
È stata individuato che la botnet GoBruteforcer, sta sfruttando una debolezza sorprendentemente attuale: il riutilizzo su larga scala di configurazioni server generate dall’intelligenza artificiale. Un’abitudine sempre più diffusa che, di fatto, sta lasciando decine di migliaia di sistemi esposti ad attacchi automatizzati.
Secondo un recente report di Check Point Research (CPR), nel 2025 la minaccia si è evoluta in modo significativo, prendendo di mira server Linux che ospitano servizi comuni come MySQL, FTP e phpMyAdmin.
Gli analisti stimano che oltre 50.000 server accessibili da Internet possano essere vulnerabili a questa nuova ondata, che combina tecniche di brute-force tradizionali con sofisticati meccanismi di evasione.
GoBruteforcer non utilizza direttamente l’intelligenza artificiale. Tuttavia, il suo successo è strettamente legato al modo in cui gli sviluppatori impiegano i Large Language Model (LLM). Molti di questi modelli, addestrati su documentazione pubblica e repository open source, tendono a suggerire configurazioni standard con credenziali deboli o prevedibili.
I ricercatori di Check Point lo dimostrano con un esempio concreto: chiedendo a due LLM differenti di generare una configurazione Docker per MySQL, entrambi hanno prodotto snippet quasi identici, con nomi utente predefiniti e facilmente indovinabili.
Questa prevedibilità è oro per gli operatori della botnet. Le liste di credenziali utilizzate da GoBruteforcer contengono infatti username comuni come appuser, myuser o appuser1234, permettendo agli attaccanti di aggirare con facilità le difese di server gestiti in modo superficiale.
Come sottolinea CPR, non è detto che la botnet prenda di mira deliberatamente installazioni create con l’AI, ma la diffusione incontrollata di configurazioni “copiate e incollate” rende gli attacchi molto più efficaci.
La campagna non ha solo finalità di espansione della botnet. Il movente è chiaramente economico. Gli analisti hanno osservato un interesse mirato verso database legati a progetti crypto e blockchain.
Su uno dei sistemi compromessi è stato scoperto un vero e proprio arsenale di strumenti per il furto di criptovalute: scanner TRON, utility per il token sweeping su TRON e BSC, e un file contenente circa 23.000 indirizzi TRON.
L’analisi delle transazioni on-chain ha confermato i sospetti peggiori: alcuni degli attacchi hanno effettivamente portato a guadagni concreti per gli operatori della botnet.
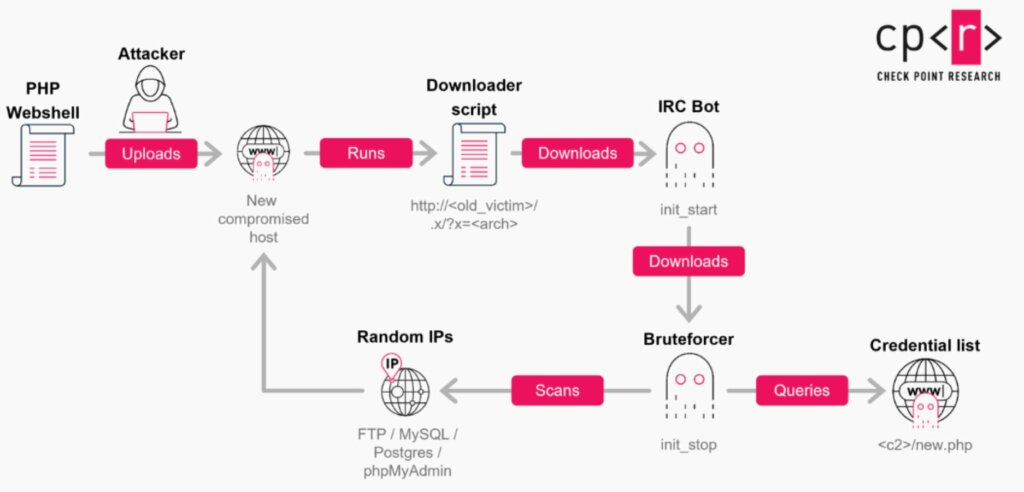
Individuata per la prima volta nel 2023, la versione 2025 di GoBruteforcer mostra un’evoluzione tecnica evidente. Il modulo IRC del bot, originariamente scritto in C, è stato completamente riscritto in Go e sottoposto a un forte processo di offuscamento.
Il malware utilizza ora tecniche di process masquerading per confondersi con i processi di sistema. Attraverso la chiamata prctl con l’operazione PR_SET_NAME, il processo può assumere nomi legittimi come init, rendendo più difficile la sua individuazione durante controlli superficiali.
GoBruteforcer non colpisce a caso. Il sistema di generazione degli indirizzi IP è progettato per evitare reti considerate “ad alto rischio”.
In particolare, il malware integra una blacklist di 13 blocchi /8 storicamente associati al Dipartimento della Difesa degli Stati Uniti, probabilmente per eludere honeypot governativi e ridurre la probabilità di attirare attenzioni indesiderate.
Allo stesso modo, i grandi provider cloud come AWS vengono spesso esclusi perché ritenuti ambienti ad alta sorveglianza, con team di risposta agli abusi particolarmente aggressivi.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.
