
Una campagna sempre più aggressiva, che punta direttamente alle infrastrutture di accesso remoto, ha spinto gli autori delle minacce a tentare di sfruttare attivamente le vulnerabilità dei portali VPN GlobalProtect di Palo Alto Networks.
Il 5 dicembre Palo Alto Networks ha emesso un avviso urgente, esortando i clienti ad adottare l’autenticazione a più fattori (MFA), a limitare l’esposizione del portale tramite firewall e ad applicare le patch più recenti.
In base alle risultanze del report sulle attività di monitoraggio condotto da GrayNoise, che ha rilevato scansioni e sforzi di sfruttamento condotti da oltre 7.000 indirizzi IP unici a livello globale, le organizzazioni che utilizzano la popolare soluzione VPN per garantire la sicurezza del lavoro remoto sono state messe in allarme.
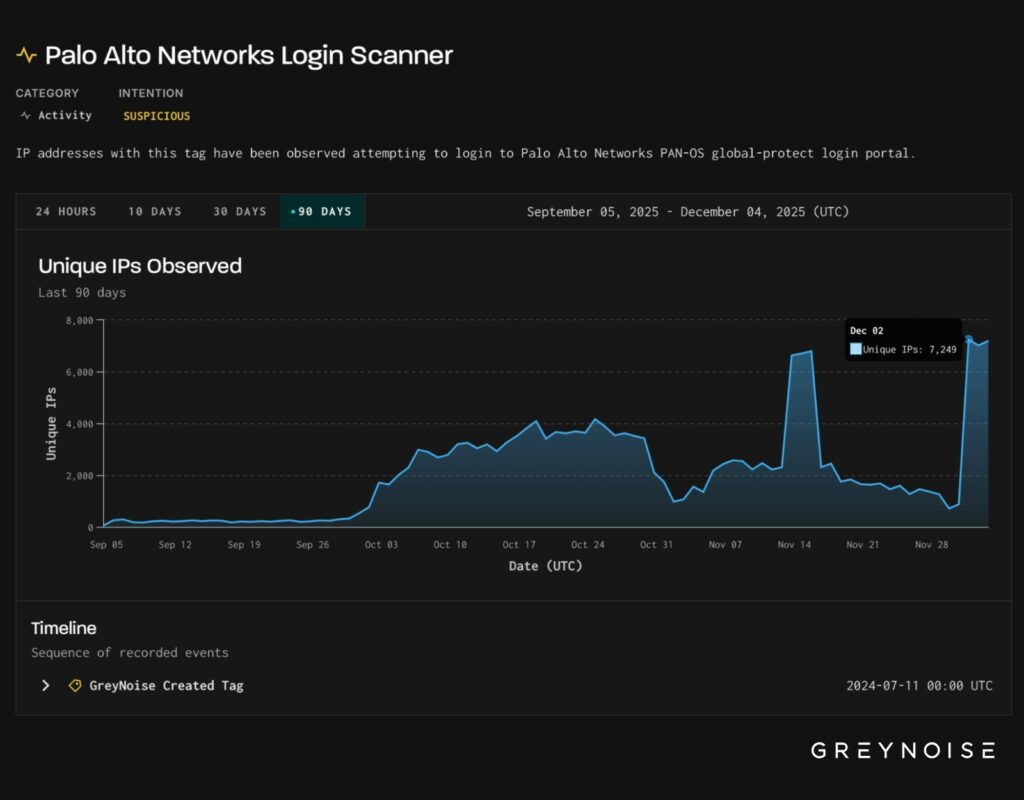
Targeting osservato da Ip (Fonte: GreyNoise)
A partire dalla fine di novembre 2025, sono stati rilevati attacchi che sfruttano le vulnerabilità dei gateway GlobalProtect, soprattutto quelle accessibili pubblicamente attraverso la porta UDP 4501.
GlobalProtect di Palo Alto Networks è da tempo un obiettivo primario a causa della sua onnipresenza negli ambienti aziendali. Difetti storici, come CVE-2024-3400 (una vulnerabilità critica di command injection, risolta nell’aprile 2024 con punteggio CVSS 9,8), continuano a perseguitare i sistemi non ancora patchati.
Le ondate recenti sfruttano configurazioni errate che consentono l’accesso pre-autenticazione, incluse credenziali predefinite o portali di amministrazione esposti. Gli aggressori utilizzano strumenti come script personalizzati che imitano i moduli Metasploit per enumerare i portali, effettuare accessi con forza bruta e rilasciare malware per la persistenza.
Secondo i dati di Shadowserver e di altri feed di intelligence sulle minacce, le fonti IP comprendono proxy residenziali, provider di hosting Bulletproof e istanze VPS compromesse in Asia, Europa e Nord America.
Gli indicatori di compromissione includono picchi anomali di traffico UDP sulla porta 4501, seguiti da richieste HTTP agli endpoint /global-protect/login.urd. Nelle violazioni confermate, gli intrusi hanno esfiltrato token di sessione, consentendo il movimento laterale nelle reti aziendali.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…