
We often talk about “Malware”. But even today, many people don’t fully understand the real meaning of this word. With this article, we want to explain precisely what malware is, the main types and their differences, so as to no longer confuse them and to understand them more precisely.
The word malware comes from the English language, from the union of two words: MALicious and softWARE, which means “malicious software”, or code capable of causing damage, or guaranteeing an advantage to its creator.
But to fully understand the evolution of “malware”; We need to go back in time, when in 1949, the mathematician John von Neumann, theorized the possibility of building computer programs that could self-replicate autonomously.

The American mathematician John von Neumann, who theorized the concept of a self-replicating virus.
The concept of a self-replicating program found its practical evolution in the early 1960s, in a game devised by a group of programmers at AT&T’s Bell Labs called “Core War,” in which multiple programs had to defeat each other by overwriting each other. A computer virus is in fact a program that recursively (and explicitly) copies a possibly evolved version of itself, thus starting an infection.
In 1971, Bob Thomas, an engineer at BBN technology, wrote the famous Creeper, a self-replicating program created for DEC PDP-10 terminals running the TENEX operating system.
Creeper was not actually malicious software and was not sophisticated. Once started, it did nothing more than write the message «I’M THE CREEPER: CATCH ME IF YOU CAN.» on the screen, then started printing a file and jumped to another computer performing the same previous operations. Creeper, we can say that it was a simple PoC, what is called today Proof of concept, that is, a “sketched” version of an idea or concept, capable of making people understand that what had been hypothesized was actually possible.
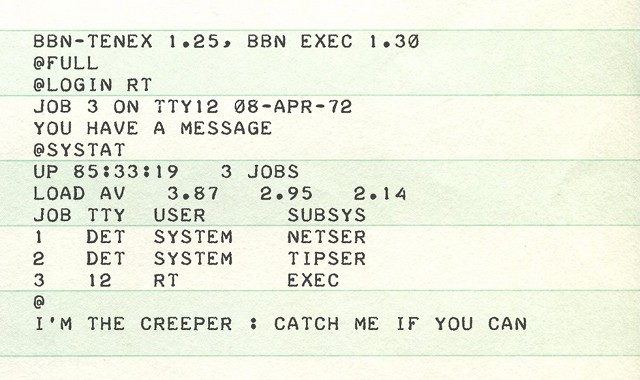
File printed by Creeper once running.
Creeper was not exactly a virus, in fact we speak of a worm, analyzing it with modern terminology, because it did not replicate on other machines but physically jumped from a computer to another. This code had laid the foundation for an idea that would soon become a “computer security” problem. But at that time the term virus was not yet associated with these programs.
In 1972, David Gerrold, a science fiction writer, used the word VIRUS to describe a computer program that behaved like biological viruses in his novel The God Machine.

Subsequently, in 1973 the phrase “computer virus” was used in the film World of Robots as well as in the X-Men comic book n. 158, published in 1982.
On November 10, 1983, Fred Cohen, a student at Southern California University, took an “academic” look at the digital future by demonstrating how a computer virus works at a computer security seminar. To demonstrate its functionality, Cohen ran his code inside a computer and within five minutes of booting, he had gained complete control of the system.
The program had managed to “infect” computers by making copies of itself, spreading from one machine to another by hiding inside a larger, legitimate program, which was loaded onto a computer via a diskette.
Cohen described this behavior as a “self-replicating computer virus,” effectively coining the term for the first time in academia, even though it was already quite common in spoken language.
But Cohen’s malware wasn’t the first of its kind.
Rich Skrenta, a 15-year-old boy from Pennsylvania, beat Cohen by just one year. Skrenta had a penchant for playing pranks on his friends and added code to the game programs of the very popular Apple II that would shut down their computers or do other annoying and bizarre things.

It was 1982, when he developed the program that was called Elk Cloner, credited as the first computer virus that appeared in the world.
The program ran on Apple’s DOS 3.3 and the infection was propagated through the exchange of floppy disks.
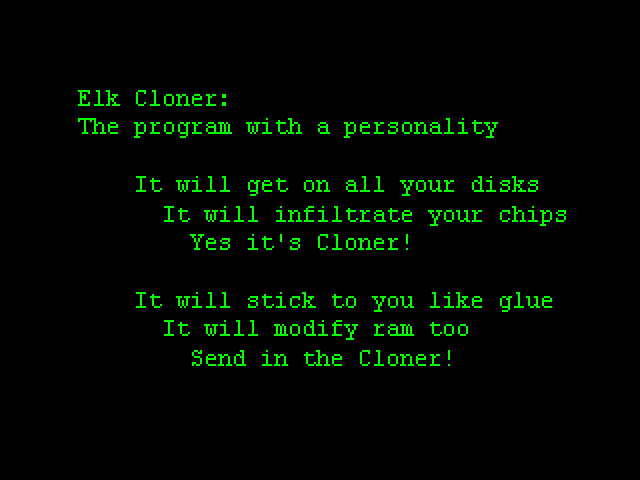
The virus was present on a floppy disk that contained some games. After the fiftieth time that floppy disk was started, the program was copied to the computer’s master boot, so that every time it started it would display the message “I am Elk Cloner, a program with a personality”
From then on, the story is quite well known as we have all had to deal with computer viruses and antiviruses.
As time went by, the word virus became more and more specialized, also in consideration of the evolution of computer security and threats.
So here is what the virus soon became a worm, and then became a Trojan, rootkit, ransomware, adware and much, much more.
Many of these “specializations” are still confused by many people today, but with this article we will analyze the most widespread forms, in order to understand the differences well and know their genesis and nature.
The Trojan class takes its name from the way in which the program penetrates a system, presenting itself as a useful and apparently harmless software (Trojan horse).
The user executes it of its own free will, also starting the malware’s functions at the same time. Trojans are also called RATs, an acronym for Remote Administration Tool/Trojan, which are generally composed of two components, a server and a client, to allow remote control of the infected computer and then send the instructions to be executed.
There are many variants of Trojans, which allow different control modes capable of all types of compromises.
The first Trojan in history was Gotcha, which appeared in 1985 and was capable of causing a lot of damage. The program presented itself as a graphical file viewer, while its intent was to delete all data on the disk.
The virus class can often be confused with other types of malware, but the discriminating factor is the propagation model.
In fact, once executed, the computer virus infects other files in order to make copies of itself, generally without being detected by the user. Normally, a virus is distributed within an executable and spreads once launched by infecting another executable, without the user’s knowledge.
The virus credited as the first in history, as we have seen previously, is Elk Cloner, which is often confused with the Creeperworm, (which is not the monster from the Minecraft video game). It is important to underline that the difference is made by the propagation method that discriminates the typology, the first self-replicating, the second, self-propagating, that is, it executes a copy of itself autonomously, without using another executable as an infection vector.
Ransomware is that class of malware that limits access to the device it infects, requiring a ransom to be paid to remove this limitation.
Today’s ransomware blocks the system and to prevent the user from being able to somehow restore access, it encrypts the data and asks for a ransom for the recovery and decryption of the data. data.
Furthermore, for some time now, cybercrime has been organizing itself into RaaS (Ransomware as a Service), inspired by cloud services. This Ransomware can be used even by those without malware or hacking skills. These operators working in the darknet (such as Maze, Revil, Darkside), also exfiltrate data from compromised servers so that if the ransom is not paid, they always have an additional form of blackmail towards the victim for the publication of the data and intellectual property stolen from their infrastructure.
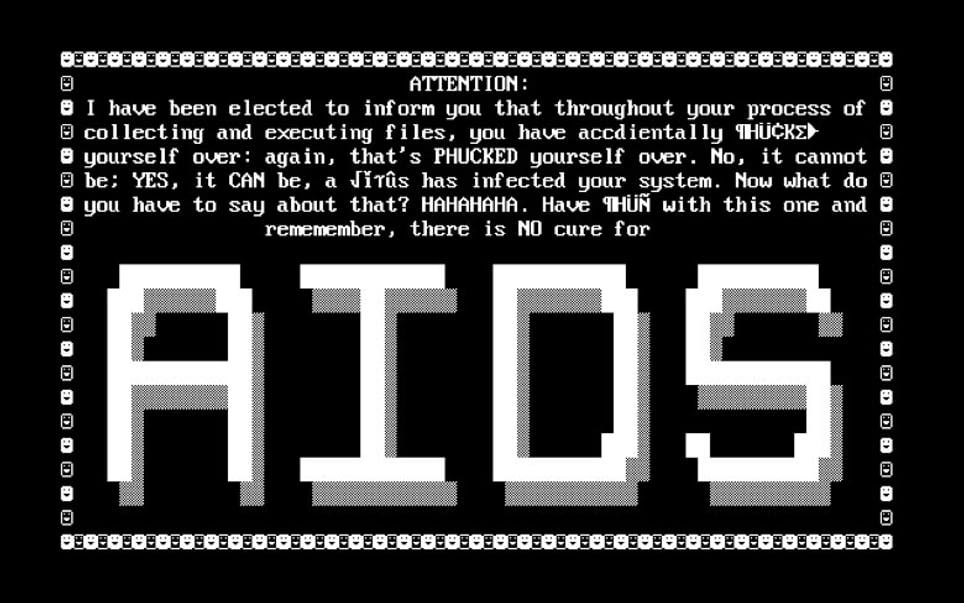
Screenshot once the Trojan AIDS ransomware has been executed.
The first ransomware was the AIDS Trojan, also known as “PC Cyborg”, written in 1989 by biologist Joseph Popp, which executed a payload that showed the user a message that a license for an installed software had expired. Immediately afterward, it encrypted the files on the hard disk and forced the user to pay $189 to the “PC Cyborg Corporation” to unlock the system.
Ransomware is often used at the end of an attack, often initiated using RATs to initially compromise the infrastructure, or once persistence has been acquired through the use of access brokers. If you want to better understand how RaaS works, read the articles on this topic on RedHotCyber.
The Worms class represents that group of malware that can self-replicate autonomously. Be careful because they are often confused with viruses. In fact, viruses self-replicate, but they do so by infecting other files. The most common means used by worms to spread is email, like many other malware.
In fact, the worm searches for email addresses stored on the host computer and sends a copy of itself as an attachment to all or some of the addresses it has managed to collect.

The diskette containing the “morris” worm, the first in history on the Internet.
The first computer worm in history was written by Tappan Morris, in 1988, a student at Cornell University, Robert Purcell, and was launched on November 2, 1988, from the MIT laboratory. Morris wrote the worm because he wanted to calculate the size of the ARPANet network. Fifteen hours after its launch, it infected 6,000 Unix servers out of a total of 60,000 on the ARPANet network. Morris went down in history both for creating the first worm, but also for leading its creator to the first conviction for computer piracy in the United States.
In computing, spyware is a type of software that collects information about a user’s online activity without their explicit consent.
Spyware, born in the era of Windows XP and Internet Explorer, are generally present within other software, within Mobile APPs or designed (in the most sophisticated cases) to be made available to intelligence agencies and governments of nations, as we have already seen in a video on the YouTube channel “zeroday tra broker e spionaggio”.
These programs allow you to intercept messages, allow access to phone information, the address book, photo galleries, where some can have access to the microphone and camera. In short, they are really dangerous.
Spyware, unlike viruses and worms, cannot spread autonomously, so they generally require user intervention, in fact very similar to Trojans which use, for example, social engineering techniques or known security vulnerabilities, and even unknown ones, such as the famous zerodays.
The word spyware appeared for the first time in 1995 on Usenet, a computer discussion forum, following a discussion on Microsoft’s business model and was then taken up again in 1999 by Gibson Research.
In addition to endless scandals, Italy also had its own scandal regarding smartphone spyware with Exodus, produced by the Calabrian company eSurv in 2018 and then used on 1000 users by the state police as part of a series of judicial investigations.
Unfortunately, spyware is the scourge of the internet today. We have often quoted the great Bruche Shneier and his famous phrase “the internet’s business model is surveillance” and how can we blame him?
How many times has it happened to you that while browsing with your favorite browser, a series of windows have opened in an uncontrolled manner and even though you tried to close them, the windows have not taken long to disappear?
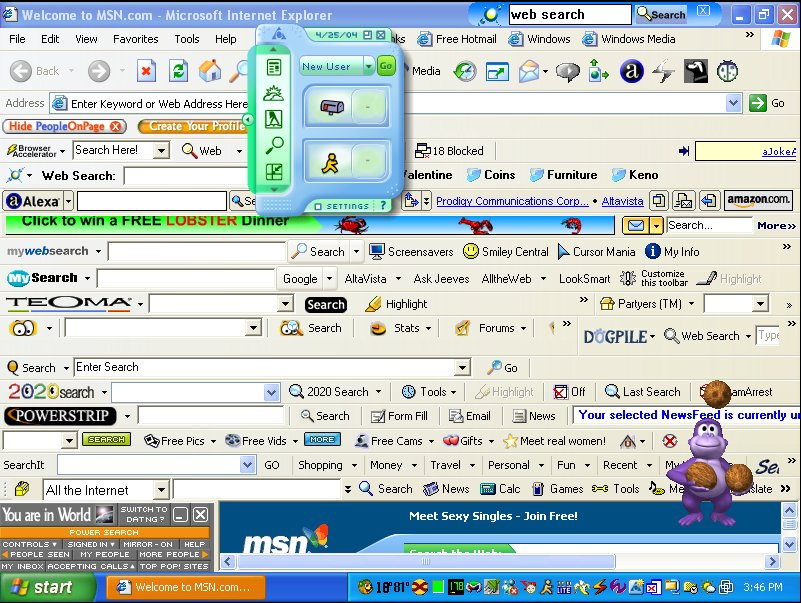
Internet Explorer infested with Adware.
This is Adware, or malware designed to make advertising, which ensures the display of advertisements purposely exposed to the user, with commercial purposes.
There are many different types, from those designed to modify the HTML within the Browser, to those residing within the extensions of the browser, to those contained within Mobile APPs, in short, a real jungle.
Surely slow navigation, banners published on websites where you had never seen them before, the homepage changed from the one set and pop-up windows continuously open, are all good clues to think that your computer has been infected by an AdWare.
There are many types of AdWare, but we can mention some famous ones such as Fireball, DollarRevenue, Gator, DeskAd,
By rootkit, we mean refers to a program designed to allow a cybercriminal to administer a system by previously installing it, without the user’s knowledge.
Generally, a rootkit is installed automatically, or an attacker may be able to install it once they have obtained root permissions or administrative access to the system.
Obtaining this type of access can occur directly to the system, or by using Privilege Escalation vulnerabilities that represent an elevation of privileges compared to a non-administrative user.
Directly, however, means after having obtained the password, through cracking, brute-forcing, or social engineering of the administrator account.
These malware first appeared in the 1990s. Rootkits initially targeted Linux systems, in fact they are referred to as “root,” which is the UNIX superuser who, by default, has access to all files and commands on a system.
The malware is associated with the word “Kit,” which is in fact the software that guarantees its persistence and access.
A backdoor (from the English service door or back door) is software that allows you to bypass normal authentication in a computer system.
Backdoors can hide inside any program and are generally designed to be undetectable by firewalls, but in fact allow access to system functions silently and hidden.
They can be installed on a system or developed within it, to allow maintenance activities of the software itself up to industrial espionage activities or used by intelligence agencies and governments of countries.
But be careful, the term Backdoor does not indicate a distribution model, as they can be transported by RootKits, Trojans or Viruses.
The Cult of the Dead Cow hacker group, which invented the term Hacktivism and participated in the creation of the TOR software, created in 1998 the famous Back Orifice, a remote administration tool that allowed remote control of Windows computers on a network.

Presentation of Backorifice at the Hacker event in 2000.
This name was a reference to, let’s say it as we say now, “trolling” the well-known Microsoft suite of that period, Microsoft BackOffice.
In this article, we analyzed 8 classes of malware, among the most well-known ones, but there are many other types of Malware that we will not discuss, such as grayware, rabbits, and many other old and new malware that will take shape over time from the imagination of hackers.
The best weapon to defend yourself from malware is to always be wary of any software offered for free on the Internet, and of attachments sent via email from unknown people, and always keep this in mind.
But it is also possible to protect yourself from malware through software solutions such as antivirus software, so choose one, preferably a paid one, to have good protection and always keep it updated.
But since zero risk does not exist, be careful guys, always keep your eyes open!
Follow us on Google News to receive daily updates on cybersecurity. Contact us if you would like to report news, insights or content for publication.
