
I ricercatori di Varonis hanno scoperto una nuova piattaforma PhaaS, chiamata Spiderman , che prende di mira gli utenti di banche e servizi di criptovaluta in Europa. Gli aggressori utilizzano il servizio per creare copie di siti web legittimi per rubare credenziali di accesso, codici 2FA e informazioni sulle carte di credito.
Secondo gli esperti, la piattaforma è rivolta a istituti finanziari di cinque paesi europei e a grandi banche come Deutsche Bank, ING, Comdirect, Blau, O2, CaixaBank, Volksbank e Commerzbank.
Tuttavia, gli attacchi non si limitano alle banche.
Spiderman può anche creare pagine di phishing per servizi fintech come Klarna e PayPal in Svezia. Inoltre, la piattaforma supporta il furto di seed per wallet di criptovalute come Ledger, Metamask ed Exodus.
“Poiché Spiderman è modulare, può facilmente adattarsi a nuove banche, portali e metodi di autenticazione. Man mano che i paesi europei aggiornano i loro sistemi di online banking, è probabile che il servizio si evolverà parallelamente”, osservano i ricercatori di Varonis.
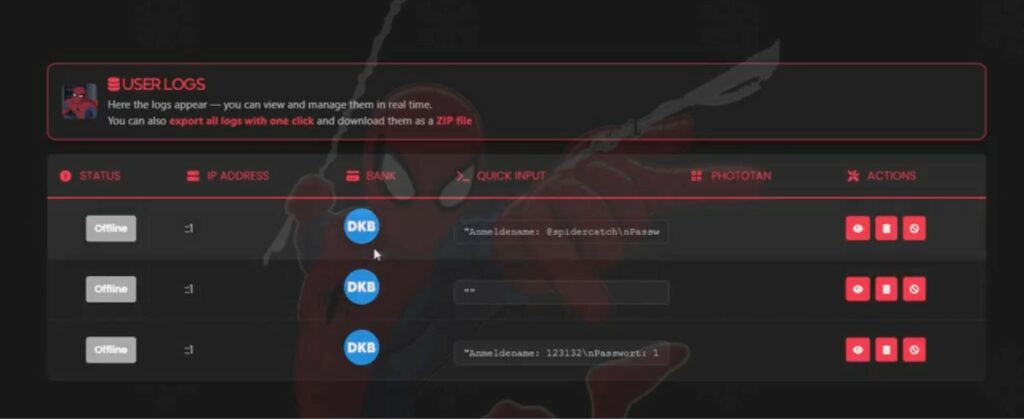
Attraverso la dashboard web di Spiderman, gli operatori possono monitorare le sessioni delle vittime in tempo reale, esportare i dati con un solo clic, intercettare al volo credenziali, PhotoTAN e password monouso e raccogliere informazioni sulle carte di credito.
PhotoTAN è un sistema di password monouso ampiamente utilizzato dalle banche europee. Quando si effettua l’accesso o si conferma una transazione, all’utente viene mostrato un mosaico colorato che deve essere scansionato tramite l’app della banca. L’app decripta il mosaico, genera un codice OTP per la transazione specifica e l’utente inserisce questo codice sul sito web.
Gli operatori di Spiderman hanno anche accesso alle impostazioni di targeting tramite il pannello di controllo: possono limitare gli attacchi a paesi specifici, inserire i provider nella whitelist, filtrare le vittime in base al tipo di dispositivo (utenti mobili o desktop) e impostare reindirizzamenti per i visitatori non adatti al phishing.
I ricercatori sottolineano che tutti i kit di phishing si basano sul fatto che la vittima clicchi su un link e venga reindirizzata a una pagina di accesso falsa.
Pertanto, la migliore difesa contro tali attacchi è controllare sempre attentamente il dominio prima di inserire le proprie credenziali. Vale anche la pena prestare attenzione alle finestre “browser-in-the-browser” false , che potrebbero visualizzare l’URL corretto.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…