
Il team AI Research (STAR) di Straiker ha individuato Villager, un framework di penetration testing nativo basato sull’intelligenza artificiale, sviluppato dal gruppo cinese Cyberspike. Lo strumento, presentato come soluzione red team, è progettato per automatizzare in modo completo le attività di test di sicurezza, combinando tool di Kali Linux e modelli AI DeepSeek tramite protocollo MCP.
Villager è stato pubblicato sul Python Package Index (PyPI.org) ed è liberamente accessibile a livello globale. Nei primi due mesi dalla pubblicazione ha superato i 10.000 download, un dato che ha attirato l’attenzione degli analisti per il potenziale rischio di abuso.
Secondo Straiker, la combinazione tra automazione avanzata e bassa barriera di accesso potrebbe portare Villager a seguire una traiettoria simile a quella di strumenti come Cobalt Strike, nati per usi legittimi ma successivamente adottati su larga scala da attori malevoli.
Villager riduce drasticamente il livello di competenza necessario per condurre attività offensive complesse. Automatizzando l’intera catena di strumenti di penetration testing, consente anche a operatori meno esperti di eseguire intrusioni avanzate.
La distribuzione attraverso PyPI rappresenta inoltre un potenziale vettore di supply chain, offrendo agli attaccanti un canale affidabile per ottenere e integrare lo strumento nei propri flussi operativi.
Dal punto di vista operativo, l’uso improprio di Villager potrebbe tradursi in un aumento significativo delle attività automatizzate di scansione, sfruttamento e post-exploitation, con un conseguente aggravio per i team di rilevamento e risposta agli incidenti.
Il protocollo MCP (Model Context Protocol) è uno standard pensato per consentire ai modelli di intelligenza artificiale di interagire in modo strutturato con strumenti esterni, servizi e risorse di sistema. A differenza di una semplice API di inferenza, MCP definisce un meccanismo attraverso il quale l’AI può ricevere contesto operativo, comprendere quali strumenti sono disponibili e invocarli in modo controllato. Questo trasforma il modello da motore puramente conversazionale a componente attivo all’interno di flussi di lavoro complessi.
Dal punto di vista tecnico, MCP introduce un livello di orchestrazione che regola lo scambio di messaggi tra il modello e i cosiddetti “tool”, come ambienti di esecuzione, container, browser automatizzati o utility di sistema. Ogni azione viene descritta e restituita in un formato strutturato, permettendo all’AI di concatenare più operazioni, gestire dipendenze tra task e reagire agli errori. In questo modo è possibile costruire agenti che pianificano, eseguono e verificano attività articolate, mantenendo coerenza e tracciabilità.
Il valore – e al tempo stesso il rischio – di MCP emerge quando viene applicato in contesti sensibili come la sicurezza informatica. Collegando modelli linguistici a strumenti offensivi o di test, il protocollo consente l’automazione di intere catene operative, riducendo drasticamente l’intervento umano. Per questo MCP è considerato una tecnologia abilitante: da un lato rende più efficienti sviluppo, testing e difesa, dall’altro può essere sfruttato per creare framework di attacco autonomi, come nel caso di Villager.
Le imprese potrebbero trovarsi di fronte a un incremento di tentativi di scansione ed exploit provenienti dall’esterno, a cicli di attacco più rapidi che riducono le finestre di reazione e a una maggiore difficoltà di attribuzione, dovuta all’uso di strumenti standard in campagne ibride.
Ulteriori rischi riguardano la supply chain e gli ambienti di sviluppo, qualora il pacchetto venga installato su workstation CI/CD o sistemi di test.
Gli analisti suggeriscono di implementare gateway di sicurezza per il protocollo MCP, capaci di ispezionare e filtrare in tempo reale le comunicazioni tra agenti AI e strumenti. È inoltre consigliata una revisione approfondita delle integrazioni AI di terze parti, l’adozione di policy di governance sull’uso dell’intelligenza artificiale e lo sviluppo di capacità di threat intelligence focalizzate sugli attacchi AI-driven.
Tra le misure indicate figurano anche la definizione di procedure di risposta specifiche per incidenti potenziati dall’AI e l’esecuzione di test di sicurezza continui, mirati alle applicazioni abilitate MCP.
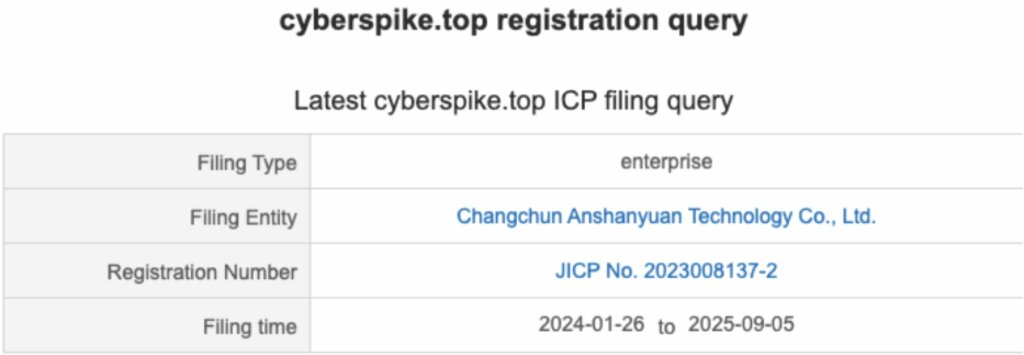
Cyberspike, riportano i ricercatori di Striker, emerge per la prima volta il 27 novembre 2023, con la registrazione del dominio cyberspike[.]top associato alla Changchun Anshanyuan Technology Co., Ltd., società cinese indicata come fornitore di soluzioni AI e software applicativo.
Tuttavia, l’assenza di un sito web aziendale attivo e di una presenza commerciale verificabile solleva interrogativi sulla reale struttura dell’organizzazione.
Snapshot archiviati dalla Wayback Machine mostrano che nel 2023 l’azienda promuoveva un prodotto denominato Cyberspike, dotato di dashboard per il monitoraggio delle macchine compromesse.
Le funzionalità dichiarate includevano proxy inverso, generatori multistadio e strumenti tipici delle piattaforme di comando e controllo.
L’analisi del Cyberspike Studio Installer v1.1.7, caricato su VirusTotal il 10 dicembre 2023, ha rivelato che i plugin inclusi corrispondono a un Remote Access Trojan (RAT) completo. Le capacità individuate comprendono accesso remoto al desktop, keylogging, compromissione di account Discord, controllo della webcam e altre funzioni di sorveglianza.
Ulteriori verifiche hanno dimostrato che l’intera suite Cyberspike coincide con la versione 1.0.7.0 di AsyncRAT, malware noto e diffuso dal 2019, da cui derivano anche varianti come DCRat e VenomRAT.
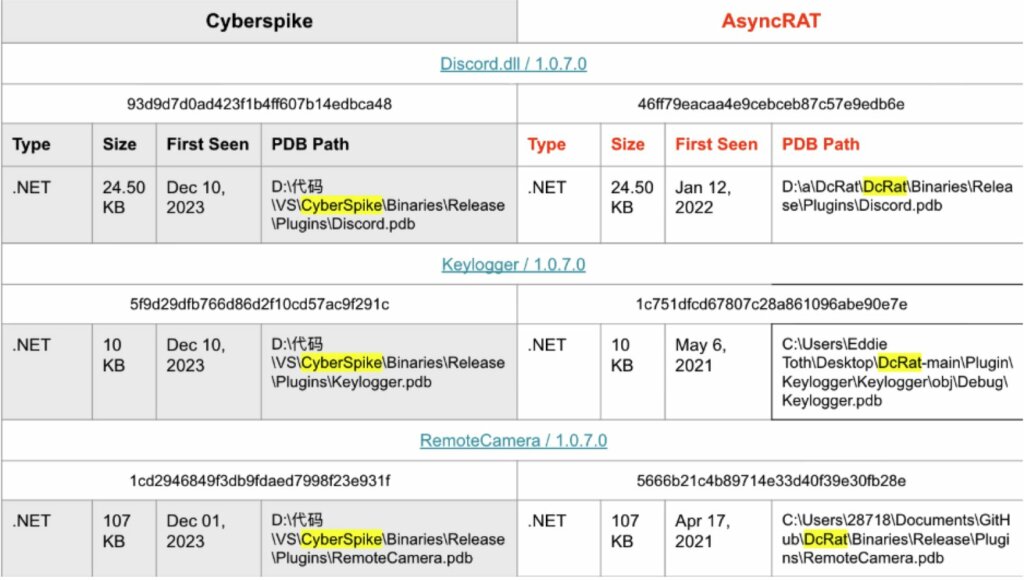
I componenti analizzati risultano identici per formato, dimensione e linguaggio di programmazione, confermando l’integrazione diretta di AsyncRAT nel prodotto Cyberspike, insieme a plugin aggiuntivi come Mimikatz.
Il 23 luglio 2025 Cyberspike ha pubblicato Villager Pentesting Tool su PyPI. Il pacchetto automatizza i test di sicurezza utilizzando modelli DeepSeek e include riferimenti a un modello personalizzato denominato “al-1s-20250421”, ospitato su infrastrutture cyberspike[.]top.
L’autore indicato, @stupidfish001, è un ex partecipante a competizioni CTF del team cinese HSCSEC e risulta manutentore di diversi progetti correlati.
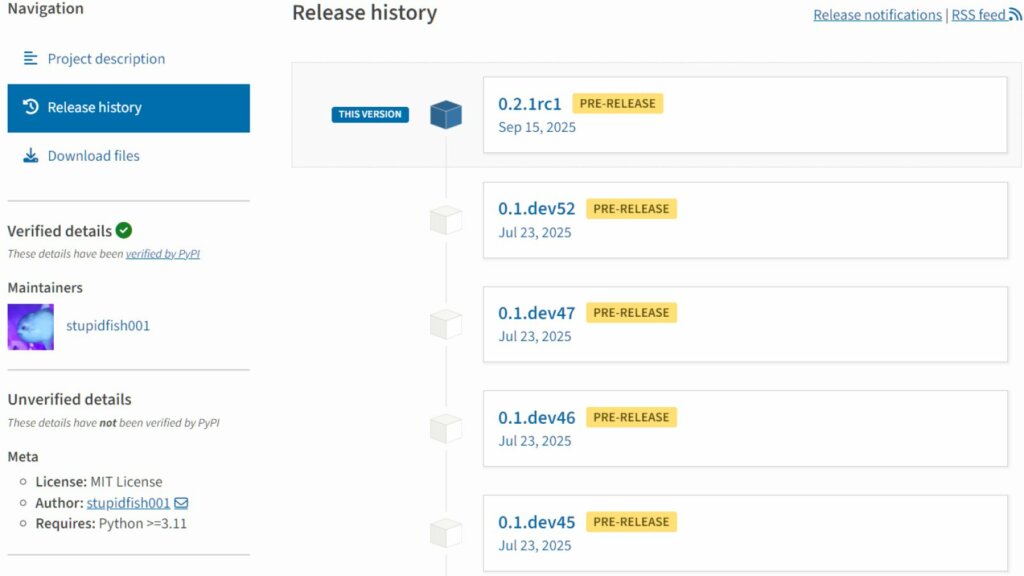
Nei due mesi successivi al rilascio, Villager ha totalizzato 10.030 download su Linux, macOS e Windows, con una media di oltre 200 download ogni tre giorni.
Villager adotta un’architettura distribuita basata su MCP, con servizi dedicati al coordinamento dei messaggi, alla generazione di exploit tramite RAG (Retrieval-Augmented Generation) e alla creazione automatica di container Kali Linux on-demand. L’orchestrazione si basa su Pydantic AI, che impone formati strutturati agli output per garantire coerenza operativa.
Un elemento critico è rappresentato dai meccanismi di evasione forense: i container sono progettati per autodistruggersi, cancellando log e tracce, e utilizzano porte SSH randomizzate, rendendo più complessa l’analisi post-incidente.
A differenza dei framework tradizionali basati su script, Villager consente l’interazione in linguaggio naturale. I comandi testuali vengono tradotti automaticamente in sequenze di attacco dinamiche grazie all’integrazione con LangChain e DeepSeek v3, accessibile tramite API compatibili con OpenAI.
Il sistema di comando e controllo si basa su FastAPI e su una gestione avanzata delle attività. Obiettivi complessi vengono scomposti in sotto-task, eseguiti anche in parallelo, con monitoraggio continuo dello stato e capacità di recupero automatico in caso di errore. Questo approccio consente una pianificazione adattiva dell’attacco lungo l’intera kill chain.
In uno scenario di test applicativo web, Villager può identificare tecnologie, eseguire scansioni mirate e sfruttare vulnerabilità in modo adattivo.
In contesti più complessi, il framework è in grado di coordinare automazione del browser, generazione di payload, monitoraggio del traffico di rete e persistenza post-exploit, senza ricorrere a playbook statici.
Villager rappresenta un’evoluzione significativa nel panorama degli strumenti di attacco basati sull’intelligenza artificiale.
La sua capacità di orchestrare dinamicamente più vettori offensivi, riducendo al minimo l’intervento umano, abbassa ulteriormente la soglia tecnica per condurre operazioni complesse.
La presenza attiva del framework su piattaforme come VirusTotal conferma che gli attacchi AI-driven non sono più teorici. L’uso del protocollo MCP come ponte tra modelli linguistici e strumenti offensivi introduce un paradigma destinato a influenzare lo sviluppo dei malware futuri, contribuendo alla diffusione delle cosiddette AiPT, le minacce persistenti basate su agenti di intelligenza artificiale.
Ti è piaciuto questo articolo? Ne stiamo discutendo nella nostra Community su LinkedIn, Facebook e Instagram. Seguici anche su Google News, per ricevere aggiornamenti quotidiani sulla sicurezza informatica o Scrivici se desideri segnalarci notizie, approfondimenti o contributi da pubblicare.

 Cybercrime
CybercrimeLe autorità tedesche hanno recentemente lanciato un avviso riguardante una sofisticata campagna di phishing che prende di mira gli utenti di Signal in Germania e nel resto d’Europa. L’attacco si concentra su profili specifici, tra…
 Innovazione
InnovazioneL’evoluzione dell’Intelligenza Artificiale ha superato una nuova, inquietante frontiera. Se fino a ieri parlavamo di algoritmi confinati dietro uno schermo, oggi ci troviamo di fronte al concetto di “Meatspace Layer”: un’infrastruttura dove le macchine non…
 Cybercrime
CybercrimeNegli ultimi anni, la sicurezza delle reti ha affrontato minacce sempre più sofisticate, capaci di aggirare le difese tradizionali e di penetrare negli strati più profondi delle infrastrutture. Un’analisi recente ha portato alla luce uno…
 Vulnerabilità
VulnerabilitàNegli ultimi tempi, la piattaforma di automazione n8n sta affrontando una serie crescente di bug di sicurezza. n8n è una piattaforma di automazione che trasforma task complessi in operazioni semplici e veloci. Con pochi click…
 Innovazione
InnovazioneArticolo scritto con la collaborazione di Giovanni Pollola. Per anni, “IA a bordo dei satelliti” serviva soprattutto a “ripulire” i dati: meno rumore nelle immagini e nei dati acquisiti attraverso i vari payload multisensoriali, meno…