
Gli aggressori utilizzano una tecnica di phishing avanzata, nota come CoPhish, che si avvale di Microsoft Copilot Studio per convincere gli utenti a concedere l’accesso non autorizzato ai propri account Microsoft Entra ID.
Un recente rapporto, descrive l’attacco nei dettagli e sottolinea come malgrado gli sforzi di Microsoft volti a rafforzare le politiche di consenso, permangano evidenti vulnerabilità negli strumenti di intelligenza artificiale offerti in cloud.
L’adozione crescente di strumenti come Copilot da parte delle organizzazioni evidenzia la necessità di un’attenta supervisione delle piattaforme low-code. In questo ambito, funzionalità configurabili dall’utente, progettate per favorire la produttività, possono inavvertitamente agevolare il phishing.
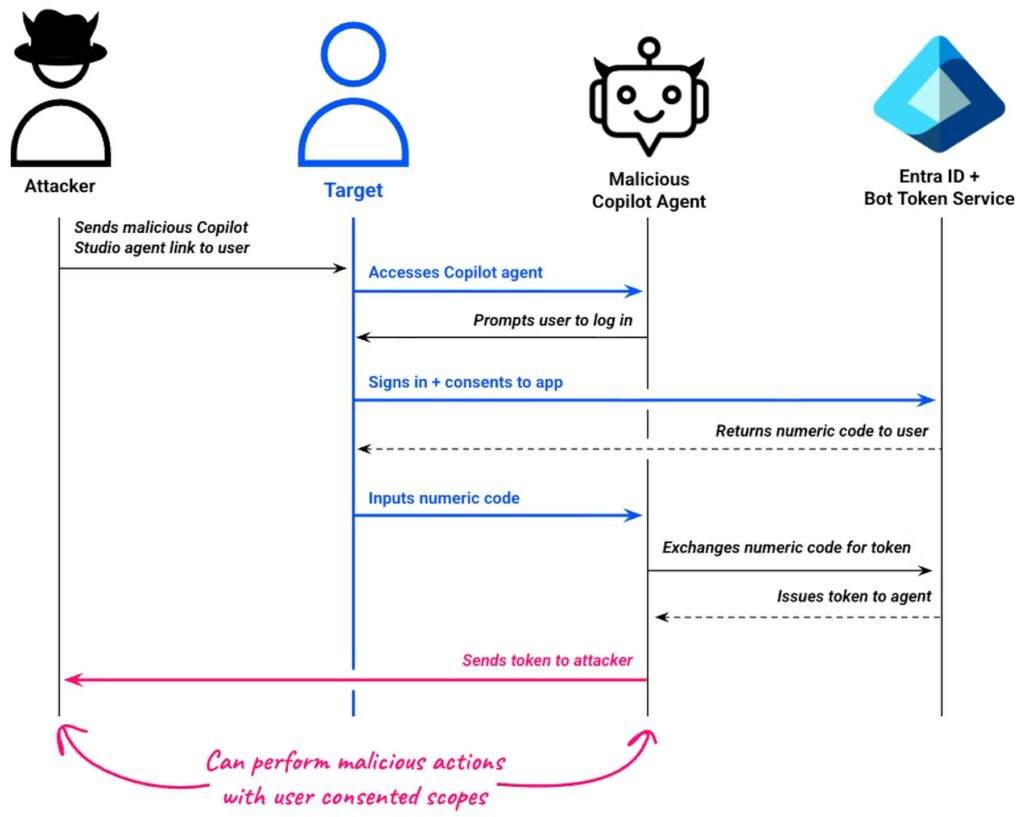
Questo attacco scoperto dai ricercatori di Datadog Security Labs, utilizza agenti di intelligenza artificiale personalizzabili ospitati su domini Microsoft legittimi per mascherare i tradizionali attacchi di consenso OAuth, facendoli apparire affidabili e aggirando i sospetti degli utenti.
Gli aggressori sono in grado di progettare e creare chatbot dall’aspetto innocuo, al fine di ottenere dagli utenti le credenziali di accesso e, successivamente, tokens OAuth utilizzabili per compiere azioni dannose, ad esempio, l’accesso ai calendari o la lettura delle email.
Gli attacchi di consenso OAuth, classificati nella tecnica MITRE ATT&CK T1528, consistono nell’indurre gli utenti ad approvare registrazioni di app dannose che richiedono ampie autorizzazioni per l’accesso a dati sensibili.
Gli attacchi condotti all’interno degli ambienti Entra ID prevedono la creazione di registri di applicazioni da parte degli aggressori al fine di ottenere l’accesso alle risorse messe a disposizione da Microsoft Graph, quali ad esempio la posta elettronica o OneNote. Ciò avviene mediante l’utilizzo di collegamenti di phishing che inducono le vittime a concedere il consenso. Una volta ottenuto l’approvazione, il token che ne deriva conferisce all’aggressore la possibilità di impersonificare l’utente, consentendo così l’estrazione dei dati o ulteriori azioni di compromissione.
Negli anni, Microsoft ha implementato misure di difesa più solide, come ad esempio le limitazioni relative alle applicazioni non verificate. Inoltre, un aggiornamento del luglio 2025 ha stabilito come impostazione predefinita “microsoft-user-default-recommended”, andando così a bloccare automaticamente l’accesso a autorizzazioni considerate ad alto rischio, quali Sites.Read.All e Files.Read.All, qualora non venga concessa l’approvazione da parte dell’amministratore.
Tuttavia, permangono delle lacune: gli utenti senza privilegi possono comunque approvare app interne per autorizzazioni come Mail.ReadWrite o Calendars.ReadWrite, mentre gli amministratori con ruoli come Amministratore applicazioni possono acconsentire a qualsiasi autorizzazione su qualsiasi app.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…