
Quando si parla di cybersecurity, non è raro imbattersi in notizie che sembrano prese da un film di fantascienza. Eppure, la realtà è ancora più sorprendente e a volte inquietante. La storia dei due cittadini ucraini sospettati di far parte del gruppo ransomware Black Basta è un esempio lampante di come la minaccia informatica sia una realtà sempre più concreta e pericolosa.
Le autorità ucraine e tedesche hanno identificato due cittadini ucraini sospettati di far parte di Black Basta, un gruppo ransomware (RaaS) collegato alla Russia.
Secondo la Polizia informatica ucraina, i sospettati erano specializzati nell’hacking tecnico di sistemi protetti e partecipavano alla preparazione di attacchi informatici tramite ransomware. In particolare, gli individui agivano come “hash cracker”, professionisti nell’estrazione di password dai sistemi informatici mediante software dedicati. Le credenziali ottenute venivano poi utilizzate per infiltrarsi nelle reti aziendali, installare ransomware e richiedere riscatti per il recupero dei dati crittografati.
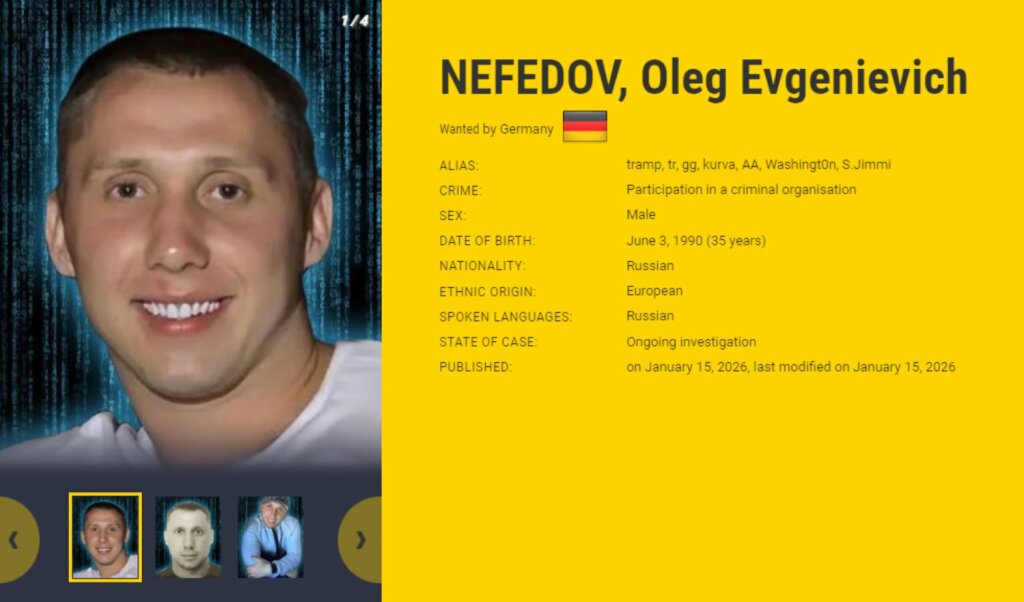
Il presunto leader del gruppo, Oleg Evgenievich Nefedov, cittadino russo di 35 anni, è stato inserito nella lista dei criminali più ricercati dell’Unione Europea e tra le persone segnalate come pericolose dall’INTERPOL. Le autorità hanno eseguito perquisizioni nelle abitazioni dei sospetti a Ivano-Frankivsk e Leopoli, sequestrando dispositivi digitali e asset in criptovaluta.
Black Basta è comparso per la prima volta nel panorama delle minacce informatiche nell’aprile 2022. Il gruppo ha preso di mira oltre 500 aziende in Nord America, Europa e Australia e molte anche in Italia, accumulando, secondo stime, centinaia di milioni di dollari in criptovalute attraverso pagamenti illeciti.
All’inizio del 2025, sono trapelati online registri di chat interne di Black Basta relativi a un anno di attività, rivelando dettagli sulla struttura interna, sui membri chiave e sulle vulnerabilità sfruttate per penetrare nelle organizzazioni bersaglio. Da questi documenti è emerso che Nefedov era a capo del gruppo, utilizzando diversi alias, tra cui Tramp, Trump, GG e AA. Alcuni rapporti lo collegano a figure politiche russe e agenzie di intelligence come FSB e GRU, connessioni che avrebbe sfruttato per proteggere le proprie operazioni e sfuggire alla giustizia internazionale.
Le indagini suggeriscono anche un legame tra Nefedov e Conti, gruppo ransomware attivo dal 2020 e ormai sciolto, successore di Ryuk. Nel 2022, il Dipartimento di Stato americano aveva annunciato una ricompensa di 10 milioni di dollari per informazioni su cinque membri di Conti, tra cui Target, Tramp, Dandis, Professor e Reshaev.
Dopo il ritiro di Conti nel 2022, Black Basta è emerso come gruppo autonomo insieme a BlackByte e KaraKurt, mentre altri ex membri si sono uniti a BlackCat, Hive, AvosLocker e HelloKitty, oggi inattivi.
Secondo il Bundeskriminalamt (BKA), Nefedov gestiva tutte le operazioni del gruppo: decideva gli obiettivi, assegnava compiti, partecipava alle trattative per i riscatti e amministrava i fondi ottenuti tramite estorsione.
Le fughe di dati hanno portato a una apparente inattività di Black Basta a partire da febbraio 2025, con il blocco dei siti per la diffusione dei dati rubati. Tuttavia, esperti di sicurezza sottolineano che i membri di bande ransomware tendono a riciclarsi in nuovi gruppi o a rinascere sotto nuove identità. Alcune analisi di ReliaQuest e Trend Micro indicano che diversi ex affiliati di Black Basta potrebbero essere entrati a far parte dell’operazione ransomware CACTUS, con un picco di attacchi rilevato a febbraio 2025, in concomitanza con la chiusura del sito di Black Basta.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…