
Un servizio di botnet chiamato Aisuru, offre un esercito di dispositivi IoT e router compromessi, per sferrare attacchi DDoS ad alto traffico. In soli tre mesi, la massiccia botnet Aisuru ha lanciato più di 1.300 attacchi DDoS, uno dei quali ha stabilito un nuovo record con un picco di 29,7 terabit al secondo.
Dall’inizio dell’anno, Cloudflare ha neutralizzato un totale di 2.867 attacchi Aisuru, caratterizzati da un’intensità notevole, con quasi il 45% di essi classificati come ipervolumetrici, ossia attacchi con una portata superiore a 1 Tbps o 1 miliardo di pacchetti al secondo (Bpps).
La stima di Cloudflare, società leader nella gestione e infrastruttura di Internet, indica che la botnet potrebbe essere costituita da un numero di host infetti compreso tra uno e quattro milioni a livello globale. I responsabili delle attività illecite nel settore informatico hanno la possibilità di affittare segmenti della botnet Aisuru presso i distributori per condurre attacchi DDoS (Distributed Denial-of-Service).
Un massiccio attacco ipervolumetrico, ad opera di dispositivi controllati da Aisuru, ha avuto luogo nel terzo trimestre del 2025 il quale è stato efficacemente mitigato da Cloudflare.
Previamente, Cloudflare aveva neutralizzato un altro attacco DDoS record, attribuito ad Aisuru con un livello di sicurezza medio-basso, che aveva raggiunto un picco di traffico di 22,2 Tbps.
Recentemente, è stato reso noto che la medesima botnet ha preso di mira la rete Azure di Microsoft, sferrando un poderoso attacco DDoS da 15 Tbps originato da circa 500.000 indirizzi IP diversi.
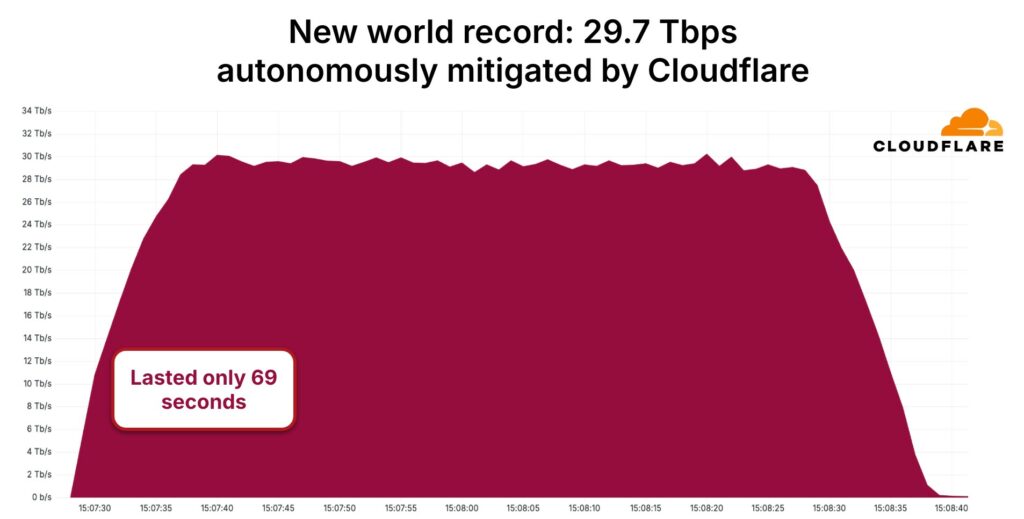
L’attacco di record subito dall’ignota società Internet è stato caratterizzato da una durata di 69 secondi, con un traffico che ha raggiunto il picco di 29,7 Tbps. Nella sua strategia, sono state impiegate tecniche di inondazione UDP, generando così un ingente quantità di traffico “spazzatura” indirizzato verso un numero medio di 15.000 porte di destinazione ogni secondo.
Cloudflare afferma che gli attacchi Aisuru possono essere così devastanti che la quantità di traffico può mettere in difficoltà i provider di servizi Internet (ISP), anche se non sono presi di mira direttamente. “Se il traffico di attacco di Aisuru può interrompere parti dell’infrastruttura Internet degli Stati Uniti quando i suddetti ISP non erano nemmeno l’obiettivo dell’attacco, immagina cosa può fare quando è direttamente mirato a ISP non protetti o non sufficientemente protetti, infrastrutture critiche, servizi sanitari, servizi di emergenza e sistemi militari”, afferma Cloudflare .
I dati statistici di Cloudflare mostrano che gli attacchi DDoS ipervolumetrici della botnet Aisuru sono in costante aumento quest’anno, raggiungendo 1.304 incidenti solo nel terzo trimestre. Secondo i ricercatori, Aisuru prende di mira aziende di vari settori, tra cui il gaming, i provider di hosting, le telecomunicazioni e i servizi finanziari.
La frequenza degli attacchi DDoS di intensità superiore a 100 Mpps ha subito un aumento significativo del 189% rispetto al trimestre precedente. Contemporaneamente, gli attacchi che superano 1 Tbps sono cresciuti in maniera ancora più rilevante, ben del 227%, sempre su base trimestrale. Soltanto una breve finestra temporale, inferiore ai 10 minuti, è a disposizione dei difensori e dei servizi on-demand per rispondere efficacemente agli attacchi, dato che la maggior parte di questi ultimi si conclude entro tale lasso di tempo, stando ai dati riportati da Cloudflare.
“Un attacco breve può durare solo pochi secondi, ma i disagi che provoca possono essere gravi e il ripristino richiede molto più tempo”, ha spiegato Cloudflare. “I team di ingegneria e operativi si trovano quindi a dover affrontare un processo complesso e articolato in più fasi per ripristinare la funzionalità dei sistemi critici, verificare la coerenza dei dati nei sistemi distribuiti e ripristinare un servizio sicuro e affidabile per i clienti.”
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…