
Una recente scoperta ha rivelato che gli hacker possono sfruttare una falla in Microsoft Teams su Windows per ottenere token di autenticazione crittografati, i quali garantiscono l’accesso a chat, email e file archiviati su SharePoint senza autorizzazione. Brahim El Fikhi ha dettagliato questa vulnerabilità in un post pubblicato il 23 ottobre 2025, evidenziando come i token, conservati all’interno di un database di cookie ispirato a quello di Chromium, siano vulnerabili alla decrittazione tramite l’utilizzo dell’API di Protezione Dati (DPAPI) fornita da Windows.
I token di accesso offrono agli aggressori la possibilità di impersonare gli utenti, inviando ad esempio messaggi o email di Teams a nome delle vittime, al fine di eseguire attacchi di ingegneria sociale o per mantenere la persistenza. Tali metodi eludono i recenti potenziamenti della sicurezza, mettendo a rischio gli ambienti aziendali con possibili spostamenti laterali e conseguente esfiltrazione dei dati.
Il focus di El Fikhi sulle applicazioni desktop di Office, soprattutto Teams, rivela vulnerabilità nei componenti browser incorporati, deputati alla gestione dell’autenticazione tramite login.microsoftonline.com. Un’analisi recente segnala che l’ecosistema Microsoft resta un bersaglio privilegiato, vista la diffusione capillare all’interno delle aziende.
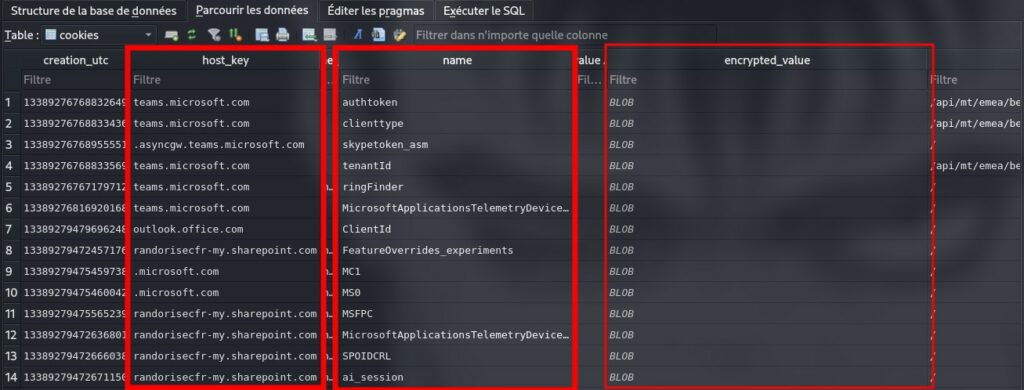
Le prime versioni di Microsoft Teams memorizzavano i cookie di autenticazione in testo normale all’interno del file SQLite in %AppData%LocalMicrosoftTeamsCookies, una falla scoperta da Vectra AI nel 2022 che consentiva semplici letture di file per raccogliere token per l’abuso della Graph API, bypassando l’MFA.
Gli aggiornamenti hanno eliminato questo tipo di archiviazione in testo normale, adottando formati crittografati allineati alla protezione dei cookie di Chromium per impedire il furto su disco. Tuttavia, questo cambiamento introduce nuovi vettori di attacco. I token ora utilizzano la crittografia AES-256-GCM protetta da DPAPI, un’API di Windows che collega le chiavi ai contesti utente o macchina per l’isolamento dei dati.
Per contrastare le minacce, sono previste misure che comprendono il monitoraggio delle interruzioni anomale di ms-teams.exe o di pattern ProcMon inusuali.
Inoltre, è consigliabile utilizzare l’uso di team basati sul web in modo da limitare l’archiviazione locale. La rotazione dei token tramite policy ID Entra e il monitoraggio dei log API per rilevare irregolarità sono ulteriori passaggi cruciali.
Man mano che le minacce a Teams si evolvono, assumono un’importanza fondamentale le regole EDR che si basano su DPAPI.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…