
La scoperta è avvenuta casualmente: navigando sulla versione web mobile di Instagram, Jatin Banga ha notato che i contenuti di alcuni profili privati erano visibili senza alcuna autorizzazione.
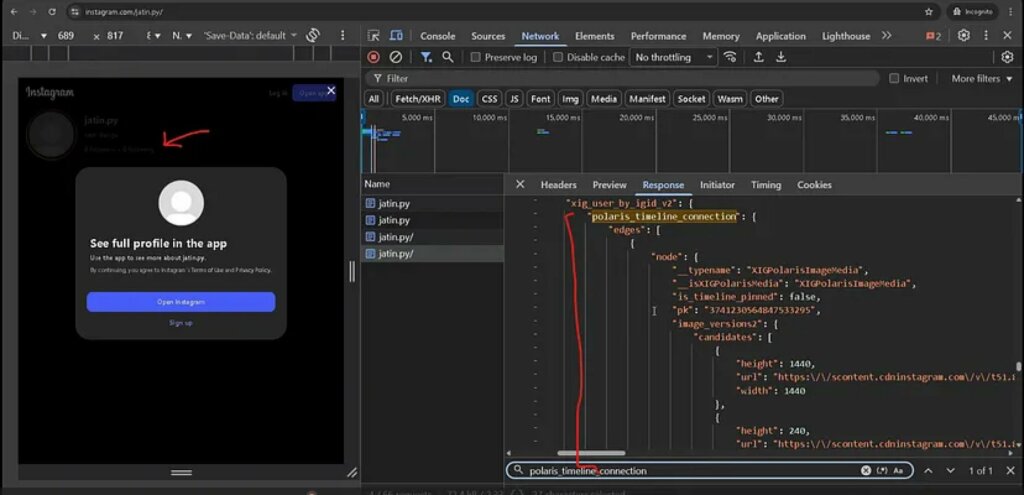
Analizzando il traffico dati, ha individuato la causa in una vulnerabilità del backend: inviando una semplice richiesta GET non autenticata a un profilo privato, il server restituiva un file HTML contenente un oggetto JSON chiamato polaris_timeline_connection.
Questo oggetto includeva i link diretti alla CDN di Instagram, permettendo di visualizzare foto e video a piena risoluzione. Il problema non riguardava la cache, ma un fallimento critico del server nel verificare i permessi di accesso prima di inviare i dati sensibili nel codice della pagina.
Banga ha condotto test mirati su account di sua proprietà o di persone che avevano fornito il consenso, scoprendo che la vulnerabilità era intermittente.
Non tutti i profili privati erano esposti: il bug si manifestava solo quando l’account si trovava in uno stato del server “anomalo”, rendendo la falla difficile da individuare ma estremamente pericolosa.
Il 12 ottobre 2025, Banga ha inviato un report dettagliato al programma Bug Bounty di Meta, allegando script in Python e prove video. Nonostante la documentazione, Meta ha inizialmente faticato a riprodurre il bug, chiudendo la segnalazione.
Banga ha dovuto insistere, fornendo ulteriori log di rete e dimostrando che il problema risiedeva nel controllo delle autorizzazioni lato server e non in comportamenti previsti dell’applicazione.
Il 16 ottobre 2025, Banga ha verificato che il bug era stato risolto: le richieste GET non restituivano più i dati privati. Tuttavia, Meta ha gestito il caso con poca trasparenza. Solo l’11 novembre, l’azienda ha risposto ufficialmente dichiarando il bug “Non Riproducibile” e chiudendo il report come “Non Applicabile” (negando quindi il premio economico).
La risposta di Meta: “Il fatto che un problema non riproducibile sia stato risolto non cambia il fatto che non fosse riproducibile al momento. Anche se il problema fosse riproducibile, è possibile che sia stata apportata una modifica per risolvere un problema diverso e che questo problema sia stato risolto come effetto collaterale indesiderato.”
Meta ha attribuito la scomparsa del bug a generiche “modifiche infrastrutturali”, ignorando le prove fornite dal ricercatore. Banga ha quindi reso pubblica la vicenda per sottolineare i rischi legati ai “bug condizionali” e criticare la gestione della sicurezza da parte di piattaforme che ospitano i dati sensibili di miliardi di persone.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…