
Nel 2025, le comunità IT e della sicurezza sono in fermento per un solo nome: “React2Shell“. Con la divulgazione di una nuova vulnerabilità, CVE-2025-55182, classificata CVSS 10.0, sviluppatori ed esperti di sicurezza di tutto il mondo ne mettono in guardia dalla gravità, utilizzando persino il termine “2025 Log4Shell”.
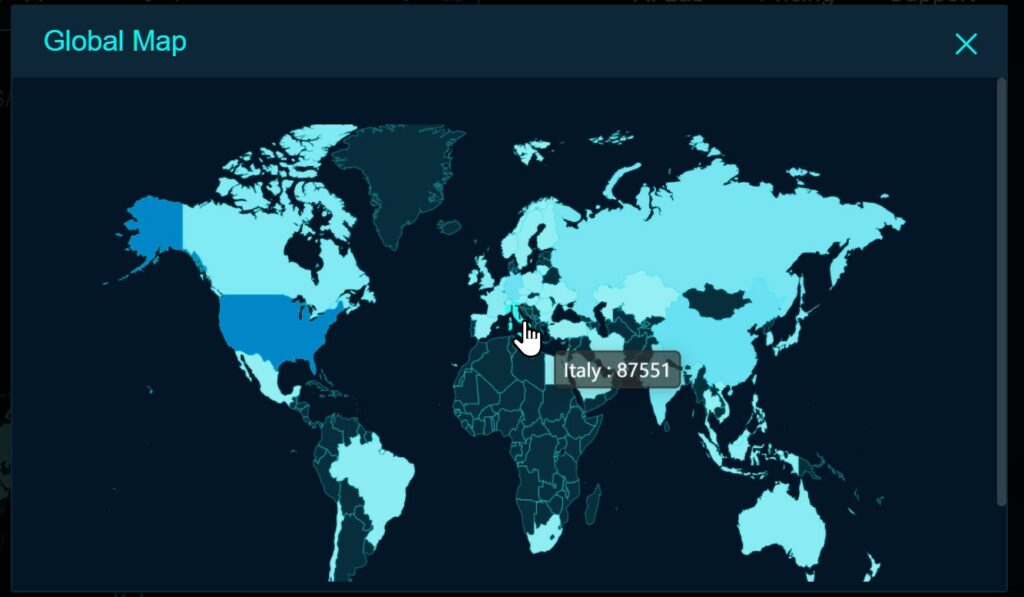
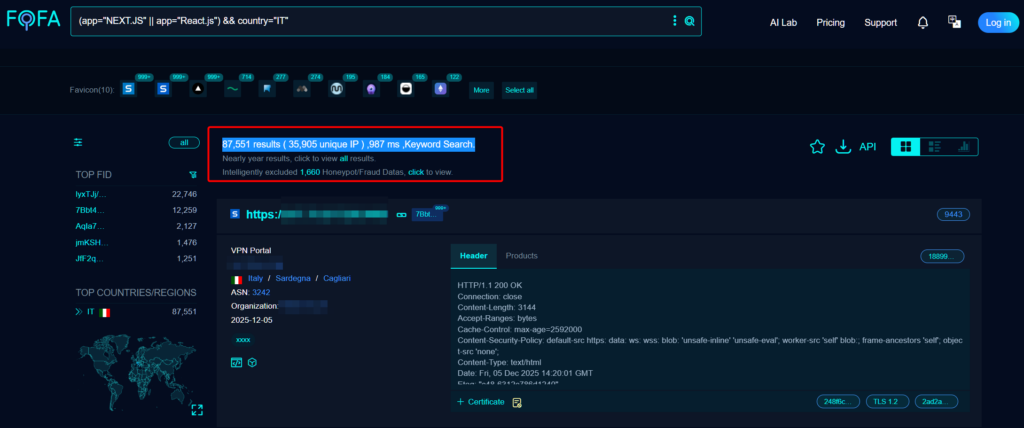
I server impattati da questa minaccia sono circa 8.777.000 nel mondo, mentre i server italiani sono circa 87.000. Questo fa comprendere, che con una severity da score 10, potrebbe essere una delle minacce più importante di tutto l’anno, che sta diventando “attiva”.
Infatti, è stato confermato che la comunità hacker cinese che sono stati già avviati test di attacco su larga scala sfruttando l’exploit per la vulnerabilità in questione sui server esposti. il CVE-2025-55182 non è semplicemente un bug software. È una falla strutturale nel protocollo di serializzazione RSC, che consente lo sfruttamento con la sola configurazione predefinita, senza errori da parte degli sviluppatori. L’autenticazione non è nemmeno richiesta.
Ecco perché gli esperti di sicurezza di tutto il mondo lo chiamano “la versione 2025 di Log4Shell”. Lo strumento di scansione delle vulnerabilità React2Shell Checker sta analizzando più percorsi e alcuni endpoint sono contrassegnati come Sicuri o Vulnerabili. L’immagine sopra mostra che diversi ricercatori stanno già eseguendo scansioni automatiche sui server basati su RSC.
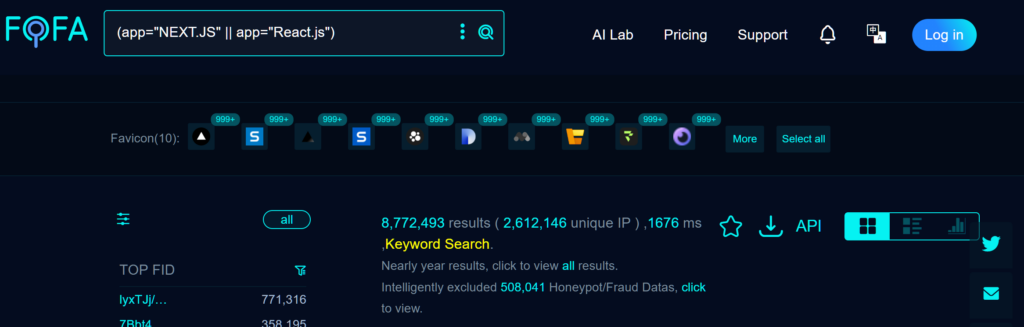
Il problema è che questi strumenti diventano armi che gli aggressori possono sfruttare. Gli hacker cinesi stanno conducendo con successo test RCE. Secondo i dati raccolti dalla comunità di hacker cinese, gli aggressori hanno già iniettato React2Shell PoC nei servizi basati su Next.js, raccolto i risultati con il servizio DNSLog e verificato il vettore di attacco.
Viene inviato un payload manipolato con Burp Repeater e il server crea un record DNS esterno. Ciò indica che l’attacco viene verificato in tempo reale. Gli aggressori hanno già completato i seguenti passaggi:
Non si tratta più di una “vulnerabilità teorica”, bensì della prova che è già stato sviluppato un vettore di attacco valido.
Gli hacker cinesi stanno in questi istanti eseguendo con successo le RCE.
l PoC sono stati pubblicati su GitHub e alcuni ricercatori lo hanno eseguito, confermando che la Calcolatrice di Windows (Calc.exe) è stata eseguita in remoto.
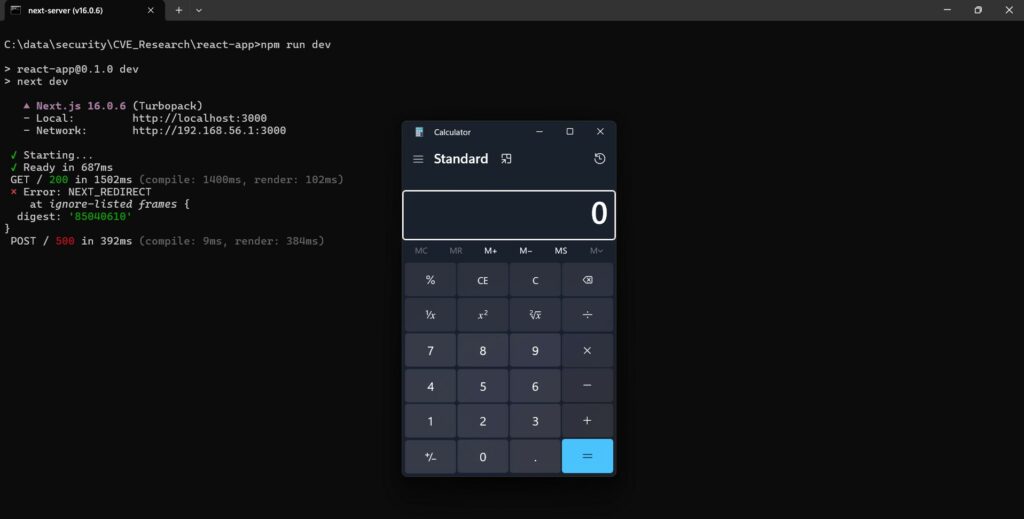
L’invio del payload tramite BurpSuite Repeater ha comportato l’esecuzione immediata di Calc.exe sul server. Ciò significa che è possibile l’esecuzione completa del codice remoto.
L’esecuzione remota della calcolatrice è un metodo di dimostrazione comune nella comunità di ricerca sulla sicurezza di un “RCE” riuscito, ovvero quando un aggressore ha preso il controllo di un server.
Gli 87.000 server riportati nella print screen di FOFA, dimostrano che un numero significativo di servizi web di aziende italiane che operano con funzioni RSC basate su React/Next.js attivate sono a rischio. Il problema è che la maggior parte di essi
In particolare, dato che i risultati della ricerca FOFA sono una fonte comune di informazioni utilizzata anche dai gruppi di hacker per selezionare gli obiettivi degli attacchi, è altamente probabile che questi server siano sotto scansioni attive.
Gli esperti definiscono questa vulnerabilità “senza precedenti” per i seguenti motivi:
Questa combinazione è molto simile all’incidente Log4Shell del 2021.
Tuttavia, a differenza di Log4Shell, che era limitato a Java Log4j, React2Shell è più serio in quanto prende di mira i framework utilizzati dall’intero ecosistema globale dei servizi web.
Gli Aggressori stanno già eseguendo la seguente routine di attacco.
Questa fase non è una pre-scansione, ma piuttosto la fase immediatamente precedente all’attacco. Dato il numero particolarmente elevato di server in Italia, la probabilità di attacchi RCE su larga scala contro istituzioni e aziende nazionali è molto alta. Strumenti di valutazione delle vulnerabilità e altri strumenti vengono caricati sulla comunità della sicurezza.
Gli esperti raccomandano misure di emergenza quali l’applicazione immediata di patch, la scansione delle vulnerabilità, l’analisi dei log e l’aggiornamento delle policy di blocco WAF.
Il team di React ha annunciato il 3 di aver rilasciato urgentemente una patch per risolvere il problema CVE-2025-55182, correggendo un difetto strutturale nel protocollo di serializzazione RSC. Tuttavia, a causa della natura strutturale di React, che non si aggiorna automaticamente, le vulnerabilità persistono a meno che aziende e organizzazioni di sviluppo non aggiornino e ricompilino manualmente le versioni.
In particolare, i servizi basati su Next.js richiedono un processo di ricostruzione e distribuzione dopo l’applicazione della patch di React, il che significa che probabilmente ci sarà un ritardo significativo prima che la patch di sicurezza effettiva venga implementata nell’ambiente del servizio. Gli esperti avvertono che “la patch è stata rilasciata, ma la maggior parte dei server è ancora a rischio”.
Molte applicazioni Next.js funzionano con RSC abilitato di default, spesso senza che nemmeno i team di sviluppo interni ne siano a conoscenza. Ciò richiede che le aziende ispezionino attentamente le proprie basi di codice per verificare l’utilizzo di componenti server e Server Actions. Con tentativi di scansione su larga scala già confermati in diversi paesi, tra cui la Corea, il rafforzamento delle policy di blocco è essenziale.
Inoltre, con la diffusione capillare di scanner automatici React2Shell e codici PoC in tutto il mondo, gli aggressori stanno eseguendo scansioni di massa dei server esposti anche in questo preciso momento. Di conseguenza, gli esperti di sicurezza hanno sottolineato che le aziende devono scansionare immediatamente i propri domini, sottodomini e istanze cloud utilizzando strumenti esterni di valutazione della superficie di attacco.
Hanno inoltre sottolineato che se nei log interni vengono rilevate tracce di chiamate DNSLog, un aumento di richieste POST multipart insolite o payload di grandi dimensioni inviati agli endpoint RSC, è molto probabile che si sia già verificato un tentativo di attacco o che sia stata raggiunta una compromissione parziale, il che richiede una risposta rapida.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…