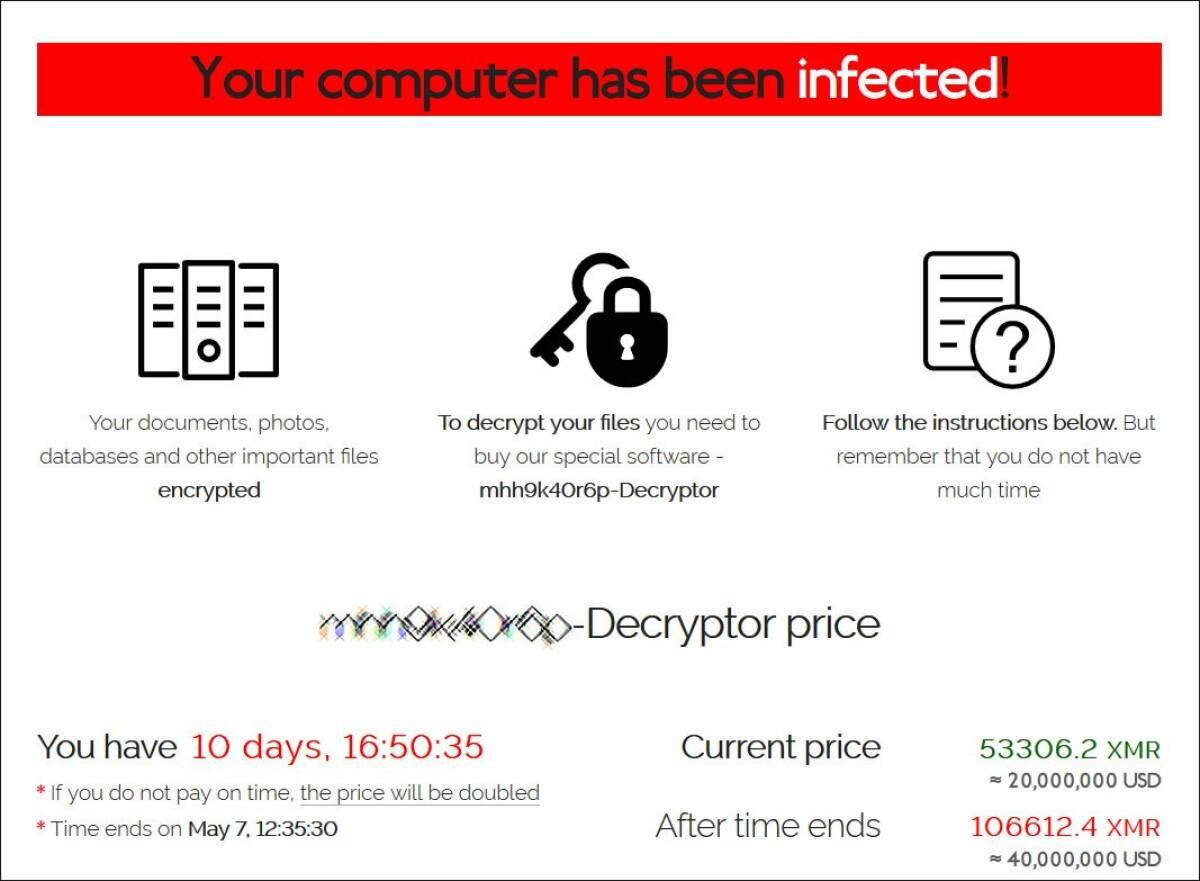
Schermata di blocco del ransomware REvil (Sodinokibi)
Inoltre viene prodotto un file (anche se sono molteplici le forme di azione), dove viene scritto cosa dovrà fare l’organizzazione per ottenere la chiave di cifratura che gli consentirà la decifrazione dei dati. Nello specifico viene riportato di “non perdere tempo”.
Vengono inoltre riportate le istruzioni per accedere al sito nella rete onion in totale sicurezza, specificando che è consigliato l’utilizzo di una VPN e di TOR browser. Una volta acceduto con TOR al sito .onion, occorrerà specificare un codice generalmente visualizzato dal programma sullo schermo del computer e quindi procedere con il pagamento del riscatto.
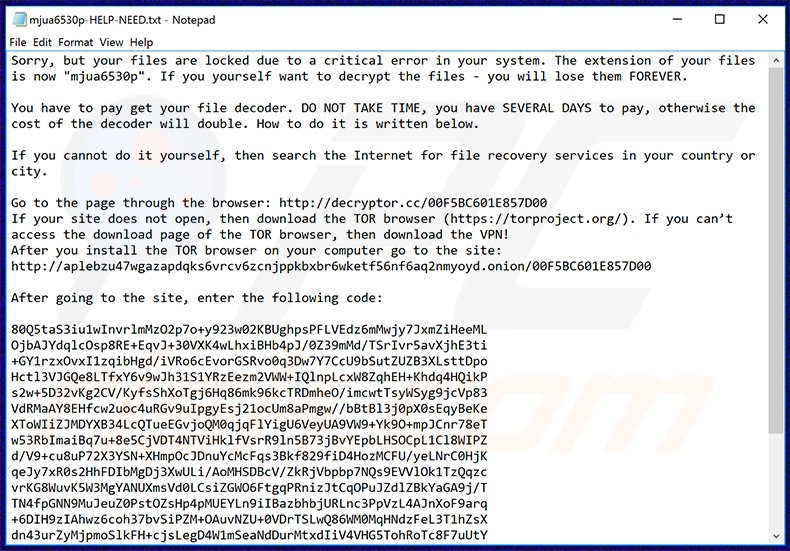
File di testo che riporta le istruzione di recupero.
Di recente sono state osservate una moltitudine di nuove tecniche di estorsione, capaci di aumentare la pressione verso l’organizzazione e quindi indurla a pagare il riscatto.
Ad esempio, nell’incidente subito dalla Vastaamo (una clinica psichiatrica finlandese), dopo aver cifrato i dati, gli affiliati hanno proceduto ad informare i suoi clienti che i dati delle loro cartelle cliniche sarebbero stati resi pubblici. Infatti 300 cartelle cliniche vennero pubblicate nel darweb e l’azienda fallì.
In altri casi, si è assistito a delle telefonate da parte degli affiliati verso i giornalisti per informarli che una determinata organizzazione è stata colpita da un ransomware, aumentando di fatto la circolazione delle notizie e quindi la pressione sulle organizzazioni.
In altri casi si è assistito anche a delle pressioni fatte verso i top manager delle aziende minacciandoli di pubblicare informazioni sensibili prelevate dai loro stessi pc, questo mentre l’azienda stava valutando il pagamento del riscatto del ransomware.
Un altro esempio davvero folle riportato da Mandiant, è relativo ad un affiliato di DarkSide, che era stato in grado di esfiltrare la polizza assicurativa informatica dell’azienda. Queste informazioni sono state ovviamente sfruttate dalla cyber-gang durante il processo di negoziazione del riscatto, rifiutandosi di ridurre l’importo, data la sua conoscenza dei limiti della previsti dalla polizza.
L’arte dell’inganno è sempre stata alla base delle attività di criminalità informatica a tutti i livelli, tanto è vero che molti libri sono stati scritti sulle tecniche di spoofing e di deception, e quindi su come ingannare gli altri a far credere di essere attaccati da un altro soggetto.
Determinare per quale paese o governo le cyber-gang possono lavorare è diventato molto difficile da comprendere negli ultimi anni, dal momento che molti gruppi cercano specificamente di lasciare delle “tracce”, per incastrare altri paesi o governi.
I codici da soli non sono sufficienti per identificare la nazionalità degli aggressori, poiché i criminali informatici possono lasciare deliberatamente false tracce, quelle che in gergo militare vengono chiamate delle false bandiere o “false flag”.
Per “false flag”, si indica una tattica segreta perseguita nelle operazioni militari, attività di intelligence e/o di spionaggio, condotte generalmente da governi, servizi segreti, progettata per apparire come perseguita da altri enti e organizzazioni, anche attraverso l’infiltrazione o lo spionaggio all’interno di questi ultimi.
Questo si legge su wikipedia come “concetto militare”, e questo ovviamente è stato acquisito e messo in atto nella guerra informatica e nelle operazioni ransomware inserendo all’interno dei malware delle specifiche “tracce”, capaci di influenzare un analista nel far dedurre, in maniera errata, l’origine di un attacco ransomware.
Il russo risulta una lingua utilizzata in molti paesi dell’ex URSS, specialmente nel campo della tecnologia informatica, pertanto oggi potrebbe essere abbastanza complicato trarre delle conclusioni sull’impronta del malware attraverso commenti, messaggi di errore, restrizioni su base linguaggio/paese, gli IP Address dei sistemi di command and control e altro ancora.
Molti gruppi che lavorano per i governi di vari paesi, stanno specificamente cercando di lasciare degli artefatti nel codice appositamente forgiati per depistare gli analisti dalle loro vere identità e paesi di provenienza.
Sono tecniche di imitazione per far credere che l’attacco sia stato sferrato da un gruppo di un altro stato, oppure simulare ed impersonare precisamente un attore di minaccia noto, per depistare le loro tracce. Molti gruppi hanno analizzato i malware di altri concorrenti, per riportare all’interno dei loro file binari, degli artefatti che possano ricondurre a loro.
Il mondo del ransomware è caratterizzato da un linguaggio tecnico ricco di acronimi e termini specifici che possono rendere difficile la comprensione del fenomeno per chi non opera quotidianamente nel settore della sicurezza informatica. Molti di questi termini provengono dal gergo usato all’interno delle community cybercriminali e descrivono ruoli, modelli di business e tecniche operative proprie del crimine informatico organizzato.
Il seguente glossario raccoglie i principali acronimi e termini legati al ransomware, offrendo una panoramica chiara e sintetica del lessico usato nelle cronache di sicurezza e nelle analisi sulle minacce informatiche.
| Acronimo / Termine | Significato |
|---|---|
| RaaS (Ransomware-as-a-Service) | Modello criminale in cui i gruppi sviluppatori di ransomware forniscono l’infrastruttura, i malware e il supporto tecnico a “affiliati”, che conducono gli attacchi e condividono i proventi dei riscatti. |
| IAB (Initial Access Broker) | Attore malevolo che ottiene e vende accessi iniziali alle reti compromesse. È spesso il primo anello della catena del ransomware. |
| Affiliato | Cybercriminale che utilizza il ransomware fornito dal gruppo principale (RaaS) per eseguire attacchi. Riceve una percentuale del riscatto versato dalla vittima. |
| Double Extortion | Tecnica d’estorsione doppia: oltre a cifrare i dati, gli attaccanti li rubano e minacciano di pubblicarli se non viene pagato il riscatto. |
| Triple Extortion | Evoluzione della doppia estorsione: oltre al furto e alla pubblicazione dei dati, vengono minacciati anche i clienti o i partner della vittima per aumentare la pressione. |
| Data Leak Site (DLS) | Portale, solitamente nel dark web, dove i gruppi ransomware pubblicano i dati rubati alle vittime che rifiutano di pagare. Serve a intimidire e promuovere la propria “credibilità” criminale. |
| Locker / Crypto Ransomware | Tipologie di ransomware: i “locker” bloccano l’accesso al dispositivo, mentre i “crypto” cifrano i file rendendoli inutilizzabili. |
| Encryption Key | Chiave crittografica utilizzata dal ransomware per cifrare i dati. Senza di essa, i file restano illeggibili. |
| Decryption Tool | Strumento che consente di decifrare i dati. Può essere fornito dagli attaccanti dopo il pagamento del riscatto o da enti di sicurezza che rilasciano tool gratuiti. |
| Negotiator | Figura (interna o esterna) che si occupa di gestire la trattativa con il gruppo ransomware per conto della vittima. |
| Payload | La componente del ransomware che esegue materialmente la cifratura o l’esfiltrazione dei dati. |
| Persistence | Tecnica con cui il ransomware garantisce la propria sopravvivenza nel sistema, mantenendo l’accesso anche dopo riavvii o tentativi di rimozione. |
| Exfiltration | Fase dell’attacco in cui i dati vengono rubati e trasferiti verso i server controllati dagli attaccanti. |
| Ransom Note | Messaggio lasciato dagli attaccanti sul sistema infetto, che contiene le istruzioni per il pagamento del riscatto. |
| Tor / Onion Network (Dark Web) | Rete anonima utilizzata dai gruppi ransomware per comunicare, negoziare e pubblicare i dati rubati, rendendo difficile la loro tracciabilità. |
| Playbook di attacco | Sequenza predefinita di azioni, tecniche e strumenti utilizzati da un gruppo ransomware durante un’operazione. Ogni gang possiede il proprio “stile operativo”. |
| Wiper (Falso ransomware) | Malware che simula un attacco ransomware, ma in realtà distrugge i dati senza possibilità di recupero, spesso con finalità di sabotaggio. |
Il team Dark Lab di Red Hot Cyber conduce regolarmente interviste esclusive con le principali cybergang dedite al ransomware da profitto. Queste conversazioni dirette permettono di entrare nella mente degli attori delle minacce, esplorando motivazioni, modelli operativi e strategie economiche che spesso restano nell’ombra. Tale approccio consente ai difensori di migliorare le difese delle organizzazioni comprendendo a pieno motivazioni, tecniche e strumenti di attacco dei criminali informatici.
| Cyber gang intervistata | Descrizione |
|---|---|
| LockBit | Uno dei principali attori storici del RaaS globale, con focus su piattaforme e affiliati. |
| ShinyHunters | Gruppo attivo dal 2020 specializzato in data breach e ricatto via pubblicazione dati. |
| Lynx | Organizzazione ransomware emersa nel 2024, che combina tecniche di doppia estorsione. |
| Qilin | Gang ransomware concentrata sulle aziende europee e sull’uso rilevante di leak‑site. |
| RADAR & DISPOSSESSOR | Due gruppi intervistati insieme, collegati ad accessi iniziali brokerati e campagne RaaS. |
| RansomCortex | Organizzazione specializzata in ransomware avanzati con tecniche evasive e offuscamento. |
| Vanir Group | Gang attiva nel 2024, nota per attacchi a fornitori IT e ricatti verso corporate. |
| Stormous | Gruppo ransomware attivo nel 2024, noto per campagne mirate contro infrastrutture critiche. |
Come abbiamo visto in questi due articoli, la RaaS è un fenomeno criminale altamente specializzato e organizzato, dove il potere negoziale delle informazioni ha oggi un valore impressionante.

Il panorama geopolitico di questo ultimo periodo, rende questi attacchi informatici – soprattutto se indirizzati verso i sistemi critici dei paesi – un problema di sicurezza nazionale e questo porta i governi a gestirli con la massima attenzione e questo è quello che non è gradito dai criminali informatici.
Inoltre, vista la difficoltà nell’identificare la provenienza di un attacco ransomware (è stata la Russia, la Cina o la Corea del Nord, ovviamente sono esempi), può portare ad una destabilizzazione degli equilibri geopolitici costruiti in precedenza e l’innesco di potenziali escalation.
Il fenomeno del ransomware è in verticale aumento, questo perché è estremamente remunerativo e a basso costo. Aspettiamoci quindi che le tattiche di estorsione utilizzate dalle cyber-gang continueranno ad evolversi nei prossimi anni in modo ad oggi non prevedibile e che del ransomware inizieranno a parlarne le prime pagine dei giornali.
Per questo risulta imprescindibile (come spesso riportato sulle pagine di Red Hot Cyber) regolamentare la guerra informatica liberando la mente da quello “che era” il Tallin Manual, cercando di scrivere un trattato realmente internazionale e non solo scritto a beneficio della Nato e dell’alleanza Five Eyes.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…