
Una falla critica di 13 anni, nota come RediShell, presente in Redis, permette l’esecuzione di codice remoto (RCE) e offre agli aggressori la possibilità di acquisire il pieno controllo del sistema host sottostante.
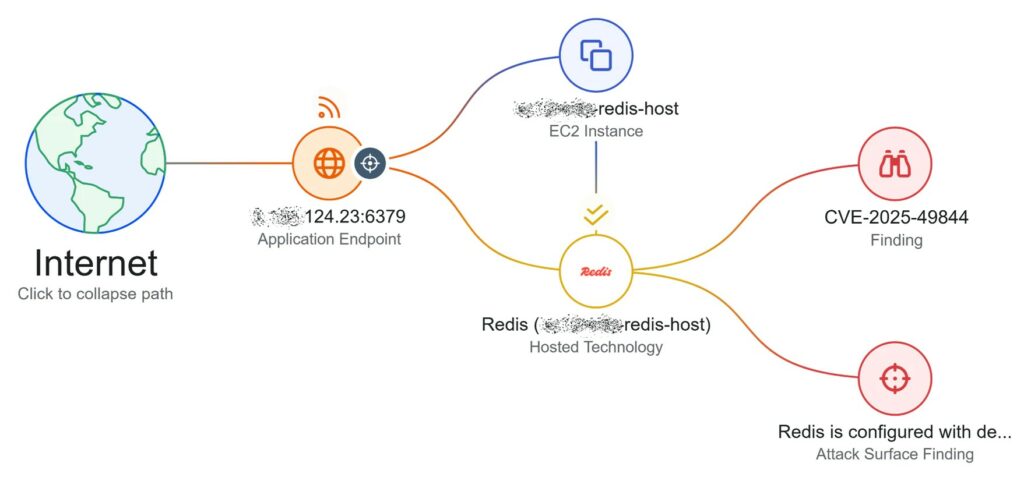
Il problema di sicurezza, è stato contrassegnato come CVE-2025-49844 ed è stato rilevato da Wiz Research. A questo problema è stato assegnato il massimo livello di gravità secondo la scala CVSS, con un punteggio di 10,0, una valutazione che indica le vulnerabilità di sicurezza più critiche.
l’analisi condotta da Wiz Research ha rivelato un’ampia superficie di attacco, con circa 330.000 istanze Redis esposte a Internet. È allarmante notare che circa 60.000 di queste istanze non hanno alcuna autenticazione configurata.
La falla di sicurezza, viene causata da un errore di tipo Use-After-Free (UAF) nella gestione della memoria, è presente nel codice di Redis da circa tredici anni. Questa vulnerabilità può essere sfruttata da un utente malintenzionato, dopo aver completato l’autenticazione, attraverso l’invio di uno script Lua appositamente realizzato.
Poiché lo scripting Lua è una funzionalità predefinita, l’aggressore può uscire dall’ambiente sandbox Lua per ottenere l’esecuzione di codice arbitrario sull’host Redis.
Il controllo completo viene garantito all’aggressore a questo livello di accesso, permettendogli di dirottare le risorse di sistema per attività come il mining di criptovalute, di muoversi lateralmente sulla rete, nonché di rubare, eliminare o crittografare i dati.
Il potenziale impatto è amplificato dall’ubiquità di Redis. Si stima che il 75% degli ambienti cloud utilizzi l’archivio dati in-memory per la memorizzazione nella cache, la gestione delle sessioni e la messaggistica.
Il flusso di attacco inizia con l’invio da parte dell’aggressore di uno script Lua dannoso all’istanza vulnerabile di Redis. Dopo aver sfruttato con successo il bug UAF per uscire dalla sandbox, l’aggressore può stabilire una reverse shell per l’accesso persistente. Da lì, possono compromettere l’intero host rubando credenziali come chiavi SSH e token IAM, installando malware ed esfiltrando dati sensibili sia da Redis che dalla macchina host.
Il 3 ottobre 2025, Redis ha rilasciato un avviso di sicurezza e versioni patchate per risolvere il problema CVE-2025-49844. Si consiglia vivamente a tutti gli utenti Redis di aggiornare immediatamente le proprie istanze, dando priorità a quelle esposte a Internet o prive di autenticazione.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…