
La criminalità informatica continua a reinventarsi e LockBit ne è uno degli esempi più evidenti. Attivo dalla fine del 2019, il gruppo è diventato uno degli operatori ransomware più prolifici mai osservati. Secondo una recente analisi di AhnLab, la gang non solo non mostra segni di rallentamento, ma ha introdotto una nuova variante, LockBit 5.0, con cui colpisce un’ampia gamma di organizzazioni, dai grandi operatori IT fino a realtà più piccole come le chiese locali.
Nonostante le operazioni di contrasto condotte dalle forze dell’ordine a livello internazionale, LockBit continua a rimanere operativo grazie a una struttura flessibile e alla capacità di adattare rapidamente strumenti e strategie. Il gruppo adotta infatti il modello Ransomware-as-a-Service (RaaS), una sorta di franchising criminale: gli sviluppatori principali realizzano il malware, mentre una rete di affiliati si occupa delle intrusioni e degli attacchi sul campo.
I numeri riportati da AhnLab confermano l’impatto del gruppo. Tra agosto 2021 e agosto 2022, LockBit è stato responsabile del 30,25% degli attacchi ransomware noti. Nel corso del 2023, la sua quota si è attestata intorno al 21%, una percentuale comunque significativa nel panorama globale delle minacce.
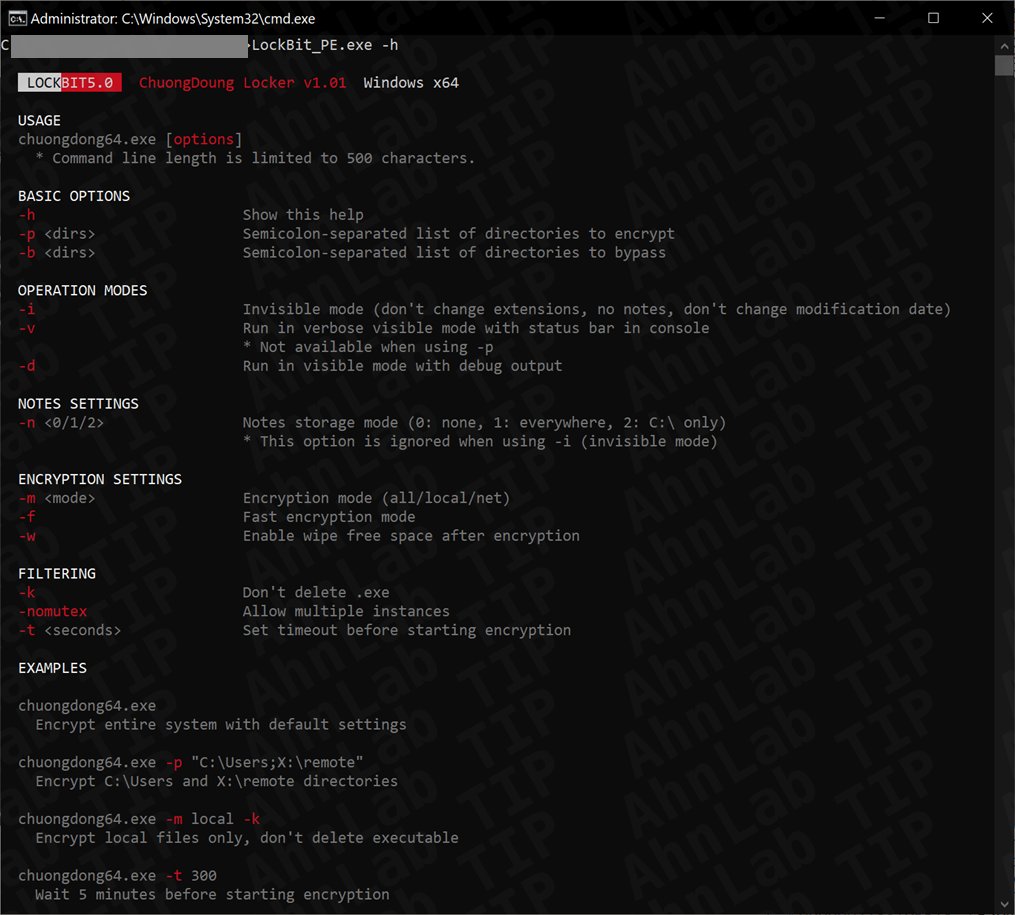
Le operazioni seguono uno schema consolidato in tre fasi. La prima consiste nell’ottenimento dell’accesso iniziale, attraverso lo sfruttamento di vulnerabilità, attacchi di forza bruta o campagne di phishing. Segue il movimento laterale, durante il quale gli attaccanti aumentano i privilegi per assumere il controllo dell’intera rete. L’ultima fase è quella più distruttiva: la distribuzione del ransomware, con la cifratura dei file e l’esfiltrazione dei dati tramite strumenti dedicati come Stealbit.
LockBit 5.0 rappresenta un ulteriore passo avanti sul piano tecnico, soprattutto in termini di automazione e rapidità. Il malware è progettato per essere estremamente flessibile: può ricevere diversi parametri al momento dell’esecuzione, ma è in grado di funzionare anche senza configurazioni specifiche. Questa caratteristica consente anche agli affiliati meno esperti di portare a termine l’attacco con successo.
Come parte della strategia di pressione sulle vittime, il gruppo gestisce un sito dedicato alla pubblicazione dei dati sottratti, utilizzato per esporre pubblicamente chi rifiuta di pagare il riscatto. Al momento, il rapporto di AhnLab indica che nessuna azienda sudcoreana compare in questo elenco, ma la diffusione delle vittime resta globale. I settori colpiti includono IT, elettronica, studi legali e organizzazioni religiose.
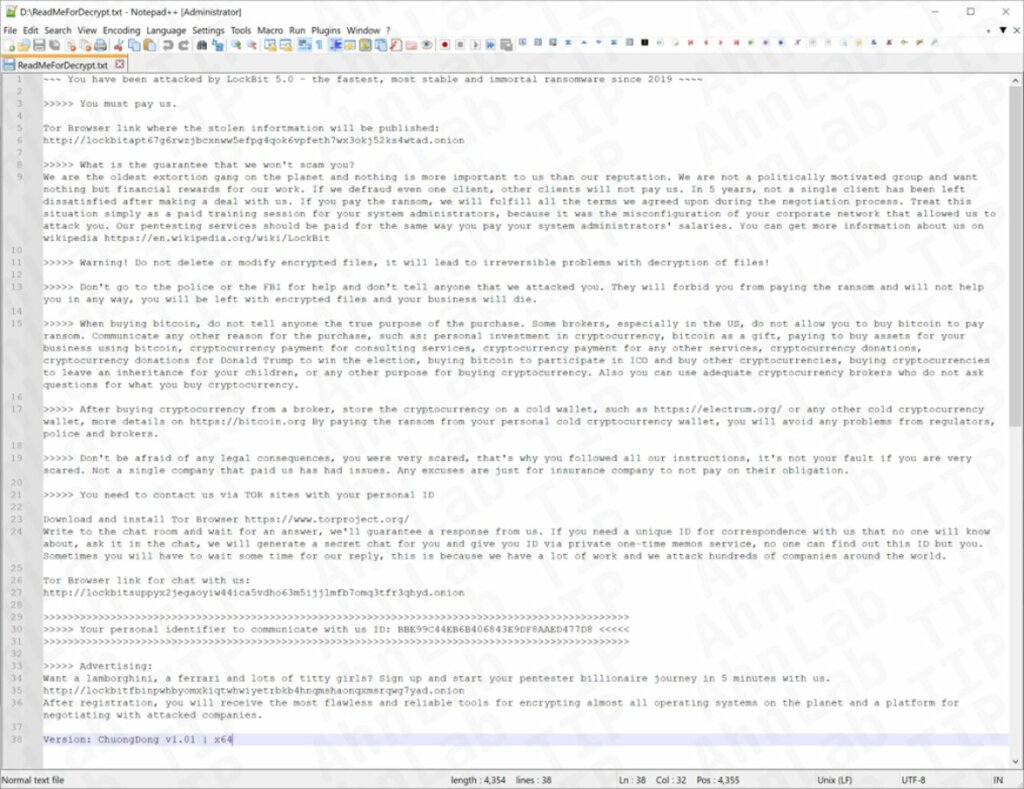
Un elemento particolarmente rilevante di LockBit 5.0 riguarda l’approccio comunicativo nelle richieste di riscatto. Il gruppo cerca di presentarsi non come una semplice banda criminale, ma come un presunto fornitore di servizi. Nei messaggi agli obiettivi compromessi vengono citati “Premium Criminal Branding Services” e vengono promesse, in cambio del pagamento, misure come il ritardo nella divulgazione dei dati o persino la correzione gratuita delle vulnerabilità sfruttate.
All’interno delle note compare anche un insolito “Manifesto Strategico”, in cui gli autori dichiarano l’intenzione di puntare ai profitti senza attirare eccessiva attenzione, affermando di voler essere “avidi come REvil, non rumorosi come LockBit”. Una posizione che appare in contrasto con l’elevata notorietà già raggiunta dal gruppo.
L’impatto economico di queste attività resta enorme. Secondo il rapporto, le richieste di riscatto e i costi di ripristino associati agli attacchi LockBit hanno causato perdite complessive pari a miliardi di dollari. Gli esperti di sicurezza sottolineano che l’evoluzione rappresentata da LockBit 5.0 dimostra la resilienza del gruppo, che continua a rappresentare una minaccia concreta per organizzazioni di ogni dimensione.
La raccomandazione degli analisti è chiara: le aziende devono andare oltre le difese di base e prepararsi alle tecniche specifiche adottate da LockBit 5.0, in particolare alla rapida esfiltrazione dei dati che precede la cifratura dei sistemi.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…