
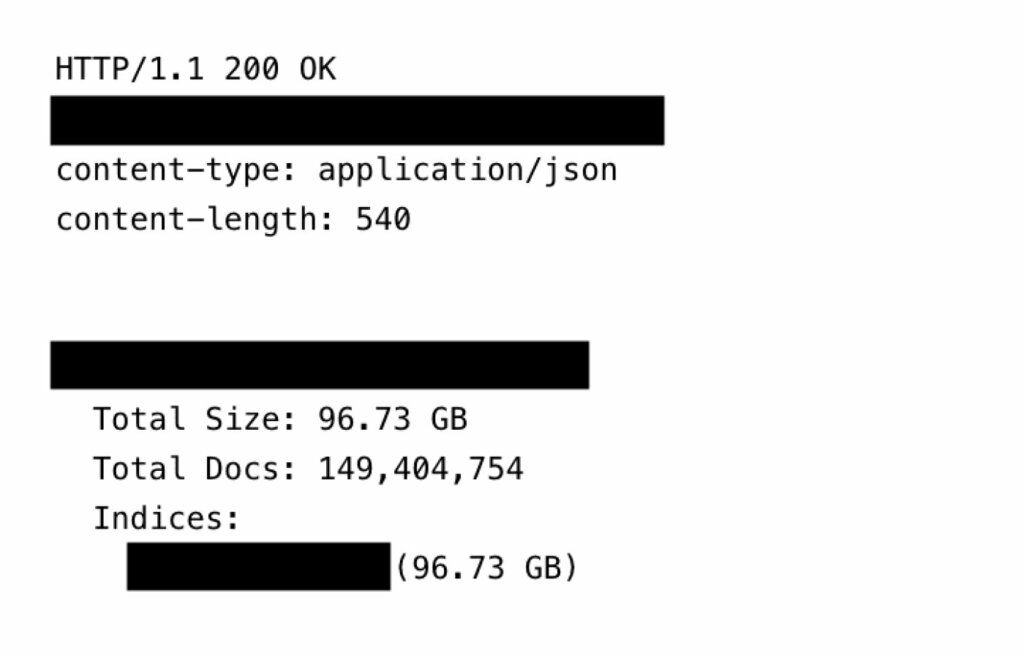
Un recente leak ha rivelato 149 milioni di login e password esposti online, tra cui account di servizi finanziari, social, gaming e siti di incontri. La scoperta è stata fatta dal ricercatore Jeremiah Fowler e condivisa con ExpressVPN. La mole di dati era impressionante: oltre 96 GB di informazioni non protette né criptate, facilmente accessibili a chiunque.
Il database conteneva email, username, password e link diretti ai login. Non si tratta di un caso isolato: i malware “infostealer” continuano a raccogliere credenziali da tutto il mondo. La vicenda dimostra che anche i cybercriminali possono diventare vittime di leak, soprattutto quando i dati vengono conservati in repository cloud pubblici.
Gli account colpiti erano estremamente variegati. Dai social network come Facebook, Instagram, TikTok e X, ai siti di incontri e piattaforme come OnlyFans, fino agli account di streaming come Netflix, DisneyPlus e Roblox.
Non mancano account finanziari, portafogli crypto, conti bancari e carte di credito. Perfino credenziali legate a domini governativi sono state esposte, aprendo scenari di rischio per la sicurezza nazionale e la privacy individuale.

L’esposizione dei dati ha permesso potenzialmente attacchi di “credential stuffing”, dove malintenzionati automatizzano l’accesso agli account rubati. Questo aumenta le probabilità di frodi, furti d’identità, crimini finanziari e campagne di phishing estremamente realistiche.
L’accesso alle caselle di posta elettronica avviene normalmente attraverso un utente e una password. Tale utente e password sappiamo che deve essere conservata con cura e messa al riparo da occhi indiscreti sia quando è presente la MFA che soprattutto quando questa non è attiva o impossibile da utilizzare.
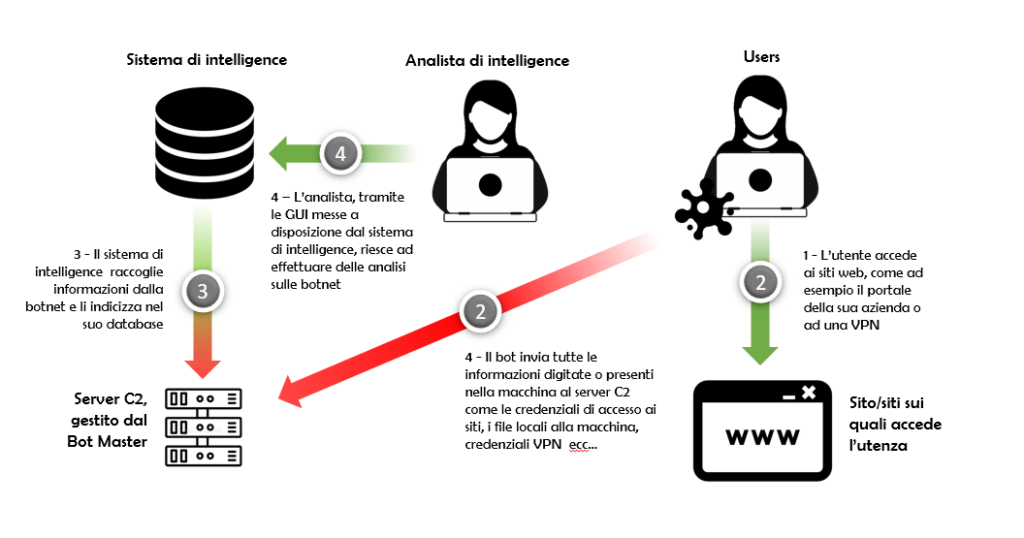
Queste coppie di chiavi, nome utente e password, devono essere messe al riparo anche dagli infostealer. Un Infostealer – o ladro di informazioni – è un tipo di malware che viene installato su una postazione di lavoro e ruba tutte le informazioni che un utente digita con la tastiera e le invia ad un server remoto controllato da un attaccante.
Accessi alla banca, accessi alle caselle di posta, accessi a qualsiasi account o profilo utente come Netflix, Disney Plus, Instagram, Facebook, vengono inviati costantemente al “botmaster”. Il botmaster è un malintenzionato che controlla la botnet dei computer infetti e vende queste informazioni nei forum underground, alle volte creando delle API di interfacciamento verso diversi mercati e alle volte – per le botnet più grandi – anche verso i tool di cyber threat intelligence (CTI) chiamati “dark feed”.
Prendersi un infostealer è molto semplice, ad esempio scaricando un file infetto – come i keygen di attivazione dei software – oppure un software non originale, oppure cliccando su un allegato infetto.
Come Red Hot Cyber abbiamo spesso portato all’attenzione il fenomeno delle botnet e dei dati raccolti da questi malware dai singoli dispositivi. Tali informazioni, vengono rivendute successivamente nei mercati underground, e sono spesso l’inizio di un attacco ai sistemi informatici in quanto forniscono credenziali di accesso o preziose informazioni per i criminali informatici.
Il database utilizzava malware per keylogging e infostealer, catturando informazioni aggiuntive come il percorso host invertito, utile per indicizzare le vittime. Ogni record era unico e organizzato in modo da evitare duplicazioni. L’accesso ai dati era semplice: bastava un browser per visualizzare l’intero contenuto.
Proteggersi è complesso ma possibile. L’uso di antivirus aggiornati è essenziale, così come la revisione di app, permessi e processi in esecuzione su dispositivi. Password manager crittografati possono ridurre alcuni rischi, pur non essendo una soluzione totale contro malware avanzati. Aggiornamenti regolari di sistema operativo e software di sicurezza rimangono fondamentali.
Le aziende e gli individui devono essere consapevoli che malware, allegati malevoli, aggiornamenti falsi e estensioni del browser compromesse possono rapidamente compromettere le credenziali. La prevenzione passa anche dall’educazione digitale e dalla vigilanza costante sulle proprie informazioni online.
La scoperta di Jeremiah Fowler e la successiva segnalazione al provider hanno portato alla sospensione dell’hosting del database dopo diverse settimane. Tuttavia, il danno potenziale rimane elevato, considerando che milioni di credenziali sono rimaste accessibili per un periodo prolungato.
L’incidente sottolinea quanto sia fragile la sicurezza dei dati e quanto sia essenziale monitorare e proteggere costantemente le proprie informazioni digitali. La gestione delle password e la sicurezza informatica non sono più opzionali, ma necessità quotidiana.
Le cifre mostrano che tra gli account più colpiti ci sono Gmail con 48 milioni di login, Facebook 17 milioni, Instagram 6,5 milioni e Netflix 3,4 milioni. Questi numeri dimostrano quanto siano vulnerabili persino i servizi più popolari e diffusi.
Per ridurre l’esposizione, è consigliabile adottare autenticazione a due fattori, verificare periodicamente le attività sospette e utilizzare strumenti affidabili per la gestione delle credenziali. La sicurezza digitale dipende tanto dalle abitudini degli utenti quanto dalla robustezza dei servizi.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…