
Dopo un lungo periodo di silenzio, il malware downloader Gootloader è tornato alla ribalta.
Lo scorso novembre il team di Huntress ha rilevato una nuova campagna che indicava il ritorno di uno sviluppatore precedentemente associato al gruppo Vanilla Tempest. All’epoca, questo gruppo utilizzava il ransomware Rhysida.
L’analisi dei nuovi campioni di Gootloade svolta da Expel ha rivelato che l’autore è tornato al suo precedente ruolo di fornitore di accesso iniziale, ma si è affidato a tecniche di mimetizzazione migliorate. Il ritorno del malware è stato accompagnato da tattiche aggiornate che ne rendono più difficile il rilevamento.
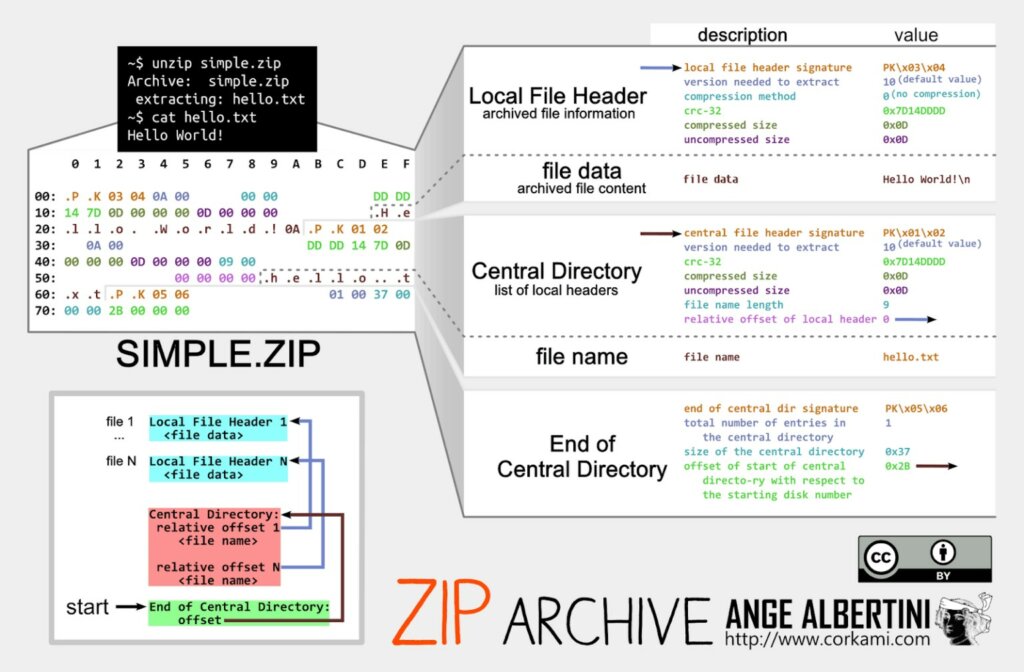
La caratteristica principale del nuovo approccio è l’utilizzo di un insolito archivio ZIP, che a prima vista sembra corrotto. Tuttavia, questa tecnica consente agli aggressori di aggirare l’analisi automatica e di nascondersi dalle soluzioni antivirus, pur riuscendo a eseguire malware sui sistemi delle vittime.
Il meccanismo di distribuzione di Gootloader rimane lo stesso: l’infezione inizia con un file JScript compresso in un archivio ZIP. L’apertura del file avvia PowerShell, che stabilisce una presenza dannosa nel sistema. Ma è il formato dell’archivio ZIP a rendere questa campagna particolarmente degna di nota. Gli archivi contengono centinaia di file ZIP concatenati tra loro: questo è possibile perché la decompressione inizia alla fine del file. Il numero di questi frammenti varia e ogni archivio scaricato è univoco, eliminando la possibilità di rilevamento tramite hash.
L’archivio viola anche le specifiche ZIP: la sua struttura manca dei byte richiesti alla fine della directory e alcuni campi, come il numero del disco o la data di modifica, sono riempiti con valori casuali. Questo impedisce il corretto funzionamento di strumenti come 7-Zip o WinRAR, ma non influisce sullo strumento di decompressione integrato di Windows. Pertanto, il file dannoso rimane eseguibile dall’utente, ma è inaccessibile alla maggior parte dei sistemi di analisi automatica.
La metodologia dello sviluppatore di Gootloader è incentrata sulla furtività. Grazie al file ZIP “falso” e al contenuto univoco ogni volta, il codice dannoso è difficile da rilevare con gli strumenti standard. Persino il file JScript è camuffato da innocuo: contiene migliaia di righe di codice innocuo, tra cui sono nascoste istruzioni dannose.
Il programma si avvia direttamente dalla cartella temporanea di Windows, poiché il file non viene estratto manualmente dall’utente. Questo crea un’opportunità di rilevamento: ad esempio, è possibile tracciare l’avvio di “wscript.exe” dalla directory AppDataLocalTemp. Un altro indicatore è la presenza di file LNK nella cartella di avvio, che fanno riferimento a script in posizioni non standard.
Vale anche la pena notare il metodo utilizzato per eseguire la seconda fase dell’infezione. Il malware utilizza il vecchio formato di file breve NTFS, una rarità nei sistemi moderni e può fungere da ulteriore indicatore. Inoltre, all’avvio, viene osservata una catena di processi: da CScript a PowerShell e oltre, che può essere utilizzata anche per il rilevamento.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…