
Un recente evento ha visto un hacker anonimo rendere pubblica una chiave di sicurezza cruciale, impiegata da Sony per salvaguardare l’integrità della catena di trust nella console PlayStation 5. Questa chiave di sicurezza, conosciuta con il termine BootROM, rappresenta un elemento essenziale nell’architettura di sicurezza concepita da Sony. In teoria, la diffusione di tale chiave potrebbe agevolare futuri tentativi di compromettere la sicurezza della console.
La fonte della chiave trapelata sembra risalire a due figure ben note nella comunità degli hacker di console, BrutalSam_ e Shadzey1. Allo stato attuale, è ampiamente accettato che la chiave BootROM esposta sia autentica e valida, sebbene le sue applicazioni più ampie richiederanno ulteriori ricerche approfondite.
La chiave BootROM è parte integrante dell’hardware interno della PlayStation, memorizzata in una memoria di sola lettura non riscrivibile fisicamente.
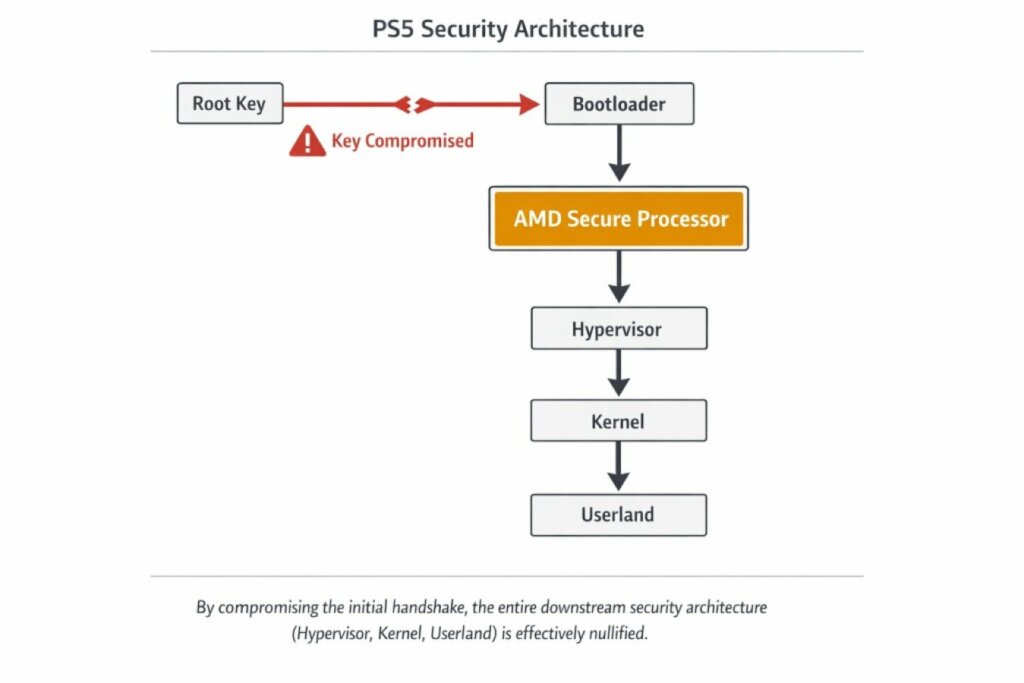
All’accensione, il sistema accede immediatamente a questa chiave per verificare la firma digitale del bootloader, che quindi procede all’inizializzazione del kernel del sistema operativo della console. Solo dopo aver completato con successo questi essenziali passaggi di verifica, Sony consente agli utenti di eseguire giochi e applicazioni acquistati legittimamente.
Prima di questa fuga di notizie, hacker e modder della console si concentravano principalmente sullo sfruttamento del kernel del sistema operativo di PlayStation 5 o sul browser basato su WebKit in esecuzione nello spazio utente, ma con scarso successo. Grazie all’accesso alla chiave BootROM, tuttavia, i ricercatori possono ora approfondire notevolmente l’architettura hardware e i meccanismi operativi della console.
Con questa chiave in mano, gli sviluppatori potrebbero finalmente essere in grado di creare firmware personalizzati, espandere l’ecosistema per la modifica e l’emulazione dei giochi e, cosa più importante, sbloccare alcuni titoli esclusivi Sony. Detto questo, le esclusive Sony sono in costante calo, con la maggior parte dei giochi moderni che ora vengono lanciati simultaneamente sulle piattaforme Sony, Microsoft e PC.
Per Sony, affrontare questo tipo di fuga di informazioni rappresenta una sfida significativa.
Essendo una chiave di sicurezza integrata nell’hardware, la BootROM non può essere facilmente sostituita. Tuttavia, Sony può introdurre nuove chiavi nelle future revisioni hardware, garantendo la sicurezza delle console di nuova produzione, senza che le funzionalità principali dei dispositivi esistenti vengano influenzate da eventuali rotazioni delle chiavi.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…