
PixelCode nasce come progetto di ricerca che esplora una tecnica nascosta per archiviare dati binari all’interno di immagini o video. Invece di lasciare un eseguibile in chiaro, il file viene convertito in dati pixel, trasformando ogni byte in una struttura di colore. La tecnica cambia completamente il modo in cui consideriamo file grafici e video, mostrandoli come potenziali vettori di dati binari senza esporne il contenuto reale.
Il concetto alla base è semplice nella sua idea, ma complesso nella realizzazione: convertire un programma eseguibile in una mappa visiva.
Questo “codice pixel” può poi essere memorizzato dentro un’immagine o un video, rendendolo apparentemente innocuo agli occhi di strumenti di scansione tradizionali che non analizzano il contenuto visivo alla ricerca di dati eseguibili.
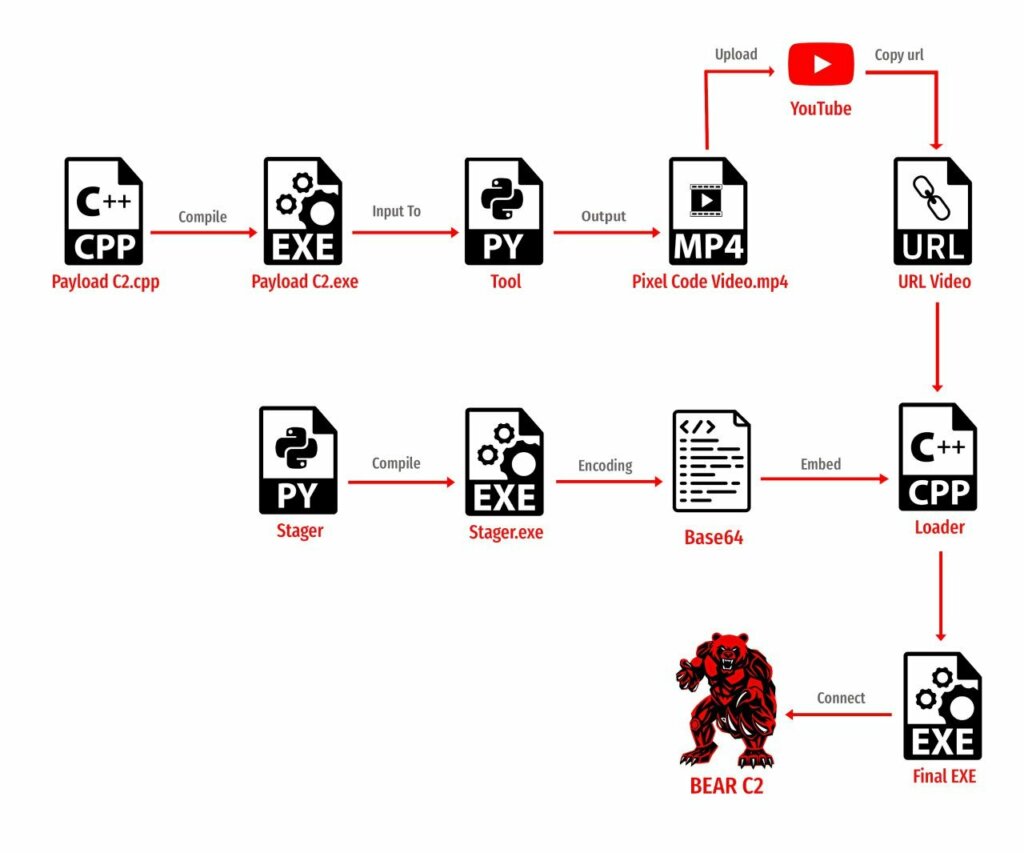
Il progetto documenta un processo in più fasi. La prima prevede un payload in C++ progettato per comunicazioni di comando e controllo, compilato in un eseguibile standard. Questo eseguibile non viene distribuito così com’è, ma convertito in un video MP4 mediante uno strumento Python dedicato.
Una volta generato il video con il “Pixel Code”, esso può essere caricato su piattaforme pubbliche come servizi di condivisione video. La playlist ospita così un file apparentemente innocuo, un video qualsiasi, che in realtà contiene dati binari pronti a essere estratti.
Il passo successivo utilizza un loader C++ che include l’URL del video. Questo loader, quando avviato su un sistema, scarica il video e chiama un piccolo stager Python, anche esso incorporato nel loader, per riconvertire i pixel nei byte originali.
Questa tecnica apre scenari insoliti: file multimediali caricati su servizi fidati possono servire a trasportare dati che sfuggono a filtri di sicurezza tradizionali, che tendono a concentrarsi su EXE o script espliciti. L’idea sottostante è che i video non siano soggetti alle stesse scansioni rigorose di file binari.
L’esecuzione in memoria del payload ricostruito evita la scrittura su disco di file potenzialmente sospetti, complicando l’individuazione e la rimozione tramite antivirus o sistemi di rilevamento comportamento.

Questo progetto non è un attacco reale ma una dimostrazione di ricerca e consapevolezza, usata per evidenziare come tecniche non convenzionali possano essere sfruttate per la consegna di codice.
Verso la fine del documento, gli autori sottolineano che la tecnica è solo per scopi educativi e di ricerca, e non devono essere usati in modi che violano leggi – e qui si inquadra S3N4T0R-0X0/Malicious-PixelCode come esempio di ricerca avanzata.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…