PentestAgent è un altro nuovo progetto open source sviluppato dal gruppo GH05TCREW che mira a supportare le attività di penetration testing attraverso l’uso di agenti basati su modelli linguistici.
Il tool è progettato per funzionare con Python dalla versione 3.10 in poi e richiede una chiave API compatibile con OpenAI, Anthropic o altri provider supportati da LiteLLM.
L’installazione può avvenire clonando il repository GitHub ufficiale e utilizzando script dedicati per Windows, Linux e macOS, che automatizzano la creazione dell’ambiente virtuale e l’installazione delle dipendenze. In alternativa, è possibile procedere manualmente configurando una virtual environment Python, installando i pacchetti necessari e completando l’installazione di Playwright con Chromium, indispensabile per l’utilizzo degli strumenti di navigazione web integrati.
Per il corretto funzionamento del software è necessario creare un file di configurazione .env nella directory principale del progetto. All’interno vanno specificate le variabili d’ambiente relative alla chiave API del provider scelto e al modello da utilizzare, come ad esempio Claude Sonnet o GPT-5. PentestAgent è compatibile con qualsiasi modello supportato dall’ecosistema LiteLLM.
Una volta configurato, il tool può essere avviato tramite riga di comando, aprendo un’interfaccia testuale interattiva. È possibile lanciare PentestAgent senza parametri, specificando direttamente un target IP o abilitando l’esecuzione degli strumenti all’interno di un container Docker per una maggiore sicurezza e isolamento dell’ambiente di test.
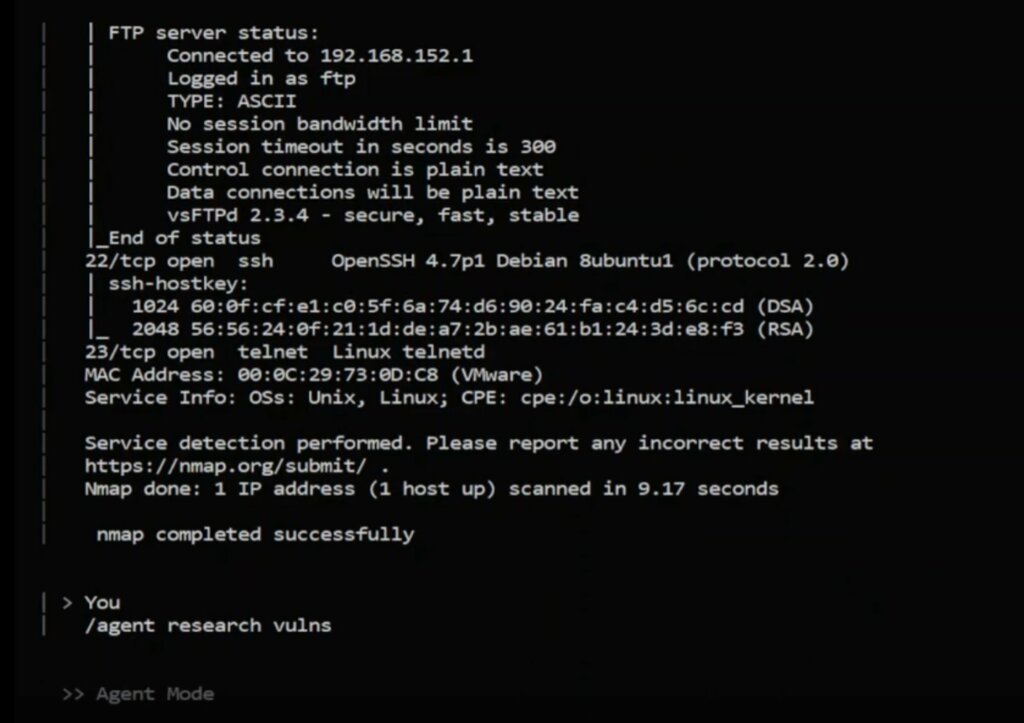
Il supporto Docker rappresenta una delle caratteristiche principali del progetto. Gli utenti possono scegliere tra immagini precompilate leggere, che includono strumenti di base come nmap e netcat, oppure immagini basate su Kali Linux, già dotate di framework avanzati come Metasploit, sqlmap e Hydra. In alternativa, le immagini possono essere costruite localmente tramite Docker Compose, con profili differenti a seconda delle esigenze operative.
PentestAgent offre tre modalità operative distinte. La modalità Assist consente un’interazione guidata con l’agente, lasciando il controllo all’utente. La modalità Agent permette l’esecuzione autonoma di un singolo task, mentre la modalità Crew attiva un sistema multi-agente in cui un orchestratore coordina più entità specializzate per affrontare attività complesse.
L’interfaccia TUI mette a disposizione una serie di comandi per la gestione delle operazioni, tra cui l’impostazione del target, la visualizzazione degli strumenti disponibili, la generazione di report e la consultazione delle note raccolte durante le sessioni. È inoltre possibile interrompere l’esecuzione degli agenti o uscire rapidamente dall’applicazione tramite scorciatoie da tastiera.
Il progetto include playbook predefiniti per test di sicurezza black-box, oltre a un sistema di gestione della conoscenza basato su RAG. Metodologie, vulnerabilità e wordlist possono essere caricate per arricchire il contesto operativo degli agenti. Le informazioni raccolte vengono salvate in modo persistente e, nella modalità Crew, utilizzate per costruire un grafo di conoscenza che supporta analisi strategiche avanzate. L’utilizzo del software è consentito esclusivamente su sistemi per i quali si dispone di autorizzazione esplicita, come indicato nelle note legali del progetto.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…
 Cyber Italia
Cyber ItaliaNegli ultimi giorni è stato segnalato un preoccupante aumento di truffe diffuse tramite WhatsApp dal CERT-AGID. I messaggi arrivano apparentemente da contatti conosciuti e richiedono urgentemente denaro, spesso per emergenze come spese mediche improvvise. La…