
Nel panorama delle minacce informatiche, pochi malware sono tanto persistenti e diffusi quanto Formbook. Nato come un semplice keylogger e form-grabber, si è evoluto in un potente infostealer venduto secondo il modello Malware-as-a-Service (MaaS), rendendolo accessibile a un’ampia platea di criminali informatici. La sua capacità di esfiltrare credenziali dai browser, client email e altri software lo rende uno strumento prediletto per ottenere un accesso iniziale alle reti aziendali.
In questo articolo, analizzeremo il sample di un dropper multi-stadio progettato per distribuire l’infostealer Formbook, e, a partire dalle evidenze raccolte, illustreremo le contromisure proposte da ELMI per prevenire, rilevare e rispondere a questa tipologia di minacce.
ELMI opera nel settore IT come System Integrator da quarant’anni, offrendo consulenza professionale e supportando aziende private e pubbliche nello sviluppo di progetti innovativi.
Attualmente, l’azienda è fortemente focalizzata sui temi della Digital Transformation, con particolare riferimento alle aree tecnologiche inerenti la Digitalizzazione dei processi, la Cyber Security, l’Asset Management, l’Intelligenza Artificiale generativa e la Blockchain.
Infostealer in azione: analisi tecnica di Formbook
Come osservato in diverse campagne recenti documentate anche dall’Agenzia per la Cybersicurezza Nazionale (ACN), la distribuzione di Formbook avviene principalmente tramite malspam (Malware Spam o Malicious Spam): email malevole confezionate per sembrare legittime (finte fatture, documenti di spedizione, preventivi o comunicazioni aziendali). Il messaggio contiene tipicamente un allegato (archivi compressi .zip/.rar o file Office con macro disabilitate) o un link che, una volta cliccato, porta al download di un file JavaScript offuscato. È proprio questo file, nel campione analizzato, a costituire il dropper iniziale che dà avvio alla catena di infezione.
L’obiettivo della fase iniziale è indurre l’utente a eseguire manualmente l’allegato — affidandosi quindi alla componente di ingegneria sociale più che a vulnerabilità software. Questo approccio, combinato con tecniche di offuscamento del codice e l’uso di servizi cloud legittimi per ospitare i payload successivi, rende la campagna particolarmente insidiosa e difficile da bloccare con i soli controlli perimetrali.
L’analisi è quindi partita da un campione JavaScript, rivelando una catena di infezione complessa che impiega PowerShell come stadio intermedio e culmina con l’esecuzione “fileless” del payload finale. L’attore della minaccia ha implementato molteplici tecniche di offuscamento ed evasione, e ha sfruttato un servizio legittimo (Google Drive) per ospitare il payload, rendendo il rilevamento basato sulla rete più difficile.
Questa analisi documenta in dettaglio ogni fase, mappando le Tattiche, Tecniche e Procedure (TTPs) osservate sul framework MITRE ATT&CK e fornendo gli Indicatori di Compromissione (IoCs) necessari per il rilevamento e la mitigazione.
L’obiettivo non è solo sezionare il malware, ma capire come un singolo file si inserisca nell’enorme ecosistema del cybercrime, alimentando il mercato nero dei dati e come possa impattare significativamente l’operatività e la riservatezza dei sistemi.
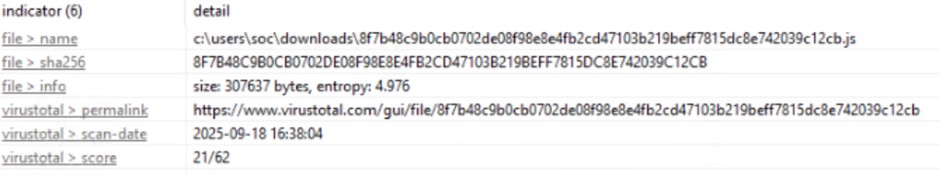
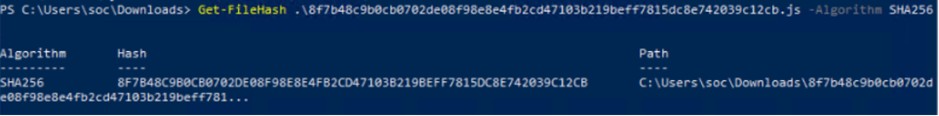
Nome File 8f7b48c9b0cb0702de08f98e8e4fb2cd47103b219beff7815dc8e742039c12cb.js
Tipo File .js
SHA256 8f7b48c9b0cb0702de08f98e8e4fb2cd47103b219beff7815dc8e742039c12cb
Dimensione 300 KB
Entropia 4976
Catena d’infezione di Formbook: dal phishing all’esecuzione fileless
L’attacco si sviluppa attraverso una catena di eventi ben definita, progettata per aumentare la furtività e la probabilità di successo dell’infezione.
Il campione iniziale viene veicolato tramite campagne malspam , una delle tecniche di distribuzione più comuni per Formbook, come documentato anche dall’ACN. L’efficacia di questa prima fase non si basa su vulnerabilità software, ma interamente sull’ingegneria sociale, studiata per ingannare e indurre l’utente a compiere un’azione decisiva.
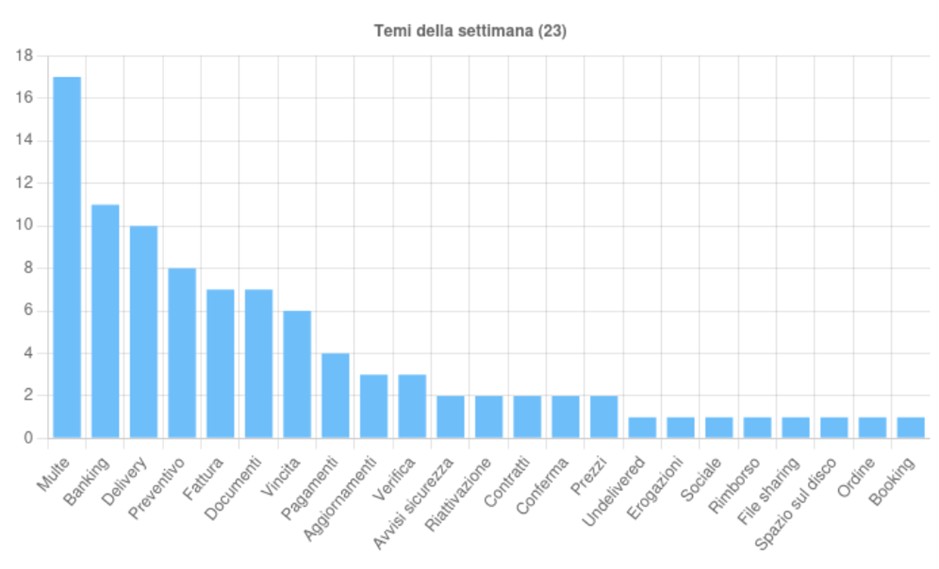
Individuati 23 temi, sfruttati per diffondere campagne malevole in Italia, nella settimana del 20-26 Settembre
L’attore della minaccia confeziona un’e-mail che appare come una comunicazione legittima e urgente, ad esempio una finta fattura, un documento di spedizione o un preventivo. Il corpo del messaggio è solitamente breve e spinge la vittima a scaricare un allegato o visualizzare un documento esterno tramite un link.
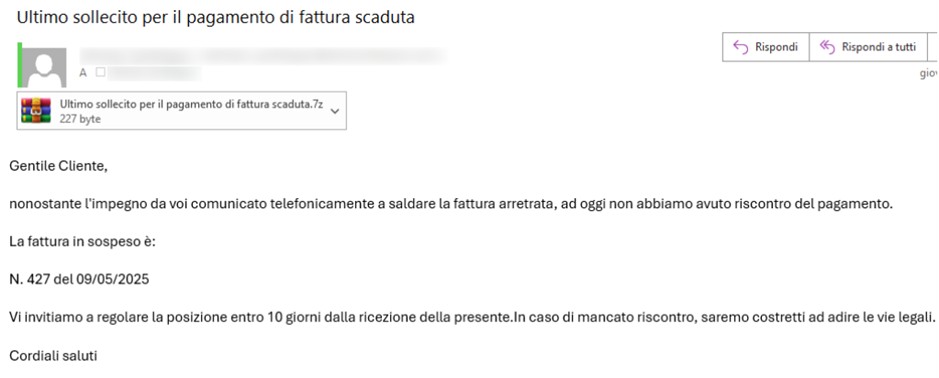
Le campagne individuate relative al malware Formbook, distribuiscono quest’ultimo mediante email con allegati compressi come ZIP,TAR,7z.
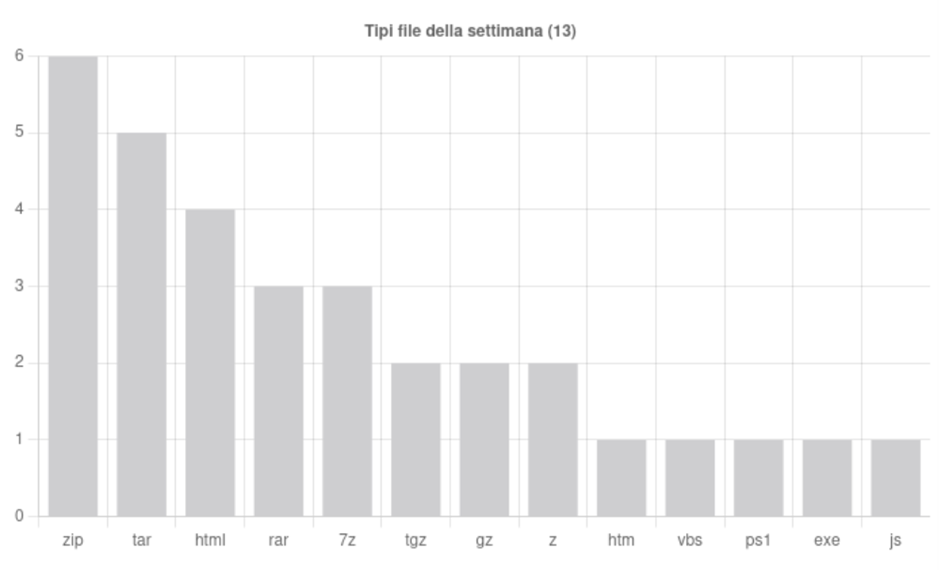
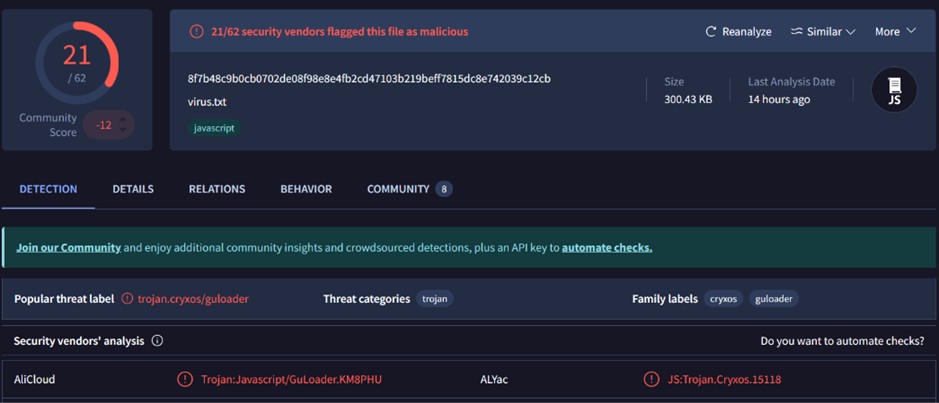
Una volta scaricato ed estratto l’archivio, ci troviamo davanti ad un file di testo con estensione .js. Analizzando l’hash del file tramite i principali motori di TI notiamo che esso risulta segnalato come Trojan.
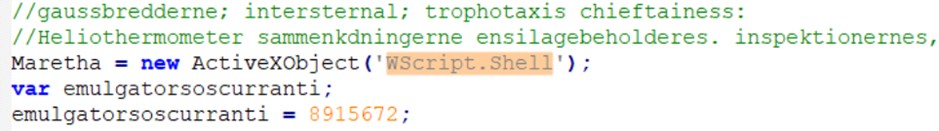
Il codice sorgente è fortemente offuscato: dopo un primo passaggio di formattazione la struttura sintattica risulta leggibile, ma le funzioni operative restano deliberatamente nascoste da nomi di variabili non significativi e dalla frammentazione del codice. L’analisi si è pertanto concentrata sull’identificazione di funzionalità che consentono l’interazione con il sistema operativo. La scoperta chiave è stata l’uso intensivo di ActiveXObject per istanziare oggetti COM di sistema:
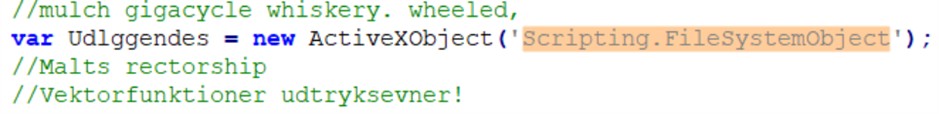
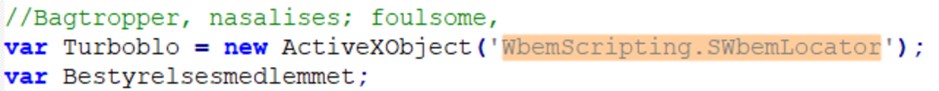
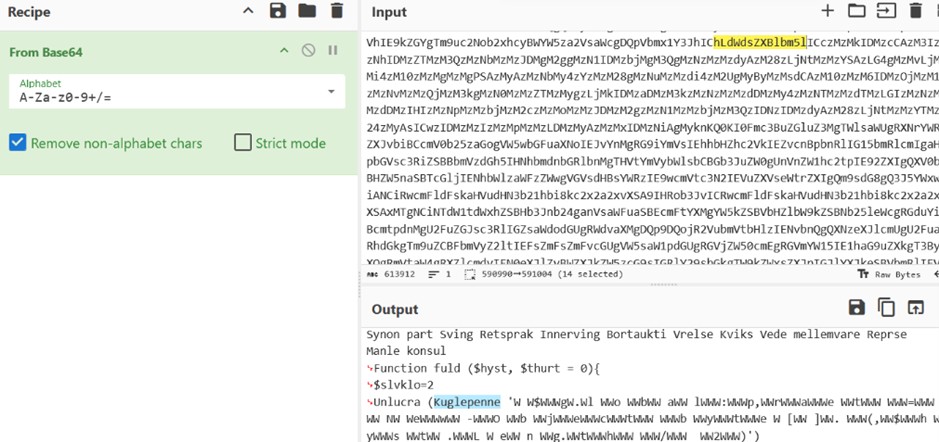
La logica principale dello script è un ciclo di assemblaggio: decodifica e concatena centinaia di piccole stringhe per costruire in memoria il payload della fase successiva, uno script PowerShell, che verrà salvato nella cartella %APPDATA% con il nome di “Plaidtry”.
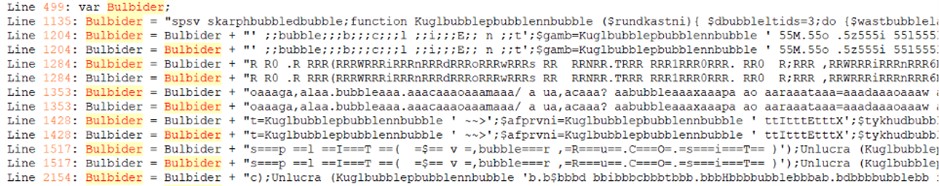

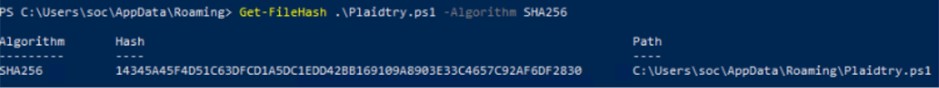
Lo script Plaidtry.ps1 è a sua volta offuscato, ma con una logica interna. Contiene una funzione (Kuglepenne) di de-offuscamento che ricostruisce i comandi reali campionando caratteri da stringhe offuscate. Eseguendo questa funzione in un ambiente sicuro (PowerShell ISE), abbiamo potuto decodificare i comandi passo dopo passo.
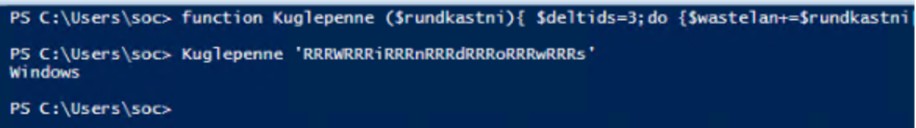
Esempio de-offuscamento
Il cuore dello script è la logica di download. Imposta uno User-Agent di Firefox per mascherare la richiesta, quindi utilizza il metodo Net.WebClient.DownloadFile per scaricare un payload dall’URL di Google Drive precedentemente decodificato. Il file viene salvato come %APPDATA%Pidg.chl
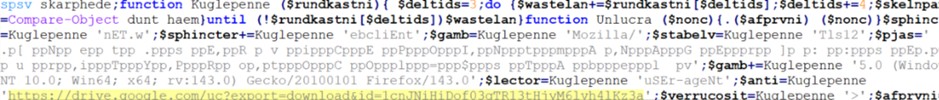
Script PS de-offuscato
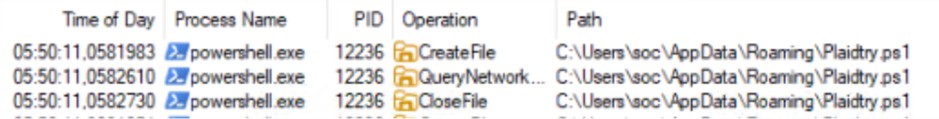
Dettaglio PROCMON
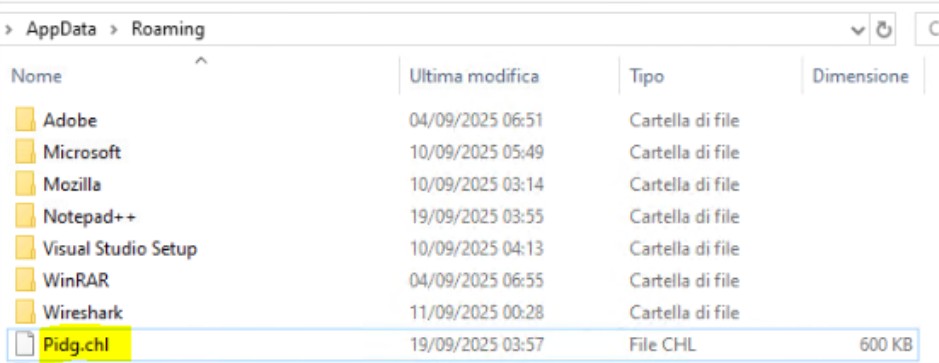
Dettaglio Folder
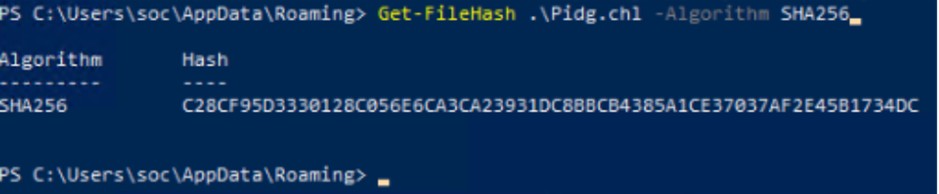
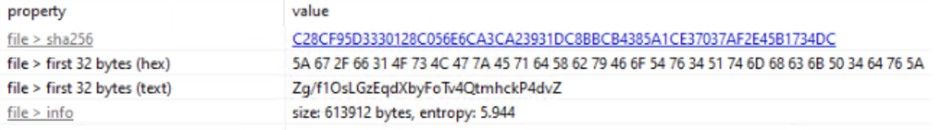
Il file Pidg.chl non è un eseguibile. È un file di testo contenente un’unica, lunga stringa codificata in Base64. Utilizzando PowerShell per decodificare questa stringa, abbiamo svelato l’ultimo e più pericoloso stadio dell’attacco: un iniettore di PE
Questo script, anch’esso altamente offuscato, è progettato per eseguire un file .exe senza mai scriverlo su disco. Le sue componenti chiave sono:
La logica dello script è la seguente: decodifica la grande stringa Base64 per ricostruire in memoria i byte dell’eseguibile di Formbook. Successivamente, alloca una nuova regione di memoria all’interno del processo powershell.exe in cui è in esecuzione, vi copia i byte di Formbook e infine avvia un nuovo thread in quel punto.
Il risultato è che Formbook inizia la sua esecuzione come un thread all’interno di un processo PowerShell legittimo. A questo punto, l’infostealer inizierebbe la sua attività malevola: registrare i tasti premuti, rubare le credenziali salvate nei browser, catturare i dati dai form web e inviarli a un’altra infrastruttura C2 controllata dall’attaccante.
Dopo aver ricostruito la catena di infezione e le tecniche utilizzate da Formbook, è possibile delineare le principali azioni di mitigazione e contenimento. Lo scopo è ridurre la superficie d’attacco, bloccare la diffusione e preservare le evidenze per la triage/IR.
Mitigazione
Eradicazione
Prevenzione
Comunicazione e disclosure
L’analisi di questo campione dimostra una chiara tendenza verso catene di infezione complesse e “fileless”. L’attore della minaccia ha investito notevoli sforzi per eludere il rilevamento a ogni livello: l’offuscamento degli script iniziali, l’uso di servizi cloud legittimi per l’hosting dei payload e, infine, l’iniezione in memoria del malware vero e proprio.
Questa metodologia stratificata rappresenta una sfida significativa per le soluzioni di sicurezza tradizionali basate su firme e analisi di file. Sottolinea la necessità di un monitoraggio comportamentale avanzato (XDR) e costante in grado di rilevare attività anomale da parte di processi altrimenti legittimi come PowerShell. L’analisi, infine, ci ha permesso di ricostruire l’intera catena di attacco e di estrarre IoC e TTPs preziosi per rafforzare le posture difensive contro minacce simili.
Le TTPs osservate durante l’analisi sono state mappate sul framework MITRE ATT&CK.
| Tattica | ID Tecnica | Nome Tecnica | Descrizione |
| Esecuzione | T1059.007 | JavaScript | L’infezione iniziale parte da uno script JavaScript. |
| Esecuzione | T1059.001 | PowerShell | PowerShell è usato come stadio intermedio per l’evasione e il download. |
| Evasione Difese | T1027 | Obfuscated Files or Information | Sia lo script JS che quello PS sono pesantemente offuscati per impedire l’analisi. |
| Evasione Difese | T1562.001 | Disable or Modify Tools | Lo script tenta di disabilitare servizi e controlla lo stato di Windows Defender. |
| Evasione Difese | T1055 | Process Injection | Il payload finale di FormBook viene iniettato in un processo legittimo in memoria. |
| Esecuzione | T1047 | Windows Management Instrumentation (WMI) | Il dropper JS utilizza WMI per tentare di eseguire lo script PowerShell in modo furtivo. |
| Comando e Controllo | T1105 | Ingress Tool Transfer | Il loader scarica il payload finale da una risorsa web esterna (Google Drive). |
| Comando e Controllo | T1573.002 | Encrypted Channel: Asymmetric Cryptography | Viene utilizzata una connessione HTTPS (TLS) per scaricare il payload, crittografando il traffico. |
8f7b48c9b0cb0702de08f98e8e4fb2cd47103b219beff7815dc8e742039c12cb
C28CF95D3330128C056E6CA3CA23931DC8BBCB4385A1CE37037AF2E45B1734DC
14345A45F4D51C63DFCDD1A5DC1EDD42BB169109A8903E33C4657C92AF6DF2830
https://drive.google.com/uc?export=download&id=1cnJNHiDoF03QTRl3tHyM6lvh4lKo3a
Fonti:ACN.GOV.IT ,CERT-AGID
Il supporto di ELMI nelle strategie di prevenzione e detection
ELMI propone un percorso integrato di prevenzione, rilevazione e risposta alle minaccestudiato specificamente per contrastare campagne di infostealer basate su phishing e fileless execution. La proposta combina soluzioni integrate, affiancando alla tecnologia un approccio consulenziale e formativo.
Le misure tecniche rappresentano il primo baluardo nella protezione contro infostealer, richiedendo un’architettura di sicurezza multilivello che integra strumenti e processi dedicati. All’interno del suoSecurity Competence Center, ELMI mette a disposizione un set di soluzioni integrate che coprono l’intero ciclo di difesa.
Il Security Competence Center integra, inoltre, servizi di Network Operation Center(NOC), dedicati alla gestione e al monitoraggio continuo della rete, e Managed Services, che consentono la gestione remota dell’infrastruttura IT, permettendo di configurare e controllare a distanza tutti i componenti aziendali.
I punti di forza del Security Competence Center di ELMI risiedono nell’approccio integrato agli incidenti informatici, nella disponibilità operativa H24 su tutto il territorio e nella capacità di offrire servizi personalizzati a 360°, garantendo così una protezione coerente e completa.
L’obiettivo non è solo quello di fornire singoli strumenti, ma costruire insieme al cliente una difesa coordinata, capace di anticipare le minacce, accelerare il rilevamento e garantire una risposta immediata.
A garantire l’efficacia dell’intero processo è la competenza di un team multidisciplinare, composto da figure specializzate come network engineer, system administrator e security analyst, con un solido background operativo e una visione end-to-end dell’infrastruttura IT.
Affrontare efficacemente il rischio cyber richiede un approccio strutturato, personalizzato e progressivo.Il supporto di ELMI si articola in tre momenti chiave:
Grazie a un approccio consulenziale e operativo integrato, ELMI accompagna i clienti lungo tutto il percorso di rafforzamento della postura di sicurezza, assicurando una progressiva riduzione del rischio e una maggiore resilienza rispetto a minacce complesse e in continua evoluzione.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…