
14 maggio 2025 – Nelle prime ore di questa mattina, sul forum underground russo XSS, noto per essere una vetrina di primo piano per la compravendita di dati compromessi, è apparso un post allarmante: il gruppo Machine1337 ha rivendicato una presunta violazione dei sistemi interni di Apple.com.
Il post, accompagnato dal logo della celebre azienda e firmato “Breached by Machine1337”, indica che nel febbraio 2025 Apple sarebbe stata vittima di una data breach che avrebbe comportato l’esposizione di strumenti interni. Secondo quanto dichiarato dall’attore malevolo, sono stati sottratti 3.000 file, offerti in sample con un link per il download. L’intero pacchetto viene messo in vendita per 5.000 dollari.
Nel post è presente anche un link che punta a Mega, solo che al momento non risulta disponibile al download.
Disclaimer: Questo rapporto include screenshot e/o testo tratti da fonti pubblicamente accessibili. Le informazioni fornite hanno esclusivamente finalità di intelligence sulle minacce e di sensibilizzazione sui rischi di cybersecurity. Red Hot Cyber condanna qualsiasi accesso non autorizzato, diffusione impropria o utilizzo illecito di tali dati. Al momento, non è possibile verificare in modo indipendente l’autenticità delle informazioni riportate, poiché l’organizzazione coinvolta non ha ancora rilasciato un comunicato ufficiale sul proprio sito web. Di conseguenza, questo articolo deve essere considerato esclusivamente a scopo informativo e di intelligence.
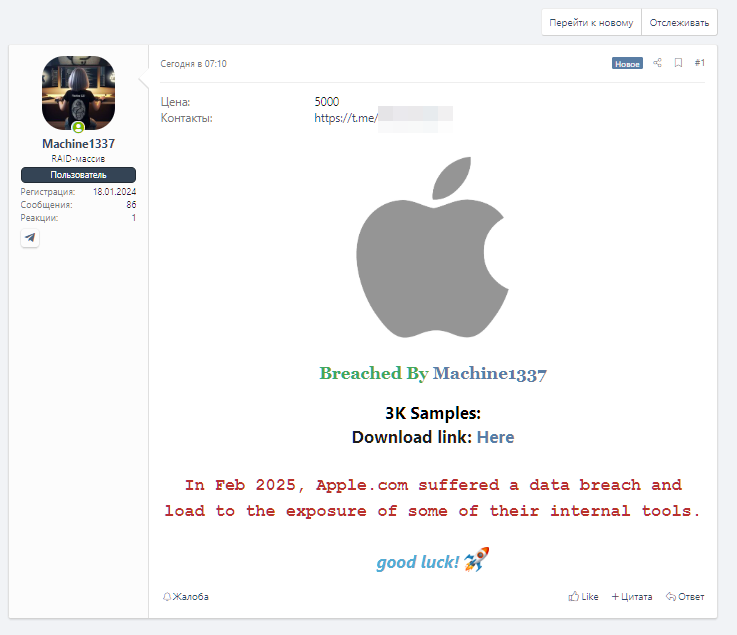
Nel dettaglio, il messaggio sul forum recita:
“In Feb 2025, Apple.com suffered a data breach and load to the exposure of some of their internal tools.”
Anche se il messaggio presenta errori grammaticali, lascia intendere che siano stati compromessi strumenti interni aziendali, senza però specificare la natura tecnica del vettore di attacco. L’attore fornisce un contatto su Telegram per eventuali trattative.
XSS è uno dei forum più attivi nel panorama underground, usato da gruppi come RansomHouse, Stormous e Qilin per la pubblicazione di leak, vendita di accessi RDP, vulnerabilità zero-day e molto altro. La pubblicazione di oggi si inserisce in un trend crescente di attacchi ad alto profilo mirati contro big tech e fornitori SaaS.
Al momento Apple non ha rilasciato comunicazioni ufficiali. Non è chiaro se i file contenuti nel dump siano effettivamente autentici né quali strumenti interni siano stati compromessi. Tuttavia, la reputazione del forum e la modalità con cui il leak è stato presentato spingono diversi analisti threat intel a considerare l’annuncio potenzialmente credibile, almeno nella fase iniziale.
Il threat actor Machine1337 si presenta come un profilo emergente ma già attivo nell’ecosistema underground, con una presenza confermata su XSS Forum e Telegram. La sua attività recente include la rivendicazione di un presunto data breach ai danni di Apple.com, pubblicata su XSS lanciando la vendita di 3.000 file interni, un annuncio ancora in fase di verifica da parte degli analisti.
Nel suo canale Telegram (che conta 24 iscritti al momento), Machine1337 si definisce: “Red Teamer, Offensive Developer & Penetration Tester” Con un focus su:
Il canale ha subito diverse chiusure, segno che il suo contenuto ha attirato l’attenzione di moderatori o forze dell’ordine, ma ha continuato a riorganizzarsi creando versioni alternative (es. “Channel 2.0”).
Mentre la comunità cybersecurity attende conferme e analisi più approfondite sul contenuto del dump, questo episodio ci ricorda come anche le aziende più protette non siano immuni da violazioni. Se confermato, il data breach di Apple del 2025 entrerà nella lista degli incidenti più significativi dell’anno.
Red Hot Cyber continuerà a monitorare la vicenda e fornirà aggiornamenti in caso di conferme ufficiali o nuove informazioni da fonti OSINT e threat intelligence.
Come nostra consuetudine, lasciamo spazio ad una dichiarazione dell’azienda qualora voglia darci degli aggiornamenti su questa vicenda e saremo lieti di pubblicarla con uno specifico articolo dando risalto alla questione.
RHC monitorerà l’evoluzione della vicenda in modo da pubblicare ulteriori news sul blog, qualora ci fossero novità sostanziali. Qualora ci siano persone informate sui fatti che volessero fornire informazioni in modo anonimo possono accedere utilizzare la mail crittografata del whistleblower.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…