
L’11 giugno, un ingegnere di Microsoft ha inavvertitamente reso pubblico 4GB di codice interno relativo a Microsoft PlayReady. La fuga di informazioni è avvenuta sulla Microsoft Developer Community, un forum dedicato agli sviluppatori.
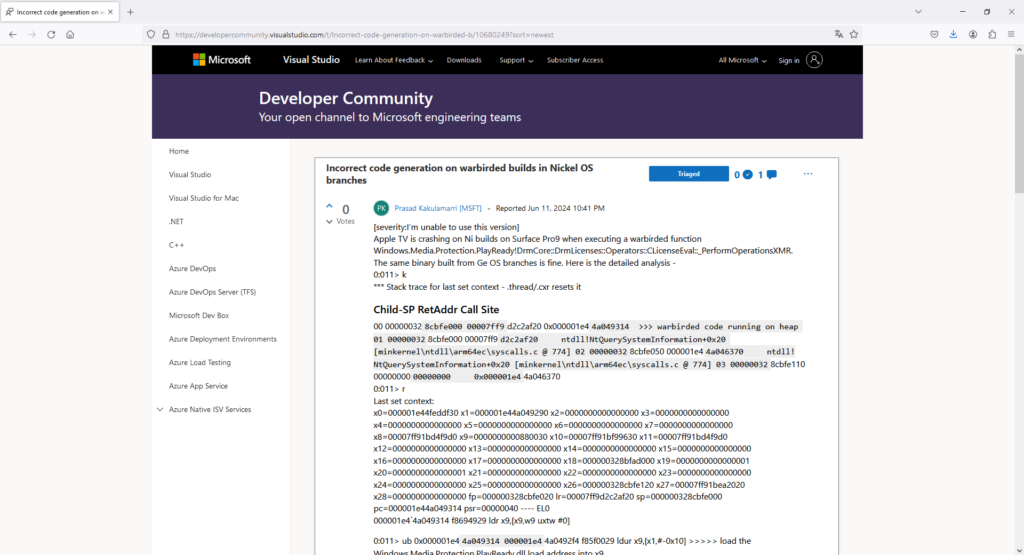
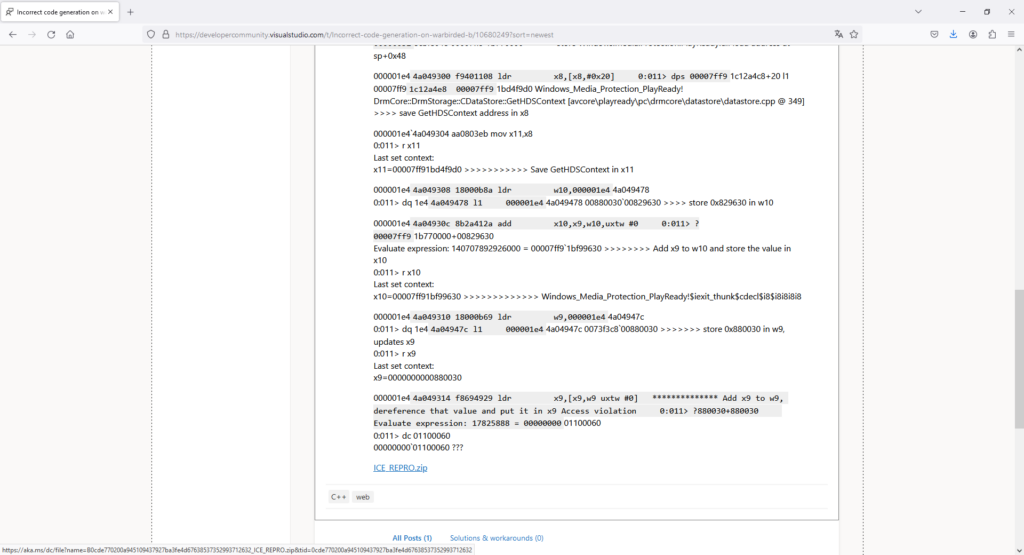
Il materiale trapelato includeva:
Queste componenti sono fondamentali per la protezione del contenuto e la gestione dei diritti digitali (DRM) all’interno delle piattaforme Microsoft.
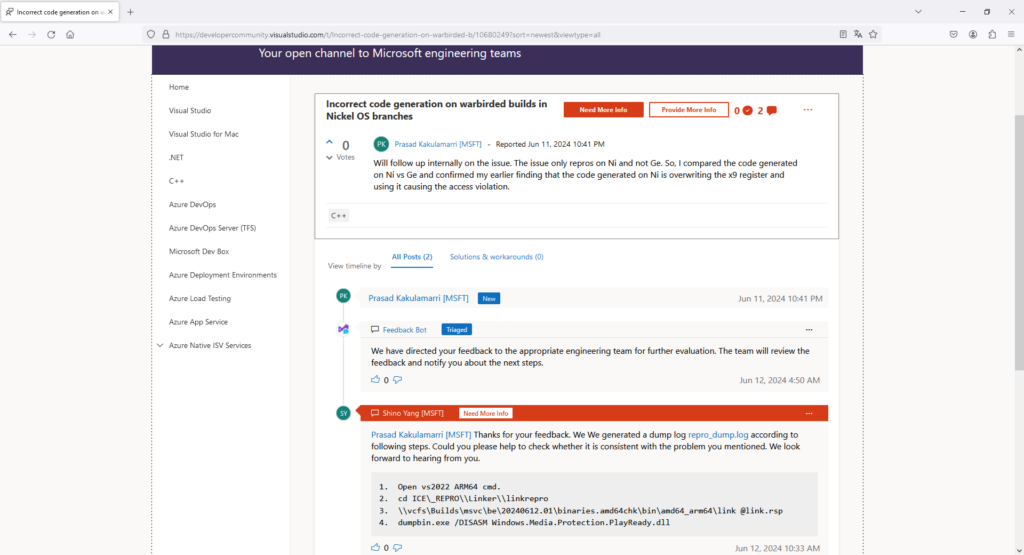
I ricercatori del AG Security Research Lab sono riusciti a compilare con successo la libreria Windows PlayReady DLL utilizzando il codice trapelato. Un aspetto curioso di questa vicenda è che un utente della Microsoft Developer Community ha fornito istruzioni passo-passo su come avviare il processo di compilazione, facilitando ulteriormente il lavoro dei ricercatori.
Un altro elemento di interesse riguarda il Microsoft Symbol Server, che non blocca le richieste di file PDB corrispondenti alle librerie WarBird di Microsoft. Questo dettaglio ha comportato una fuga involontaria di ulteriori informazioni sensibili.
Adam Gowdiak, dell’AG Security Research Lab, ha segnalato l’incidente a Microsoft. In risposta, Microsoft ha rimosso il post dal forum. Tuttavia, al momento della stesura di questo articolo, il link per il download è ancora attivo, sollevando preoccupazioni sulla sicurezza e la gestione delle informazioni sensibili.
Questo incidente evidenzia l’importanza di una gestione accurata delle informazioni riservate e dei dati sensibili all’interno delle piattaforme di sviluppo. Microsoft dovrà affrontare le implicazioni di questa fuga di dati e implementare misure più rigorose per prevenire futuri incidenti simili.
La vicenda potrebbe portare a una revisione delle politiche di sicurezza e della gestione delle informazioni all’interno di Microsoft, oltre a sollevare questioni sull’affidabilità delle piattaforme di condivisione tra sviluppatori. Gli esperti di sicurezza e gli sviluppatori dovranno collaborare per garantire che simili incidenti non si ripetano, proteggendo così le informazioni sensibili e mantenendo la fiducia degli utenti.
In conclusione, l’incidente dell’11 giugno rappresenta un campanello d’allarme per tutte le aziende tecnologiche: la sicurezza dei dati deve essere una priorità assoluta, e ogni falla può avere conseguenze significative sulla reputazione e sull’affidabilità di un’azienda.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…
 Cyber Italia
Cyber ItaliaNegli ultimi giorni è stato segnalato un preoccupante aumento di truffe diffuse tramite WhatsApp dal CERT-AGID. I messaggi arrivano apparentemente da contatti conosciuti e richiedono urgentemente denaro, spesso per emergenze come spese mediche improvvise. La…