
Nel monitoraggio quotidiano dei forum underground capita spesso di imbattersi in leak che, almeno a una prima lettura, sembrano “ordinari”: liste di credenziali, accessi a servizi legacy, dump poco strutturati. Il thread “NEW LEAK FTP LOGIN” comparso su un forum underground rientra formalmente in questa categoria, ma presenta una serie di elementi che meritano attenzione, soprattutto per l’impatto potenziale sul contesto italiano.
Il post è stato pubblicato da un utente che si presenta con il nickname Hackfut e contiene un elenco molto esteso di credenziali FTP, pubblicate in chiaro e apparentemente ancora valide. Non si tratta di un singolo dump isolato, ma di una raccolta ampia, eterogenea, che tocca numerosi domini e infrastrutture reali.
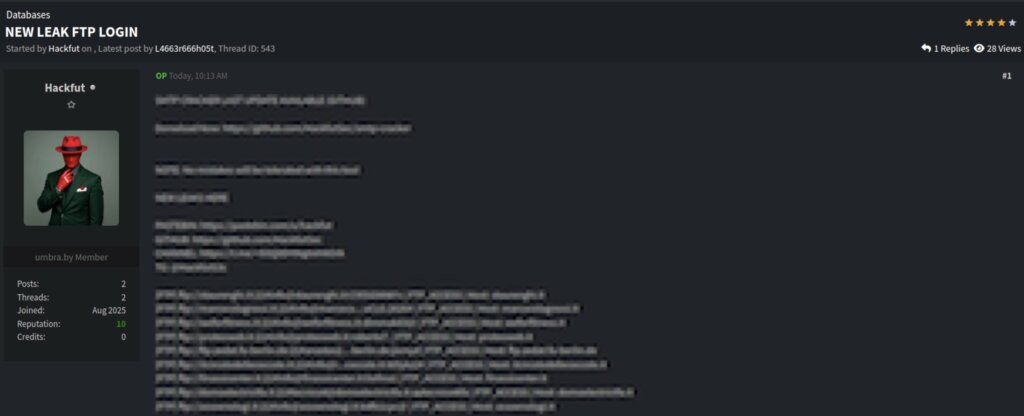
Già da una lettura superficiale emerge un primo dato rilevante: la presenza di un numero elevato di domini italiani .it. Un elemento che, per chi segue da tempo le dinamiche di compromissione di hosting e servizi web in Italia, purtroppo non rappresenta una sorpresa, ma continua a confermare una fragilità strutturale mai realmente risolta.
Il valore operativo di questo tipo di leak non sta nella raffinatezza tecnica, ma nella prontezza all’uso. Le credenziali FTP, se valide, consentono un accesso diretto a:
Non servono exploit avanzati, né competenze particolarmente elevate. È esattamente questo il motivo per cui gli accessi FTP continuano a essere una commodity molto appetibile nel sottobosco cybercriminale: basso costo, basso rischio, ritorno immediato.
Il thread non si limita a pubblicare la lista, ma inserisce anche riferimenti a risorse esterne – repository GitHub, Pastebin e canali Telegram – costruendo di fatto una filiera completa: leak → verifica → sfruttamento → redistribuzione.
Analizzando le risorse collegate al post emerge un pattern ormai consolidato. L’account GitHub associato a HackfutSec ospita script e tool orientati all’automazione di test massivi, in particolare su servizi FTP e SMTP. Non parliamo di codice particolarmente sofisticato, ma di strumenti sufficienti per:
Parallelamente, la pagina Pastebin riconducibile allo stesso alias mostra una storia di pubblicazioni ricorrenti legate a leak di FTP, webmail e pannelli di controllo. Questo suggerisce che il thread su Umbra.by non sia un episodio isolato, ma parte di un’attività continuativa di raccolta e redistribuzione di accessi.
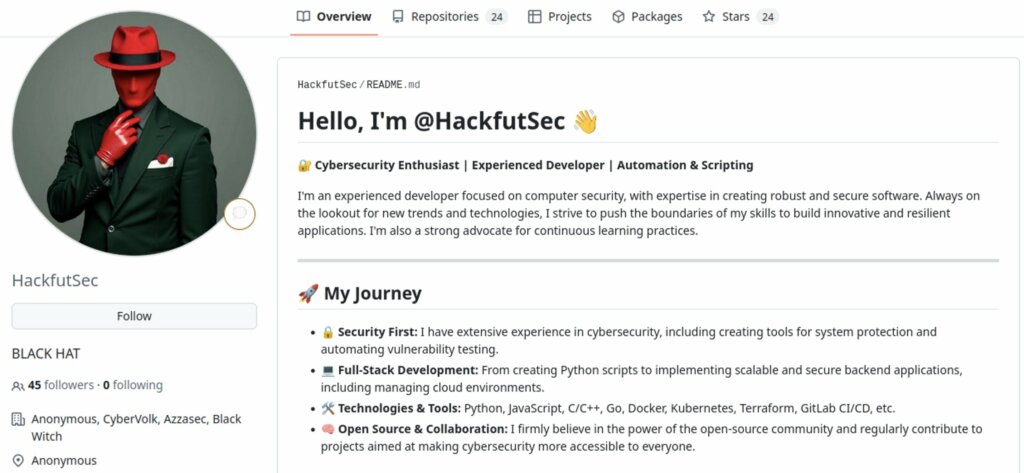
Dal punto di vista CTI, il profilo è chiaro: non un singolo “leaker occasionale”, ma un operatore orientato alla quantità, che lavora su servizi legacy e superfici d’attacco trascurate.
L’aspetto più critico del leak resta la forte concentrazione di domini italiani. Hosting condivisi, siti di PMI, associazioni, studi professionali: un panorama già visto molte volte. Tuttavia, all’interno della lista compare anche un riferimento a un account FTP riconducibile ad un grande ospedale italiano.
È importante essere precisi: la presenza di un dominio in una lista non equivale automaticamente a una compromissione attiva. Le credenziali potrebbero essere obsolete, disattivate o già ruotate. Ma il solo fatto che un’infrastruttura sanitaria compaia in un contesto del genere è sufficiente a giustificare un’attenzione immediata.
Quando un accesso FTP riguarda un ente sanitario, le implicazioni non sono solo tecniche:
Ancora una volta, il problema non è il singolo leak, ma la persistenza di servizi obsoleti e poco monitorati.
Questo episodio conferma un dato che emerge costantemente nel threat landscape: FTP in chiaro è tutt’altro che scomparso. In molti casi resta attivo per inerzia, compatibilità con vecchi flussi di lavoro o semplice mancanza di revisione delle superfici esposte.
Le condizioni che favoriscono questo tipo di leak sono quasi sempre le stesse:
Il risultato è una lunga coda di accessi che, prima o poi, finiscono in una combolist, su Pastebin o su un forum underground.
Il thread “NEW LEAK FTP LOGIN” su Umbra.by non introduce nulla di “nuovo” dal punto di vista tecnico. Ma proprio per questo è importante: mostra quanto siano ancora efficaci gli attacchi più banali, quando colpiscono infrastrutture trascurate.
Per l’Italia, il segnale è chiaro e ripetuto: una parte significativa del tessuto digitale continua a poggiare su servizi legacy esposti, facilmente enumerabili e scarsamente difesi. Questi leak non fanno notizia come un ransomware, ma alimentano l’intera catena criminale, fornendo accessi iniziali, punti di appoggio e superfici di persistenza.
In altre parole: prima del ransomware, prima dell’estorsione, prima del data breach “da prima pagina”, c’è quasi sempre un accesso semplice che nessuno ha chiuso.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…