
Nel mondo della sicurezza circola da anni una convinzione tanto diffusa quanto pericolosa: “se è patchato, è sicuro”.
Il caso dell’accesso amministrativo tramite FortiCloud SSO ai dispositivi FortiGate dimostra, ancora una volta, quanto questa affermazione sia non solo incompleta, ma in alcuni contesti profondamente fuorviante.
Da dicembre 2025 a oggi stiamo infatti osservando compromissioni reali di firewall FortiGate perfettamente aggiornati, caratterizzate da modifiche malevole alla configurazione, creazione di account amministrativi persistentied esfiltrazione dei file di configurazione. Il tutto senza ricorrere a nuovi zero-day o a tecniche di attacco particolarmente rumorose.
Il vettore non è un’incognita. È noto, documentato e — soprattutto — ancora operativo: FortiCloud SSO.
All’inizio di dicembre 2025 vengono rese pubbliche due vulnerabilità critiche:
Entrambe consentono un authentication bypass nel meccanismo FortiCloud SSO, permettendo a un attore remoto non autenticato di ottenere accesso amministrativo su dispositivi FortiOS quando l’SSO cloud è abilitato.
Fortinet rilascia le patch ufficiali il 9 dicembre 2025, assegnando alle vulnerabilità un CVSS 9.8. Il messaggio è chiaro: aggiornare immediatamente. Ma, come spesso accade, la realtà operativa segue un’altra traiettoria.
Secondo i ricercatori di Arctic Wolf, attività malevole di login SSO iniziano a comparire quasi subito dopo la disclosure pubblica, in alcuni casi prima che molte organizzazioni riescano a patchare.
È un passaggio cruciale, perché segna uno spartiacque: il cloud management diventa un vettore di accesso privilegiato, indipendente dall’esposizione classica delle interfacce di management locali.
Dal 15 gennaio 2026, sempre secondo Arctic Wolf, il fenomeno evolve in modo netto: non più eventi isolati, ma una campagna strutturata e automatizzata.
Il pattern osservato è il seguente:
Il tutto avviene in pochi secondi, con una sequenza che suggerisce chiaramente l’uso di script per automatizzare l’attacco.
Arctic Wolf lo chiarisce senza giri di parole:
It is not known at this time whether the latest threat activity observed is fully covered by the patch that initially addressed CVE-2025-59718 and CVE-2025-59719.
Questo spiega perché molte organizzazioni colpite dichiarino di avere:
Eppure il firewall viene modificato “dall’interno”, con privilegi amministrativi.
FortiCloud SSO nasce per semplificare le attività di gestione e supporto ed è, nella percezione di molti amministratori, uno strumento affidabile e sicuro per definizione, perché fornito direttamente dal vendor e integrato nativamente nel prodotto.
Proprio per questo, quando resta attivo senza un hardening adeguato, tende a non essere trattato come un vero canale di accesso amministrativo critico.
Nei fatti, FortiCloud SSO espone un accesso cloud-based con privilegi elevati, spesso non limitato per indirizzo IP, raramente sottoposto a controlli stringenti e, soprattutto, poco monitorato rispetto alle classiche interfacce di management locali. Non perché sia considerato “debole”, ma perché è percepito come intrinsecamente fidato.
Il risultato è che l’attaccante non è costretto a forzare l’accesso: lo utilizza.
Ed è proprio questa legittimità apparente, unita alla fiducia implicita nel canale cloud, a rendere il vettore così efficace e difficile da individuare in fase di detection.
I dati di Shadowserver Foundation aiutano a inquadrare la dimensione del problema:
Non parliamo di ambienti di test o lab dimenticati. Parliamo di firewall perimetrali in produzione, spesso in contesti enterprise, MSP e Pubblica Amministrazione.
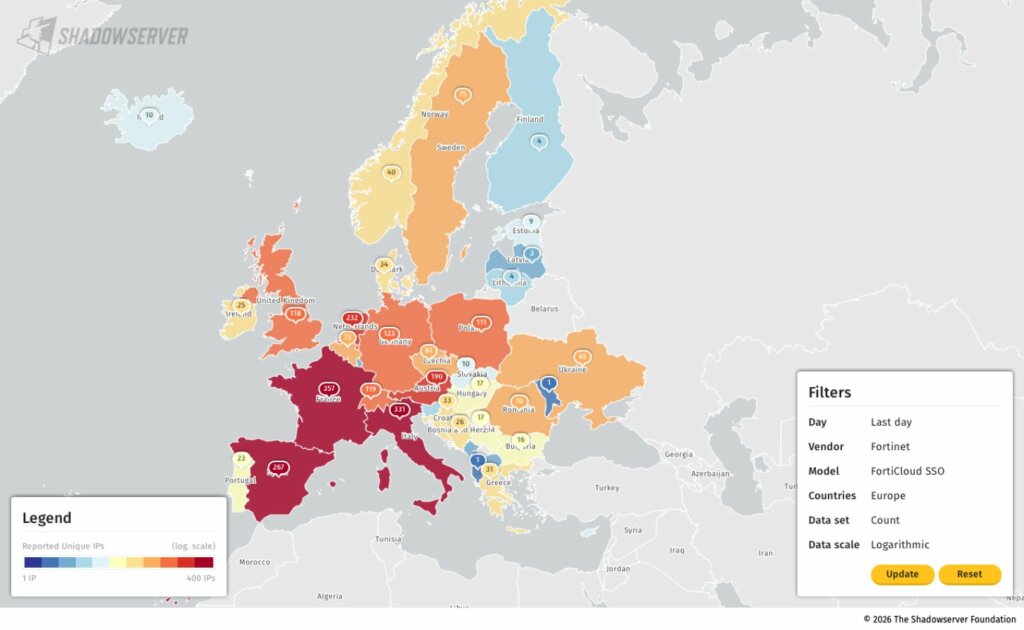
Per quanto riguarda gli Indicatori di Compromissione (IoC) associati a questa campagna — inclusi pattern di login SSO malevoli, creazione di account amministrativi persistenti, sequenze di modifica della configurazione ed eventi di esfiltrazione — si rimanda direttamente all’analisi tecnica pubblicata da Arctic Wolf, che fornisce un elenco dettagliato e aggiornato basato su osservazioni reali sul campo.
Considerata l’evoluzione rapida dell’attività e la natura automatizzata degli attacchi, fare riferimento alla fonte primaria consente di evitare duplicazioni e mantenere allineata la detection agli indicatori più recenti.
Dal punto di vista delle mitigazioni immediate, Fortinet ha indicato un workaround temporaneo in relazione alle vulnerabilità CVE-2025-59718 e CVE-2025-59719, rilevante anche alla luce dell’attività attualmente osservata, che coinvolge l’accesso amministrativo tramite FortiCloud SSO.
Se FortiCloud SSO è abilitato, può essere opportuno disattivarlo temporaneamente fino a quando non saranno disponibili indicazioni di remediation definitive.
Disabilitazione FortiCloud SSO da CLI
config system global
set admin-forticloud-sso-login disable
end
Poiché il meccanismo di accesso iniziale non è ancora completamente chiarito, non è possibile affermare con certezza che questo workaround sia totalmente efficace contro tutte le varianti della campagna in corso. Tuttavia, la disabilitazione dell’SSO cloud riduce in modo significativo la superficie d’attacco e interrompe uno dei vettori principali osservati finora.
In attesa di ulteriori chiarimenti da parte del vendor, la riduzione dell’esposizione rimane la misura più razionale, da affiancare ad attività di audit, monitoraggio dei log e revisione degli accessi amministrativi.
Questo caso evidenzia un problema più ampio e strutturale: la superficie d’attacco si è spostata verso il cloud management, gli accessi “legittimi” sono diventati il nuovo vettore e l’attenzione ossessiva sulle CVE oscura il rischio configurativo
Il caso FortiGate / FortiCloud SSO non è un’anomalia. È un segnale chiaro di come il cloud management stia diventando il nuovo perimetro da difendere. Gli attacchi non passano più solo dagli exploit. Passano dagli accessi dimenticati, dai servizi lasciati attivi, dalla fiducia cieca nel patching. E come spesso accade, i numeri di Shadowserver arrivano molto prima degli incident report.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…