
SonicWall ha confermato che il mese scorso una violazione dei dati ha interessato tutti i clienti che utilizzavano il servizio di backup cloud dell’azienda. Di conseguenza, le configurazioni del firewall memorizzate in MySonicWall sono state compromesse.
MySonicWall è un portale per i clienti SonicWall che consente loro di gestire l’accesso ai prodotti, le licenze, la registrazione, gli aggiornamenti del firmware, le richieste di supporto e i backup cloud delle configurazioni del firewall (file .EXP).
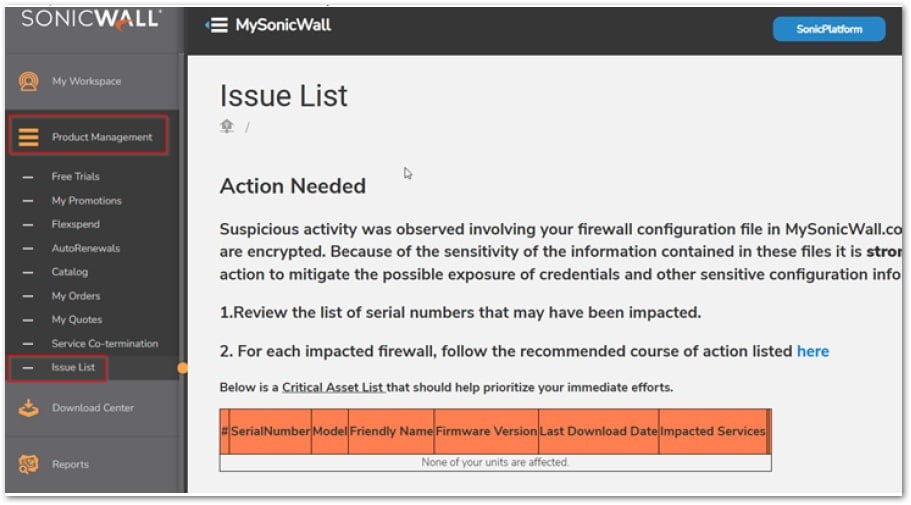
Si consiglia agli utenti di seguire immediatamente i passaggi sottostanti:
A metà settembre 2025, SonicWall ha esortato i propri clienti a modificare le proprie credenziali di accesso il prima possibile, poiché un attacco informatico agli account MySonicWall aveva compromesso i file di backup della configurazione del firewall.
All’epoca, i dettagli dell’attacco non furono divulgati e SonicWall dichiarò di aver bloccato l’accesso degli aggressori ai sistemi dell’azienda e di aver già collaborato con le agenzie di sicurezza informatica e le forze dell’ordine.
L’azienda ha pubblicato raccomandazioni dettagliate pensate per aiutare gli amministratori a ridurre al minimo i rischi di sfruttamento di configurazioni rubate. In particolare, ha raccomandato di riconfigurare il prima possibile i segreti e le password potenzialmente compromessi e di monitorare le potenziali attività degli aggressori.
All’epoca, il fornitore aveva riferito che circa il 5% dei suoi clienti totali utilizzava il servizio di backup su cloud, ma l’attacco aveva colpito solo “alcuni account”.
In un aggiornamento pubblicato questa settimana, SonicWall ha avvisato che l’incidente ha interessato tutti i clienti che utilizzavano un portale cloud per archiviare i file di configurazione del firewall.
“SonicWall ha completato l’indagine, condotta in collaborazione con Mandiant, azienda leader nella gestione delle relazioni con i clienti, sulla portata di un recente incidente di sicurezza relativo al backup su cloud. L’indagine ha confermato che una parte non autorizzata ha avuto accesso ai file di backup della configurazione del firewall di tutti i clienti che hanno utilizzato il servizio di backup su cloud di SonicWall. I file contengono credenziali e dati di configurazione crittografati; sebbene la crittografia rimanga attiva, il possesso di questi file potrebbe aumentare il rischio di attacchi mirati. Stiamo lavorando per informare tutti i partner e i clienti interessati e abbiamo rilasciato strumenti per supportare la valutazione e la risoluzione dei problemi dei dispositivi. Gli elenchi finali aggiornati e completi dei dispositivi interessati sono ora disponibili sul portale MySonicWall (accedere a Gestione Prodotti > Elenco Problemi).”
Si sottolinea che i file compromessi contengono credenziali e dati di configurazione crittografati con AES-256.
Gli utenti possono verificare se i loro dispositivi sono interessati accedendo a MySonicWall e andando su Gestione Prodotti -> Elenco Problemi. In caso di problemi in sospeso, gli utenti devono seguire i passaggi indicati nella guida Essential Credential Reset, dando priorità ai firewall attivi con accesso a Internet.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…