
Un’insidiosa offensiva di malware, nota come “Sindoor Dropper”, si concentra sui sistemi operativi Linux, sfruttando metodi di spear-phishing raffinati e un complesso processo d’infezione articolato in diverse fasi. L’operazione subdola prende di mira gli utenti con esche legate al recente scontro tra Pakistan e India, conosciuto con il nome di Operazione Sindoor, al fine di convincerli ad attivare file nocivi.
La campagna Sindoor Dropper evidenzia un’evoluzione nelle tecniche di attacco degli autori delle minacce, dimostrando una chiara attenzione agli ambienti Linux, meno presi di mira dalle campagne di phishing.
L’attacco inizia quando un utente apre un .desktopfile dannoso, denominato “Note_Warfare_Ops_Sindoor.pdf.desktop”, che si spaccia per un normale documento PDF . Secondo l’analisi del sistema Nextron, una volta eseguito, apre un PDF escamotage benigno per mantenere l’illusione di legittimità, mentre avvia silenziosamente in background un processo di infezione complesso e fortemente offuscato.
Il .desktopfile, riporta Nextron, scarica diversi componenti, tra cui un decryptor AES ( mayuw) e un downloader crittografato ( shjdfhd). Un tratto peculiare di questa attività è l’utilizzo di file desktop trasformati in strumenti offensivi, tecnica in precedenza attribuita al gruppo APT36, altresì noto come Transparent Tribe o Mythic Leopard, specializzato nelle minacce avanzate e persistenti.
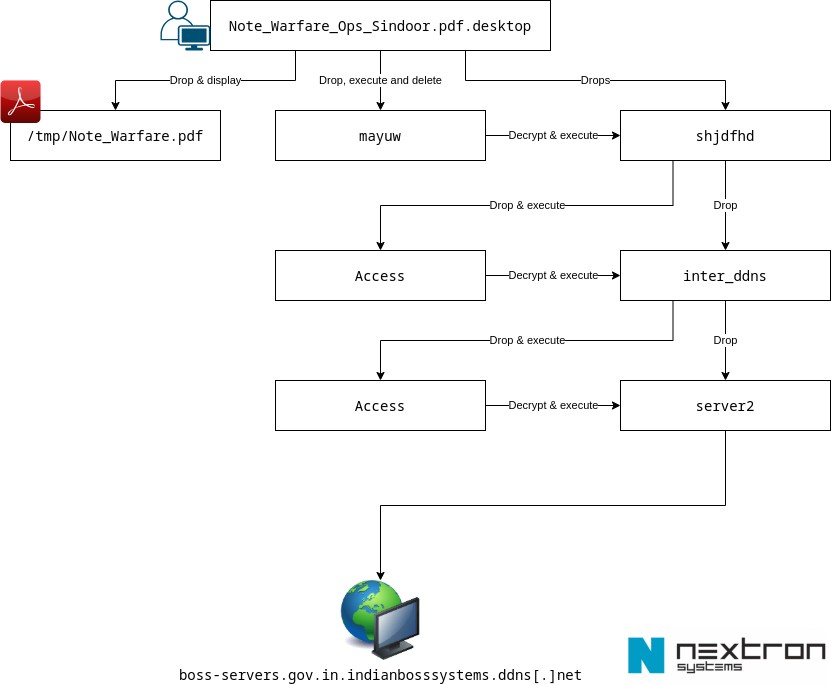
Il processo in questione è stato ideato per sfuggire sia all’analisi statica sia a quella dinamica. Al momento della sua individuazione, il payload iniziale non aveva lasciato traccia su VirusTotal, risultando quindi non rilevato. Il decryptor, un binario Go compresso con UPX, viene intenzionalmente corrotto rimuovendo i suoi magic byte ELF, probabilmente per bypassare le scansioni di sicurezza su piattaforme come Google Docs. Il .desktopfile ripristina questi byte sul computer della vittima per rendere nuovamente eseguibile il binario.
Questo avvia un processo in più fasi in cui ogni componente decifra ed esegue il successivo. La catena include controlli anti-macchina virtuale di base, come la verifica dei nomi delle schede e dei fornitori, l’inserimento nella blacklist di specifici prefissi di indirizzi MAC e il controllo del tempo di attività della macchina.
Il payload finale è una versione riadattata di MeshAgent, uno strumento di amministrazione remota open source legittimo. Una volta implementato, MeshAgent si connette a un server di comando e controllo (C2) ospitato su un’istanza EC2 di Amazon Web Services (AWS) all’indirizzo wss://boss-servers.gov.in.indianbosssystems.ddns[.]net:443/agent.ashx.
Ciò fornisce all’aggressore l’accesso remoto completo al sistema compromesso, consentendogli di monitorare l’attività dell’utente, spostarsi lateralmente sulla rete ed esfiltrare dati sensibili, ha affermato Nextron.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…