
Mandiant ha reso pubblico un ampio set di tabelle rainbow dedicate a Net-NTLMv1 con l’obiettivo di dimostrare in modo concreto quanto questo protocollo di autenticazione sia ormai insicuro. Nonostante Net-NTLMv1 sia deprecato da anni e le sue debolezze siano ampiamente documentate, i consulenti dell’azienda continuano a rilevarne l’utilizzo in ambienti aziendali ancora operativi.
Secondo Mandiant, la persistenza di questo protocollo legacy è spesso dovuta all’inerzia organizzativa e alla difficoltà di mostrare un rischio immediato e tangibile. La pubblicazione del dataset intende ridurre questa barriera, fornendo alla comunità strumenti pratici per dimostrare l’effettiva facilità con cui Net-NTLMv1 può essere sfruttato.
Le criticità di Net-NTLMv1 sono note almeno dalla fine degli anni Novanta, quando sono state pubblicate le prime analisi crittografiche del protocollo. Nel 2012, durante DEFCON 20, la comunità di sicurezza ha ribadito pubblicamente l’inadeguatezza di questo meccanismo di autenticazione rispetto agli standard moderni.
Un passaggio rilevante si è verificato il 30 agosto 2016, quando Hashcat ha introdotto il supporto per la ricostruzione dell’hash NT a partire dalle chiavi DES recuperate. Questa funzionalità ha reso più immediato il completamento della catena di attacco, consentendo di trasformare le chiavi ottenute in credenziali direttamente riutilizzabili.
Anche il concetto di tabelle rainbow non è recente: il primo studio formale risale al 2003, a firma di Philippe Oechslin, sulla base del compromesso tempo-memoria introdotto da Martin Hellman già nel 1980.
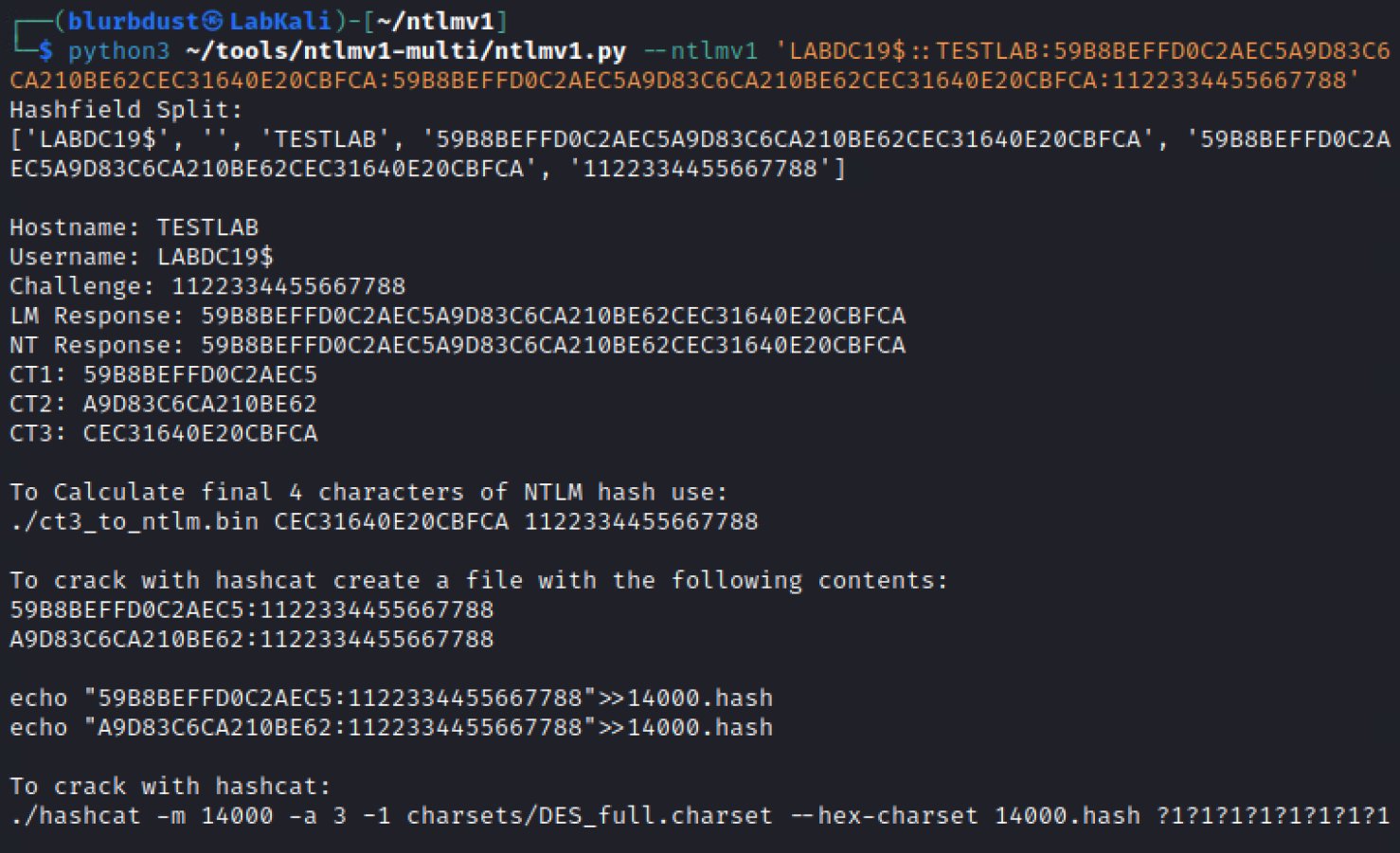
Net-NTLMv1 utilizza tre chiavi DES derivate dall’hash della password. In assenza di Extended Session Security (ESS), se un attaccante intercetta una risposta Net-NTLMv1 associata a un testo in chiaro noto – come il valore statico 1122334455667788 – diventa possibile applicare un attacco a testo in chiaro noto (Known Plaintext Attack).
Questa caratteristica consente di recuperare il materiale crittografico utilizzato durante l’autenticazione. Poiché tale materiale corrisponde all’hash della password dell’oggetto Active Directory coinvolto, i risultati possono essere sfruttati immediatamente per compromettere account utente o computer, con frequenti scenari di escalation dei privilegi.
Un caso particolarmente critico è quello in cui l’autenticazione viene forzata da un controller di dominio. Il recupero dell’hash della password dell’account macchina del DC può infatti consentire operazioni DCSync e portare alla compromissione dell’intero dominio Active Directory.
Il set di tabelle rainbow pubblicato da Mandiant è disponibile tramite Google Cloud Storage e può essere archiviato interamente su una singola unità SSD da 2 TB, dal costo indicativo di circa 130 dollari. I checksum SHA512 forniti consentono di verificarne l’integrità prima dell’utilizzo.
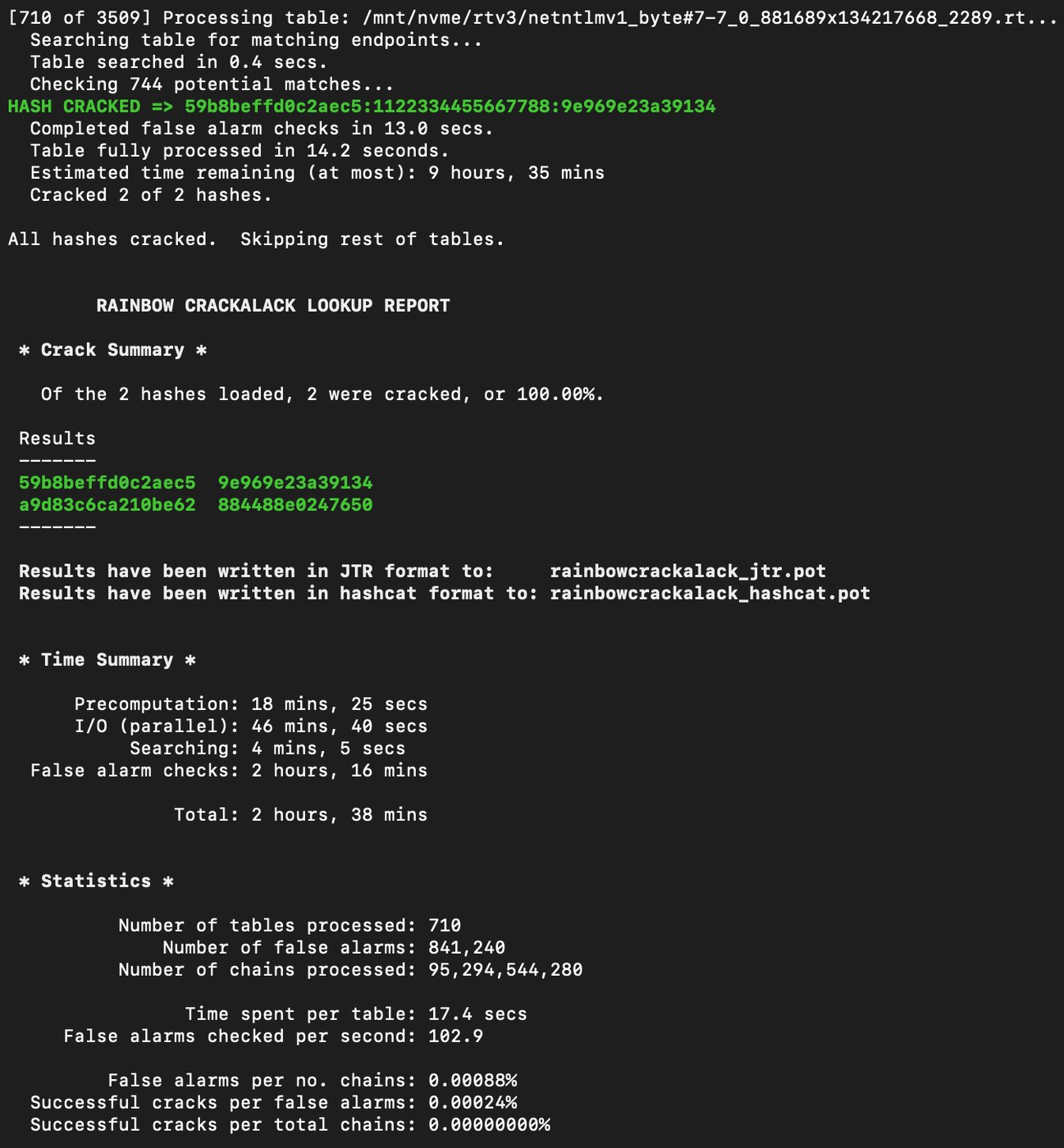
Il rilascio del dataset è accompagnato da rcrelay.py, uno strumento integrato in un fork aggiornato di RainbowCrack. Questo tool automatizza la ricerca nelle tabelle rainbow non appena viene intercettato un hash Net-NTLMv1, eliminando gran parte delle operazioni manuali richieste in passato.
Secondo Mandiant, questa integrazione riduce drasticamente la complessità dell’attacco e rende evidente quanto Net-NTLMv1 sia ormai indifendibile in ambienti moderni.
Per ottenere hash Net-NTLMv1, un attaccante può indurre sistemi Windows ad autenticarsi verso un host controllato, forzando l’uso del protocollo. Nel blog post, Mandiant cita PetitPotam come esempio di tecnica di coercizione dell’autenticazione utilizzata per generare connessioni in ingresso, incluse quelle provenienti da controller di dominio.
La suddivisione dell’hash Net-NTLMv1 nelle sue componenti DES non è un passaggio opzionale, ma una caratteristica intrinseca del protocollo stesso. Gli strumenti come rcrelay.py gestiscono automaticamente questa logica durante la fase di ricerca.
Le tabelle rainbow pubblicate coprono le prime due chiavi DES, ciascuna lunga 7 byte. La terza chiave, lunga solo 2 byte, è così ridotta da poter essere recuperata tramite forza bruta in frazioni di secondo ed è per questo motivo esclusa dal dataset.
Una volta ottenute tutte le componenti, Hashcat consente di ricostruire l’hash NT finale dell’account compromesso, rendendolo immediatamente utilizzabile per attacchi successivi, come DCSync, tramite strumenti della suite Impacket.
Mandiant raccomanda di disabilitare immediatamente Net-NTLMv1 in tutti gli ambienti. La configurazione corretta prevede l’uso esclusivo di NTLMv2, impostazione applicabile sia tramite criteri locali del computer sia attraverso i Criteri di gruppo.
Poiché si tratta di impostazioni locali, un attaccante con privilegi amministrativi potrebbe temporaneamente ripristinare uno stato vulnerabile. Per questo motivo, oltre alla disattivazione, è essenziale monitorare l’utilizzo del protocollo.
Il controllo può essere effettuato analizzando i log di sicurezza, in particolare gli eventi con ID 4624. Se il campo relativo al pacchetto di autenticazione indica “LM” o “NTLMv1”, significa che è stato utilizzato un meccanismo obsoleto che richiede un intervento immediato.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…