
Il tema dell’hacking e del furto di auto tramite Flipper Zero è tornato alla ribalta in tutto il mondo e anche noi ne abbiamo parlato con un recente articolo. Questa volta, gli hacker hanno affermato di vendere un “firmware segreto” per il gadget, che potrebbe essere utilizzato contro Ford, Audi, Volkswagen, Subaru, Hyundai, Kia e molti altri marchi.
Dal nbostro articolo venivano pubblicate informazioni relative alle prove presentate sul canale YouTube “Talking Sasquach” che aveva messo mano sul famigerato firmware presente nelle underground. Sembrerebbe che tale mod per flipper zero sia stata sviluppato da un hacker di nome Daniel, che presumibilmente vive in Russia, e dal suo socio Derrow, che ha sviluppato e vende sul darknet il firmware denominato Unleashed per Flipper Zero.
Daniel ha affermato di aver acquistato da altre persone vari frammenti di codice sorgente necessari per creare il firmware. Ha aggiunto che il firmware potrebbe effettivamente essere utilizzato per i furti d’auto, ma è anche molto diffuso tra le officine meccaniche.
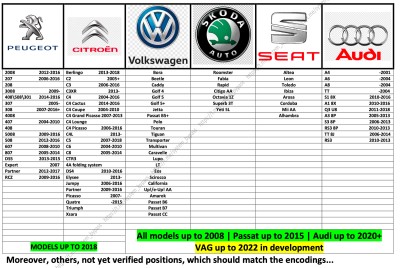
Gli hacker sostengono che il dispositivo modificato possa intercettare i segnali provenienti dai telecomandi e calcolare il codice successivo per sbloccare l’auto, creando una “copia ombra della chiave originale”. Secondo la documentazione fornita, tali attacchi funzionano contro quasi 200 modelli di auto, tra cui le versioni 2025 di Ford, Audi, Volkswagen, Subaru, Hyundai, Kia, Fiat, Mitsubishi, Suzuki, Peugeot, Citroën e Skoda.
Sono disponibili due versioni del firmware: quella base a 600 dollari (solo la versione attuale) e quella estesa a 1000 dollari (con aggiornamenti e supporto futuri); il pagamento è accettato in criptovaluta.
Allo stesso tempo, il firmware è presumibilmente associato a un dispositivo specifico tramite un numero di serie per impedirne la distribuzione non autorizzata. Per farlo, gli acquirenti sono tenuti a fornire foto della confezione del Flipper Zero, che mostrano il numero di serie del dispositivo, e una foto di una parte specifica delle impostazioni del gadget.
Daniel ha dichiarato ai giornalisti di aver venduto la tecnologia a circa 150 clienti in due anni, mentre Darrow afferma che “le vendite sono alle stelle”.
Ovviamente la community dell’automotive e della cybersecurity ha espresso preoccupazione per il fatto che, se questa tecnologia possa diffondersi, e quindi portare a un’impennata dei furti d’auto. La pubblicazione scrive che nel 2026, “i Kia Boys potrebbero diventare Flipper Boys”, riferendosi alla nota tendenza dei giovani a rubare auto Kia e Hyundai.
In risposta a numerosi resoconti dei media, uno degli autori di Flipper Zero, Pavel Zhovner, ha pubblicato un lungo messaggio sul blog ufficiale.
“Alcuni negozi darknet hanno iniziato a vendere il cosiddetto firmware ‘privato’ per Flipper Zero, sostenendo che possa essere utilizzato per hackerare innumerevoli auto.In realtà, tutti questi metodi sono stati pubblicati più di 10 anni fa. Niente di nuovo. Gli autori di tali firmware si limitano a rielaborare vulnerabilità note, spacciandole per “nuovi hack”. E, cosa importante, queste vulnerabilità non hanno nulla a che fare con i veri furti d’auto, poiché impediscono l’avviamento del motore”, scrive Zhovner.
Lo sviluppatore spiega che KeeLoq è stato sviluppato negli anni ’80 e utilizzato principalmente nei sistemi di accesso più datati (come le porte dei garage e i primi allarmi per auto). Si tratta di un sistema a codice variabile (o a salto), in cui ogni trasmissione utilizza un nuovo segnale univoco crittografato con una chiave del produttore a 64 bit.
Secondo Zhovner, il punto debole di KeeLoq è la chiave del produttore. Il problema è che le case automobilistiche spesso utilizzavano la stessa chiave per l’intera gamma di modelli. Se questa chiave venisse divulgata, gli aggressori sarebbero in grado di intercettare i segnali di qualsiasi telecomando di questa marca.
“Gli autori del firmware ‘hacker’ si limitano a distribuire vecchie chiavi rubate a diverse case automobilistiche. Non è una novità, vulnerabilità di questo tipo sono state descritte in dettaglio già nel 2006”, spiega il creatore di Flipper. “Da allora, le case automobilistiche sono passate a protocolli radio più moderni con autenticazione bidirezionale, in cui l’auto e la chiave si scambiano messaggi per verificarne l’autenticità.”
Zhovner ribadisce poi i punti che gli autori di Flipper Zero avevano spiegato in dettaglio nel 2024, quando il governo canadese annunciò l’intenzione di vietare la vendita di Flipper Zero e di dispositivi simili nel Paese perché avrebbero potuto essere utilizzati per rubare automobili.
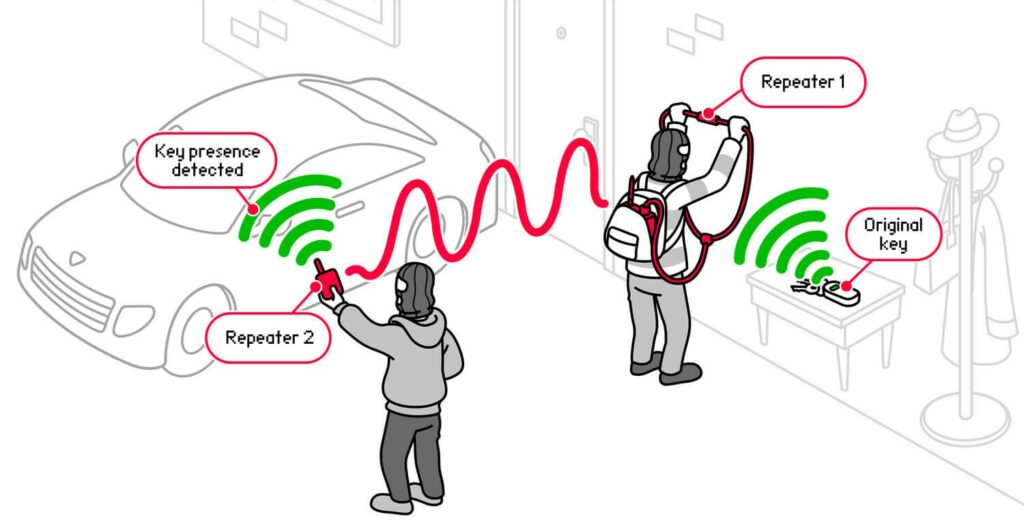
In particolare, ricorda che i veri ladri d’auto di solito prendono di mira i sistemi di apertura e avviamento senza chiave. Utilizzano ripetitori e trasmettitori che trasmettono un segnale dalla vera chiave, inducendo l’auto a credere che la vera chiave si trovi nelle vicinanze. “Se la tua auto può essere hackerata con Flipper Zero, può essere hackerata anche con un pezzo di filo“, conclude Zhovner.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…